Contents:
We know you are tired of reading about ransomware attacks, ransoms, and impacted organizations every single day, that’s why we are so glad to tell you the good news of the day: victims of BlackByte ransomware can now decrypt and get back their files as a free decryption tool has just been made public.
As explained in this article, ransomware is a sophisticated piece of malware (malicious software) that encrypts all the data on a victim’s PC or mobile device, blocking the data owner’s access to it.
After the infection happens, the victims receive a message telling them that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Normally, there is also a time limit for the payment to be completed, otherwise, the files could be lost forever.
A Quick Look Into BlackByte Ransomware
Just like its other ransomware fellows, BlackByte targets its victim’s files by applying encryption to them. Afterward, the BlackByte ransomware victims usually receive a ransom note on their computer screen, which says that they have to pay a ransom in order to have their files decrypted.
According to BleepingComputer, this ransomware began attacking corporate victims all over the world a few months ago. The ransomware was first reported this summer in the tech news website forums when its victims looked for assistance in decrypting their files.
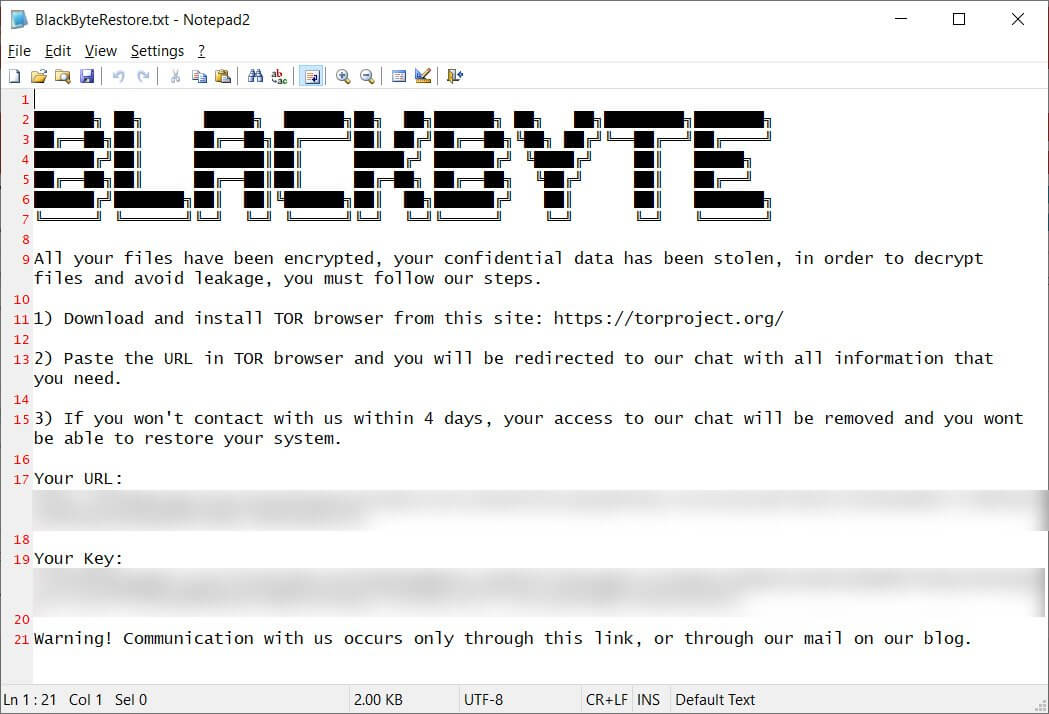
BlackByte M.O.
According to a Trustwave study, the ransomware was downloading a file called ‘forest.png’ from a remote site under their control. This file is named to look like it is an image file, but it holds the AES encryption key utilized to encrypt a machine.
As noticed by BleepingComputer, because BlackByte ransomware employs AES symmetrical encryption, the same key is used for file encryption and decryption.
While BlackByte also encrypts this downloaded AES encryption key and adds it to the ransom message, security experts at Trustwave have found that the ransomware threat actor was reusing the same forest.png file for numerous targets.
Trustwave was able to use the same ‘raw’ encryption key to create a decryptor that retrieves a victim’s files for free.
To decrypt a file, one only needs the raw key to be downloaded from the host. As long as the .PNG file it downloaded remains the same, we can use the same key to decrypt the encrypted files.
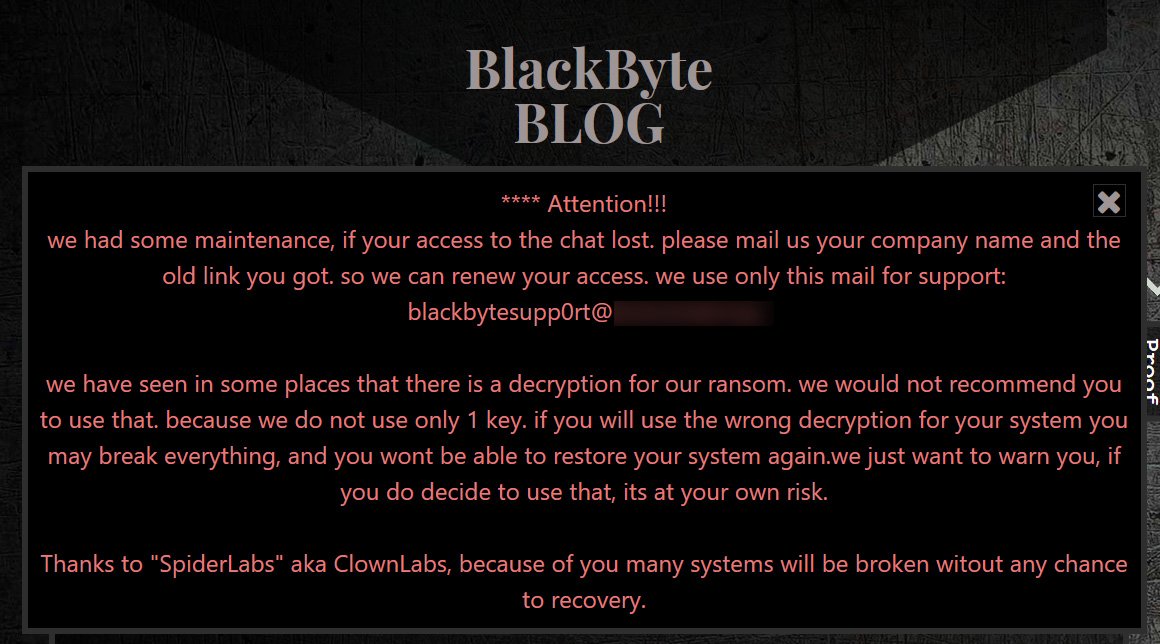
When the BlackByte ransomware gang became aware of the Trustwave’s report and decryption tool, they cautioned that they had used multiple keys and that using the decryptor with the wrong key might damage the victim’s files.
They stated:
we have seen in some places that there is a decryption for our ransom. we would not recommend you to use that. because we do not use only 1 key. if you will use the wrong decryption for your system you may break everything, and you wont be able to restore your system again. we just want to warn you, if you do decide to use that, its at your own risk.
The BlackByte decryptor that Trustwave has released can be downloaded from GitHub. Victims are advised to backup files before trying to decrypt them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










