Contents:
The Glitch platform has become a target for phishing hackers. It seems that the service is being actively abused by cybercriminals with the goal to host on this platform for free phishing sites that perform credentials theft. The ones targeted are employees of big enterprises, companies collaborating with the Middle East.
How the Abuse of the Glitch Platform Works
DomainTools researchers published a report on this topic. According to them, the phishing campaign was started back in July 2021, being still in progress.
The threat actors operate like this:
- They avoid antivirus alerts by sending e-mail messages with PDF-based attachments without any malicious code within;
- What can be found instead in these PDFs is a specific link;
- This link will lead to a malicious website that is hosted on the Glitch platform;
- Then, a landing page will be displayed;
- Researchers have identified many PDFs of this kind in a number of 70;
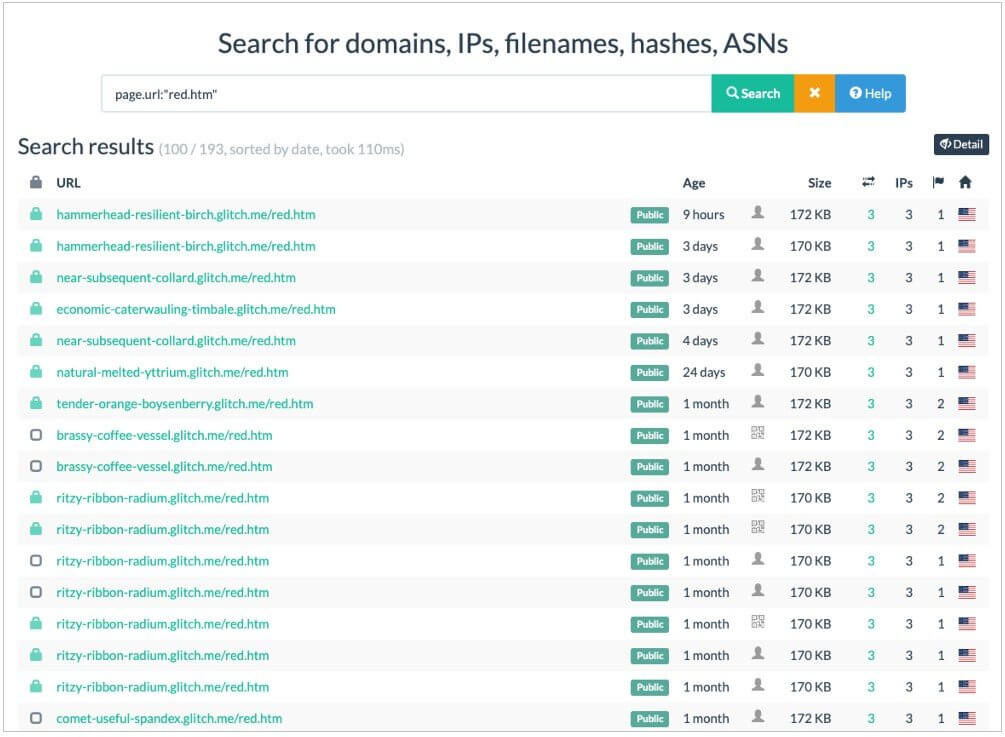
- The particularities about these PDFs were the unique URL and the e-mail correlated with each of them. All this links are related to different “red.htm” pages hosted by Glitch.
- An example of an URL that can be found in this kind of PDF document, according to the report, would be: https://spot-truthful-patio[.]glitch.me/red.htm#%20test@test.com
Here is also a list with the websites where those PDFs were directing users:
Why Is the Glitch Platform Vulnerable?
Glitch stands basically for a cloud-based hosting solution. People can use Node.js, React, or various dev platforms in order to perform apps and websites deployment.
Where’s the weak spot? As BleepingComputer mentions, the thing that makes the Glitch platform vulnerable to phishing attacks seems to be their free version through which users can build an app or a page. They can also let it live on the web for a period of 5 minutes. After the 5 minutes expire, this should be enabled manually by the user.
What makes the perfect combo for threat actors are some factors like the fact that Glitch’s domains are treated favorably by security tools due to the platform’s credibility and the free version that is a path for threat actors to host there short-lived malicious URLs.
Researches Expanded Their Analysis
Going further with their research, the experts’ team identified a Glitch website associated with a service of commercial malware sandbox. This included a phishing login page screenshot of Microsoft SharePoint.
The discovery of the PDF through which the researchers were directed to that website led to the identification of various HTLM documents linked to that sample after it was submitted to Virus Total. Obfuscated JavaScript could be found after the pages were pulled. These code chunks went through those malicious Worpress sites and then were used for credentials exfiltration purposes.
Glitch was informed by the researchers about this matter, but no response has come yet from the company.
How Can Heimdal™ Help?
Phishing e-mails with malicious attachments are so often nowadays. Threat actors are using more and more advanced social engineering techniques to lure users into clicking on a compromised link or downloading a compromised file. You might sometimes need a traffic filter tool instead of an e-mail security one in order to identify malicious URLs, as phishing gets more and more complex. Our awarded Heimdal™ Threat Prevention helps with a 96 % accuracy to prevent future threats at the domain level.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










