Contents:
The OpenSea NFT platform could be a new target in the hands of hackers. As per a new discovery, cybercriminals use malicious NFT art as bait, thus determining users to click on it. What this will do is empty their crypto wallets. This would be possible because of an OpenSea bug that might allow threat actors to engage in account hijacking.
The OpenSea Bug: Detailing the Issue
As BleepingComputer explains, an attack might happen like this: cybercriminals develop an NFT that contains a compromised payload, then they wait for users to discover it.
A common method, known as “airdropping”, has the role to bring to users’ attention new assets, so many of them reported earning such gifts that came from the OpenSea marketplace, and then, puf, their crypto wallets were emptied.
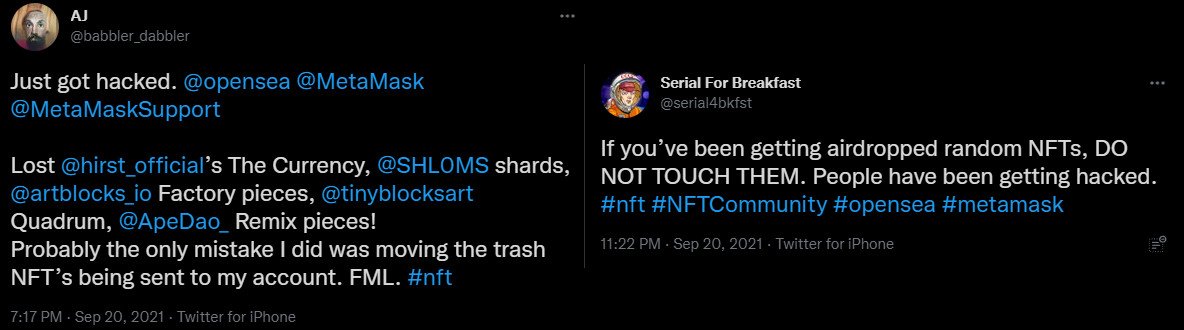
Researchers Investigate the OpenSea Bug
Getting to know these issues, CheckPoint’s experts decided to investigate the OpenSea platform to see where the flaws lie. First of all, one has to own an OpenSea account. That’s why the experts under discussion chose MetaMask which is basically a third-party wallet present on the platform’s list. You have to choose one wallet from that list to create an OpenSea account.
Since the OpenSea platform works as a selling channel of digital art (files up to 40MB and with extension like JPG, PNG, GIF, etc.), what the researchers did to further develop their investigation was to upload there an image with the SVG extension. This was embedded with malicious JavaScript code. Clicking on it led to a new tab and then to ‘storage.opensea.io’ subdomain under which the file execution was permitted.
What’s more, the SVG image was complemented by an iFrame. This had the role of HTML code uploading whose final target was the injection of “window.ethereum”. What this “window.ethereum” does is to ensure the victim’s communication with the Ethereum wallet.
In our attack scenario, the user is asked to sign with their wallet after clicking an image received from a third party, which is unexpected behavior on OpenSea, since it does not correlate to services provided by the OpenSea platform, like buying an item, making an offer, or favoring an item,” CPR says. “However, since the transaction operation domain is from OpenSea itself, and since this is an action the victim usually gets in other NFT operations, it may lead them to approve the connection.
Then the Ethereum RPC-API could be used for abusing the wallet’s range of capabilities. This triggered the communication with MetaMask, then a pop-up was displayed that requested wallet connection. Of course, only a true user could have legitimate interaction with that pop-up that was real, so cyber criminals needed to find a way to make the user be part of the scheme. Users also needed to fill out a signature in a specific pop-up in order to let the transaction happen and give hackers access to their wallets.
The two elements that make the attack successful are these: the domain of the transaction comes from the OpenSea platform and users are required to perform an action that is not unfamiliar, so nothing seems strange for them. And this is how a compromised NFT can be the path to account hijacking.
As the experts’ report summarizes, the attack will unfold like this:
Step 1 – the creation of the malicious NFT art by the hacker and the victim receives it as a gift;
Step 2 – the bad NFT is seen by the target, an OpenSea domain storage pop-up appears. This pop-up asks for a connection to the wallet;
Step 3 – victims will connect to their wallet to see what’s that gift about;
Step 4 – after connection, another pop-up is sent by the hackers requiring a transaction the users will approve without paying enough attention;
Step 5 – hackers have what’s in the crypto wallet.
What OpenSea Said About It
The researchers who tested this OpenSea Bug informed the company about it and the company’s answer followed the notification:
Security is fundamental to OpenSea. We appreciate the CPR team bringing this vulnerability to our attention and collaborating with us as we investigated the matter and implemented a fix within an hour of it being brought to our attention. These attacks would have relied on users approving malicious activity through a third-party wallet provider by connecting their wallet and providing a signature for the malicious transaction. We have been unable to identify any instances where this vulnerability was exploited but are coordinating directly with third-party wallets that integrate with our platform on how to help users better identify malicious signature requests, as well as other initiatives to help users thwart scams and phishing attacks with greater efficacy.
The only mitigation measure that could be working for now is up to the users’s vigilance, as these should avoid automatically approving or performing whatever action a pop-up requires without having a closer look at it.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










