Contents:
Cybercriminals distribute the Gh0stCringe Remote Access Trojan (RAT) on exposed machines by attacking poorly protected Microsoft SQL and MySQL database servers.
Researchers from cybersecurity company AhnLab detailed in a report issued yesterday how the operators behind GhostCringe are aiming at poorly managed database servers with inadequate account credentials and no oversight.
According to BleepingComputer, attackers hack the database servers and write the malicious’mcsql.exe’ executable to disk using the mysqld.exe, mysqld-nt.exe, and sqlserver.exe processes.
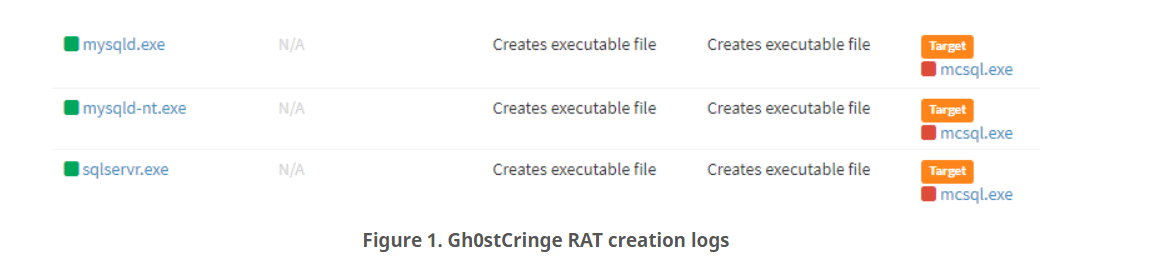
Aside from Gh0stCringe, AhnLab’s notes in its report the existence of various malware samples on the analyzed servers, implying that competing cybercriminals are hacking the same servers to drop payloads for their own operations.
Since database servers with vulnerable account credentials usually become targets of various attackers and malware, many different malware infection logs were found.
Gh0stCringe RAT is a dangerous malware that connects to the C&C server in order to receive custom commands or exfiltrate stolen data to the attackers. The threat actor can configure numerous settings to Gh0stCringe just like other Remote Access Trojan (RAT) malware.
As per AhnLab report, there are 7 settings, and the malware behaves differently depending on the data that has been configured:
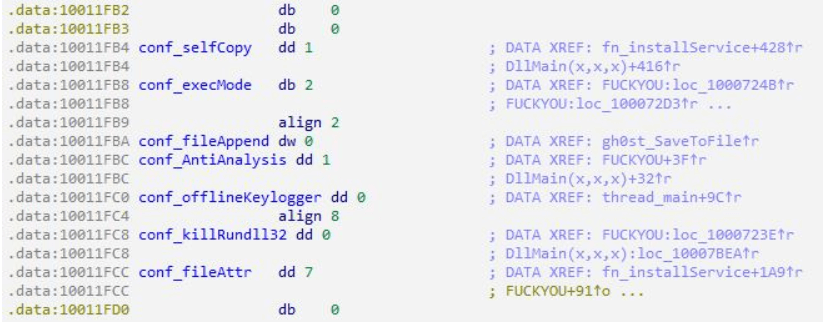
- Self-copy [On/Off]: If turned on, copies itself to a certain path depending on the mode.
- Mode of execution [Mode]: Can have values of 0, 1, and 2. See below for explanations on the modes.
- File size change [Size]: In Mode #2, the malware copies itself to the path ‘%ProgramFiles%\Cccogae.exe’, and if there is a set value, it adds junk data of the designated size to the back of the file.
- Analysis disruption technique [On/Off]: Obtains the PID of its parent process and the explorer.exe process. If it results in a value of 0, terminates itself.
- Keylogger [On/Off]: If turned on, keylogging thread operates.
- Rundll32 process termination [On/Off] If turned on, executes ‘taskkill /f /im rundll32.exe’ command to terminate the rundll32 process that is running.
- Self-copy file property [Attr]: Sets property to read-only, hidden, and system (FILE_ATTRIBUTE_READONLY|FILE_ATTRIBUTE_HIDDEN|FILE_ATTRIBUTE_SYSTEM).
The keylogger is perhaps the most aggressive of the above components.
The keylogging feature can operate by receiving a command from the C&C server, and it can also be activated depending on the settings data. Unlike Gh0st RAT which uses the Windows Hooking method (use of SetWindowsHookEx() API), Gh0stCringe uses the keylogging technique of Windows Polling method (using GetAsyncKeyState() API).
As explained by BleepingComputer, the malware will also trace keystrokes for the last three minutes and transmit them to the malware’s command and control servers along with basic system and network data.
These logged keystrokes will enable malicious actors to steal login credentials and other confidential material entered on the machine by logged-in users.
Modes and Commands
Gh0stCringe supports four distinct modes. The three modes are the values of the previously mentioned settings data, which were 0, 1, and 2. Furthermore, the malware is carried out in an exclusive mode in the Windows 10 version.
All modes eventually connect with the C&C server and execute commands, but there are contrasts in their features related to maintaining persistence.
Here is a list of commands that can be received and executed from the C&C server. Some of Gh0stCringe’s commands are present in the original Gh0st RAT, but there are many new ones as well.
Performing Commands
- Downloader: Downloads additional payload from the C&C server and executes it. Can send specific arguments
- Connecting to a specific URL: Connects to a specific website via Internet Explorer There is an option to hide the window so that the user does not notice it
- Destroying MBR
Stealing Information
- Keylogging: Regardless of whether there is settings data or not, keylogging can be performed by the C&C server’s command
- Stealing clipboard: Steals the saved data to the current clipboard
- Collecting Tencent-related file information: Collects the list of files in the path ‘%APPDATA%\Tencent\Users\’, and it is assumed that it would normally include user data related to QQ Messenger
Self-Control
- Update: Updates the malware
- Uninstall: Deletes the registered service and self-deletes using a batch file. Also deletes the keylogging data Default.key file
- Service control: Changes the ‘Host’ or ‘ConnectGroup’ item for the malware service (‘Rsuyke mkgcgkuc’)
- Event Cleanup
- Registering Run Key: Registers Run Key for the path ‘C:\Program Files\Common Files\scvh0st.exe’
System Control
- Terminating system
- Rebooting NIC
Database Servers Protection
- Update your server software to implement the most recent security patches. This will help to rule out a variety of attacks that take advantage of known flaws.
- Use a hard-to-guess admin password.
- Place the database server behind a firewall so that only allowed devices can access it.
- Keep an eye on everything to spot any dubious reconnaissance activity.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










