Contents:
Researchers from ESET have recently linked a stealthy cyberespionage group known as Gelsemium to the NoxPlayer Android emulator supply-chain attack that targeted gamers a few months ago.
Active since 2014, Gelsemium deploys its malware against a small number of victims, which suggests its involvement in cyberespionage. The report mentions that new targets were discovered that include governments, universities, electronics manufacturers, as well as religious organizations in East Asia and the Middle East.
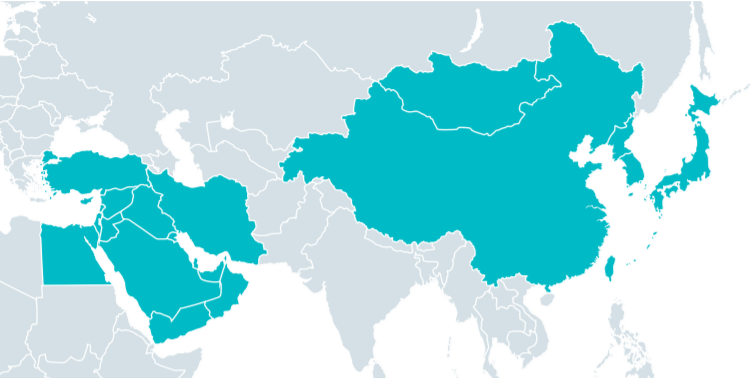
Image Source: ESET
The first vector was observed in 2014 and 2016 while investigating a targeted cyber-espionage campaign. Spear-phishing documents used exploits targeting a Microsoft Office vulnerability (CVE-2012-0158). This technique was used in the past as mentioned by G DATA and Verint Systems. Gelsemium distributed documents such as a resume written in Chinese to lure the victims.
In 2018, VenusTech mentioned a watering hole as a vector of compromise where Gelsemium used an intranet server to conduct the attack.
But while investigating several campaigns since mid-2020, researchers also found early versions of the group’s Gelsevirine “complex and modular” backdoor, BleepingComputer writes.
Gelsemium uses three components and a plug-in system to give the operators a range of possibilities to gather information: the dropper Gelsemine, the loader Gelsenicine, and the main plugin Gelsevirine.
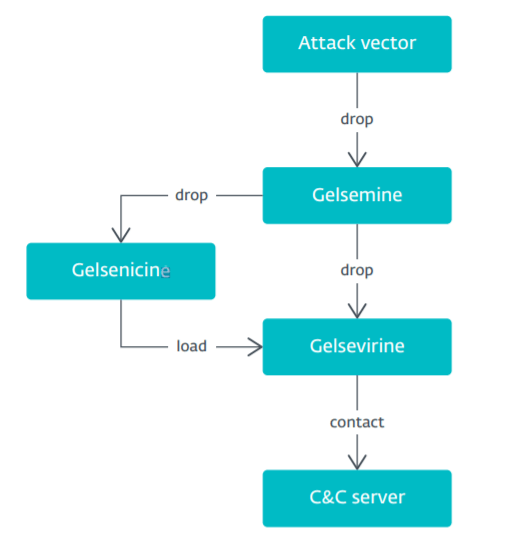
Image Source: ESET
Back in January, ESET researcher Ignacio Sanmillan analyzed and wrote an article about Operation NightScout, a supply-chain attack that compromised the update mechanism of NoxPlayer, an Android emulator for PCs and Macs, and part of BigNox’s product range. The investigation revealed an overlap between this supply-chain attack and the Gelsemium group. Victims originally compromised by that supply-chain attack were later being compromised by Gelsemine.
Among the variants examined by Sanmillan, “variant 2” depicted below, shows similarities with Gelsemium malware:
- They share the same directory where there are downloaded (C:\Intel\)
- Their filenames are identical (intel_update.exe)
- They embed two versions of the payload (32- and 64-bit)
- There is some network overlap (210.209.72[.]180)
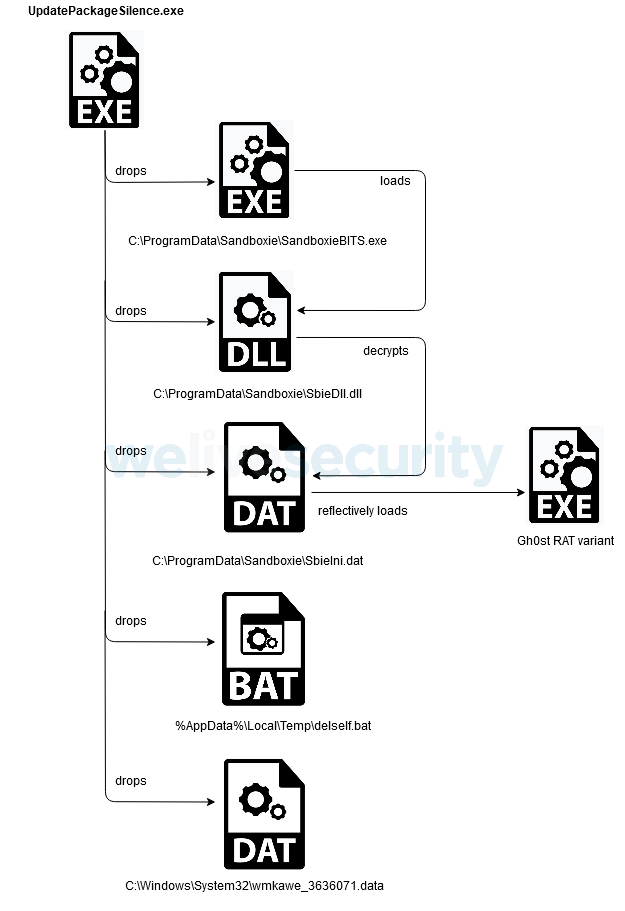
Anatomy of malicious update variant 2
Image Source: ESET
The researchers concluded that they did not observe links as strong as one campaign dropping or downloading a payload that belongs to the other campaign, however, they believe that Operation NightScout is related to the Gelsemium group.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










