Contents:
Over the last few weeks, a new phishing operation focusing on e-banking users from Germany has been in progress, using QR codes during the credential-stealing operation.
As explained by BleepingComputer, the cybercriminals behind this phishing campaign employ a variety of techniques to get through security measures and persuade their victims to read the emails and act in accordance with the instructions.
Cofense security experts sampled many of these messages and meticulously detailed the attackers’ methods in their analysis.
More About the Phishing Campaign
According to the researchers, the messages have been attentively created, including financial institution logos, well-structured information, and a generally consistent style.
The phishing emails’ subjects range from requesting the user’s approval regarding the bank’s data policy modifications to asking that they review new security measures.
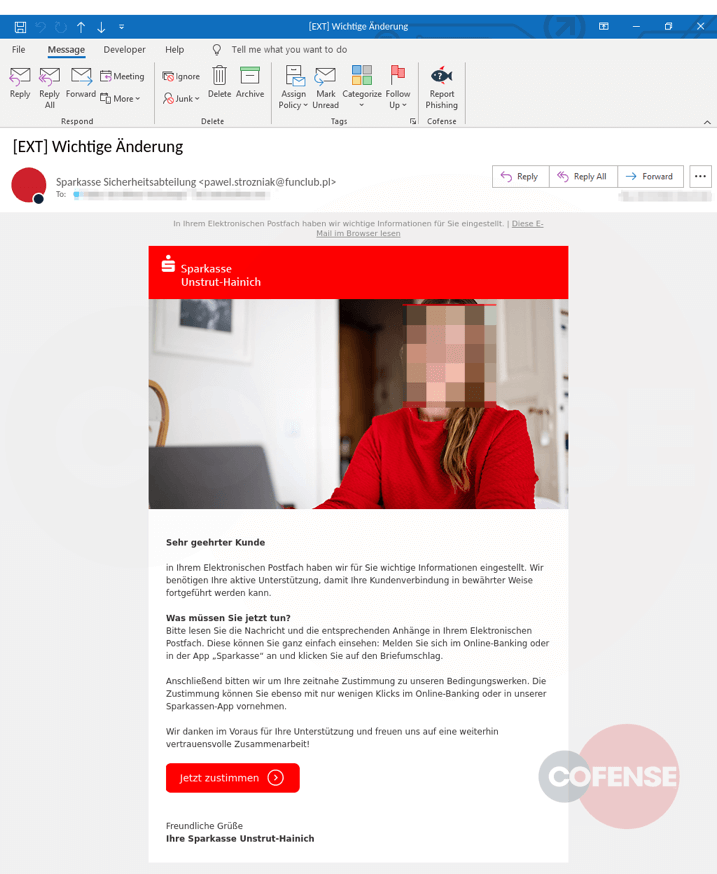
This method demonstrates thorough planning, as the cybercriminals do not make the usual exaggerated claims of account exposure and do not inform the victim of a potential crisis.
As explained by BleepingComputer, when the targets click on the embedded button, they land on the phishing website after navigating through Google’s feed proxy service ‘FeedBurner.’
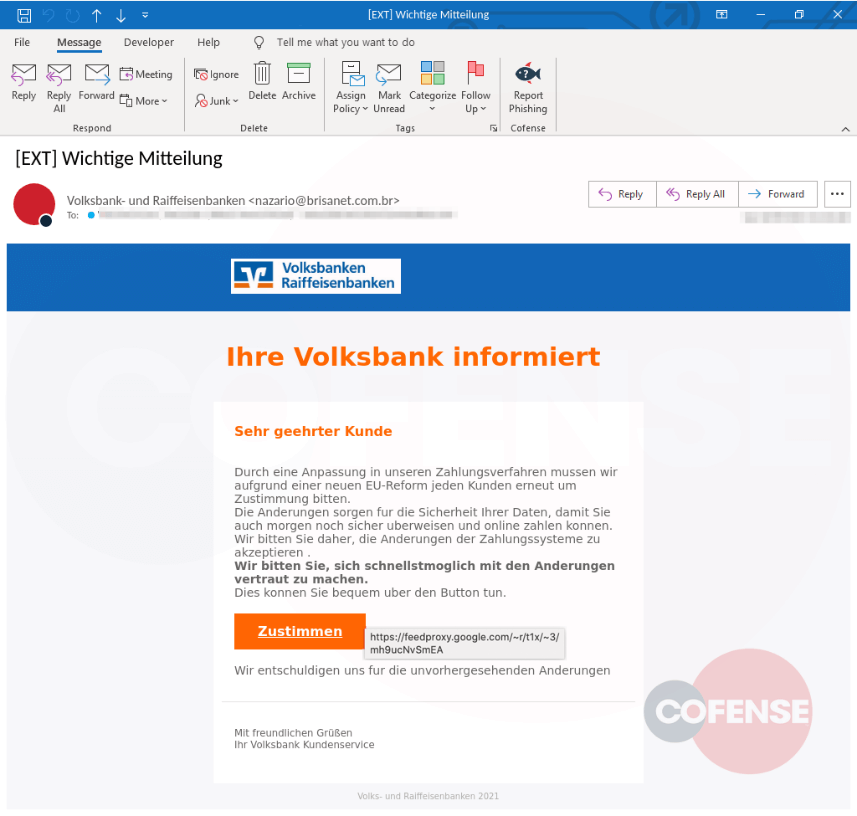
Furthermore, the attackers register their custom domains, which are utilized for both the re-directions and the phishing websites. By doing this, threat actors plan to deceive email and internet security systems into not raising any suspicions during the phishing operation.
The domains are newly registered sites on the REG.RU Russian registrar and follow a standard URL structure depending on the targeted bank.
New Techniques
In the latest phishing attacks, cybercriminals utilize QR codes rather than buttons to direct their targets to malicious websites.
These email messages do not contain clear-text URLs but instead use QR codes to obfuscate them, making it more difficult for security tools to identify them.
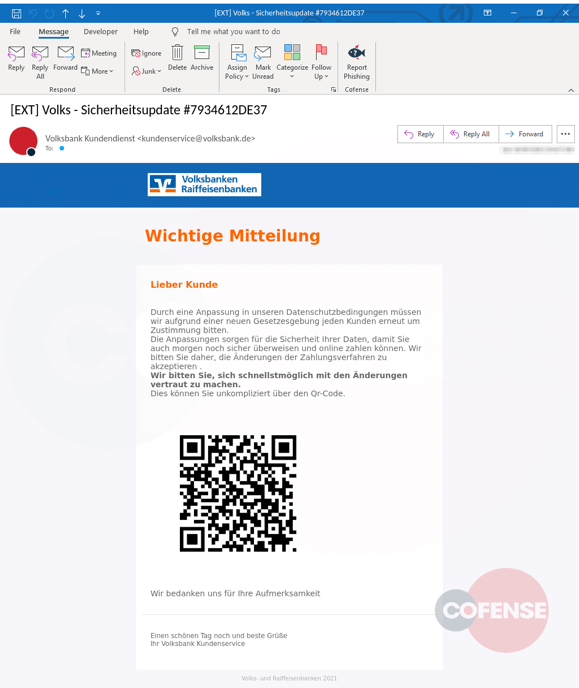
When the user visits the phishing webpage, they are prompted to disclose the location of their bank, their code, username, and PIN.
After the victims enter this information on the fake website, they are validated and then urged to enter their login information again because they are erroneous.
You might wonder about the request to re-enter the credentials. Well, this is a frequent quality strategy used in phishing attacks to remove typing errors when the victim enters their credentials the first time.
Users are advised to avoid clicking on buttons, URLs, and QR codes that lead to an external website, regardless of how authentic an email appears to be.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal™ Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










