Contents:
Industrial Spy ransomware gang has devised a new extortion strategy: it compromises corporate websites in order to publicly display ransom notifications.
The new technique is being employed by Industrial Spy, which is a data extortion organization that recently started using ransomware as part of its attacks.
In their attacks, the cybercrime group will hack into networks, steal information, and use ransomware to encrypt devices.
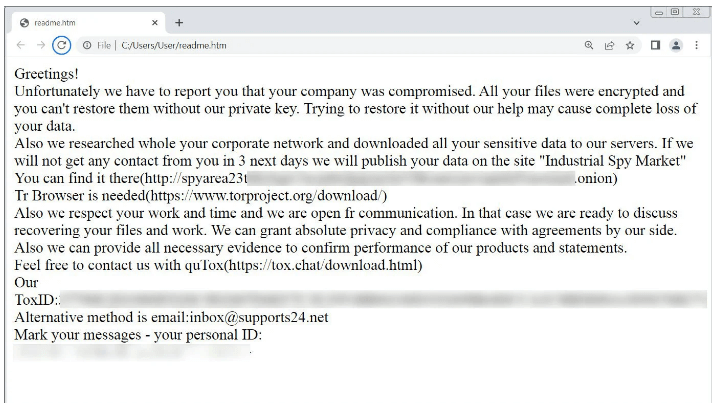
Yesterday, Industrial Spy started selling stolen information they say belongs to a French organization named SATT Sud-Est for $500,000.
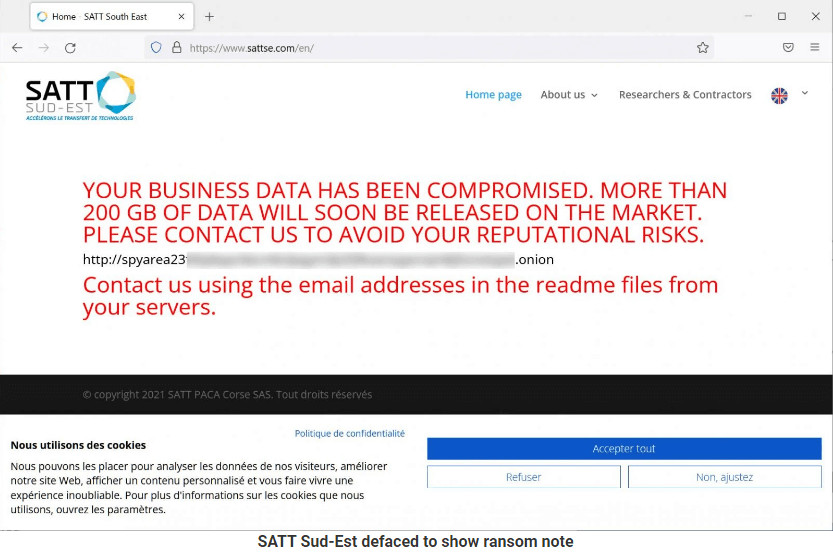
According to MalwareHunterTeam, this cyberattack is notable as the hackers also breached the organization’s website to show a note informing that 200GB had been snatched and would soon be available for sale unless the victim paid a ransom.
We already know that when such cybercrime groups extort money from their victims, they usually give them a limited amount of time (a couple of weeks) to negotiate and pay the requested ransom before making the stolen information public.
When the cybercriminals negotiate with the victims, they assure them that the ransomware attack will be kept a secret, that they will receive a decryption key, and all the stolen data will be deleted once they have received their money.
Following the negotiation process, the attackers will use different tactics to put even more pressure on the victims. They will:
- launch DDoS attacks on corporate websites,
- send emails to clients and business partners,
- call executives to threaten them.
All of these strategies are carried out in secret or with minimal public exposure on their data leak websites, which are typically only visited by cybersecurity experts and the media.
Nevertheless, for the first time, a ransomware organization is seen destroying a website in order to publicly display a ransom message.
While this strategy is unusual, it empowers the ransomware group to put even more pressure on a victim by bringing the attack into the open, where customers and business partners can see it.
It’s hard to believe that this novel strategy will catch on because web servers are usually held with hosting companies rather than on corporate networks. So, cybercriminals would have to exploit a website weakness or obtain access to credentials when they steal information from internal networks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








