Contents:
Health applications are very popular nowadays. For example, most people have smartwatches to help them track their physical progress when it comes to improving health conditions. Thus, accessing users’ personal data is self-explanatory. But where is the limit? Researchers from Macquarie University, Australia’s public research university, have recently discovered that health apps data oversharing is becoming a real threat to data privacy. 88 percent of the free targeted apps in Google Play are subject to the access and big sharing of personal data, easy prey in the hands of threat actors.
Health Apps Data Oversharing: Why Are Health Apps So Popular, Yet Insecure?
Health apps are basically storage locations of all your health-related data, for example: sleep info, the number of taken steps and calories in a day, blood pressure, level of glucose in your body, nutrition data, menstruation information, symptom checking, and so on. As with any other application, they are intended to simplify one’s life. But is simplicity bonded to online safety?
The researchers from Macquarie University have discovered and stated in a report published by BMJ that these types of applications do not keep your data secure, and they can be exposed and shared with third parties, thus leading to health apps data oversharing. The main reasons are user data sharing and subscription selling business model, privacy standards not being properly carried out, and the access to sensitive info.
What Do Statistics Say?
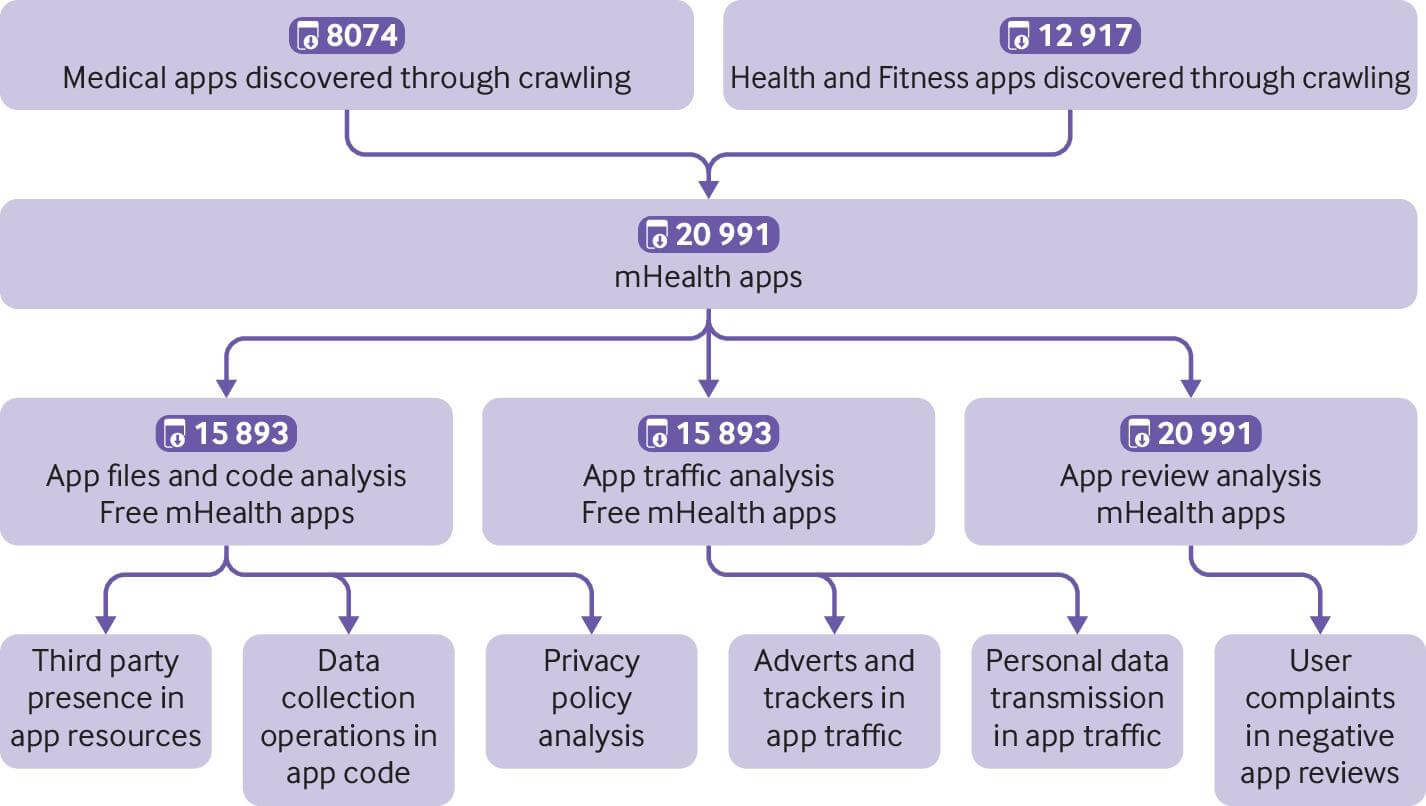
The main focus of the study was Android-designed health applications found in Google play with free access for users.
According to ZDNet, here is how the statistics look like:
- Out of 2.8 million on Google Play and 1.96 million on the Apple Store, only 99,000 applications relate to health and fitness categories.
- 88% of the 15,000 free tested applications in Google Play could gain access to users’ private data and share them.
- The transmission of data was made, however, only by 4% of the targeted apps, this specifically means the share of user’s name and location.
- 4 data gathering operations per app on average: 65,068 in total.
- 616 different apps were transmitting 3,148 communications of users’ data based on the traffic analysis.
- Third-party services covered 56% of users’ data transmissions and 87.5 % of data collection.
- They also identified 665 unique third-party entities and 23% of data communication was made on unreliable channels.
- Last, but not least: a privacy policy text was not provided by 28% of the investigated apps (5903) and non-compliance with privacy policy rules was performed by 25% of the apps.
What Generated These Numbers and What Data Is Actually Being Collected?
The researchers focused, as stated in the BMJ report, on some main topics, which helped them come to the above results. The analysis of app reviews supported experts in distinguishing between positive and negative reviews with a rate of 83.9% positive ones.
The investigation of the security level of data transmission made clear that HTTPS protocol is mandatory in these times and the traffic analysis led to the identification of collected data categories such as users’ IMSI (international mobile subscriber identity), MAC address, IMEI, location, and contact details.
The study on adverts and tracking revealed that more than half of the transmitted data was on behalf of third-party services. Out of unique third-party providers, Google, Facebook, and YouTube were the main ones that collected privacy info.
Thus, users should pay more attention to data collection:
Our results show that the collection of personal user information is a pervasive practice in mHealth apps, and not always transparent and secure. Patients should be informed on the privacy practices of these apps and the associated privacy risks before installation and use. Clinicians should understand the main privacy aspects of mHealth apps in their specialist area, along with their key functionalities, and be able to articulate these to patients in lay language.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security