Contents:
LibreOffice and OpenOffice have released fixes to tackle an issue that allows hackers to make documents look as if they were signed by a trustworthy source.
Even though the vulnerability is not placed in the ‘High’ severity category being rated as moderate, the consequences could be disastrous. The digital signatures used in document macros are intended to assist the user in determining whether or not a document has been modified and can be trustworthy.
Allowing anyone to sign macro-ridden documents themselves, and make them appear as trustworthy, is an excellent way to trick users into running malicious code.
Ruhr University Bochum’s cybersecurity researchers were the first to notice this vulnerability in OpenOffice, which has been tracked as CVE-2021-41832. The same issue affects LibreOffice, a project fork of OpenOffice that originated from the main project over ten years ago and is recorded as CVE-2021-25635 for their project.
Taking Care of The Issue
Those using at least one of the open-source office suites are recommended to update to the most recent version as quickly as possible.
- For OpenOffice – 4.1.10 and later
- For LibreOffice – 7.0.5 or 7.1.1 and later
Users will have to do the updates manually by downloading the newest version from the LibreOffice, OpenOffice download centers, as neither LibreOffice nor OpenOffice apps provide auto-updating.
Those using Linux who don’t have the versions mentioned above available on their distribution’s package manager yet are urged to download the “deb”, or “rpm” package from the Download center or build LibreOffice from source.
Those who can’t update to the newest version can always disable the macro features in their office suite or avoid trusting any documents that contain macros.
In order to set macro security on LibreOffice, go to Tools → Options → LibreOffice → Security, and click on ‘Macro Security’.
As we can see in the picture below, in the new window, the users can choose from four different levels of protection, with High or Very High being the suggested options.
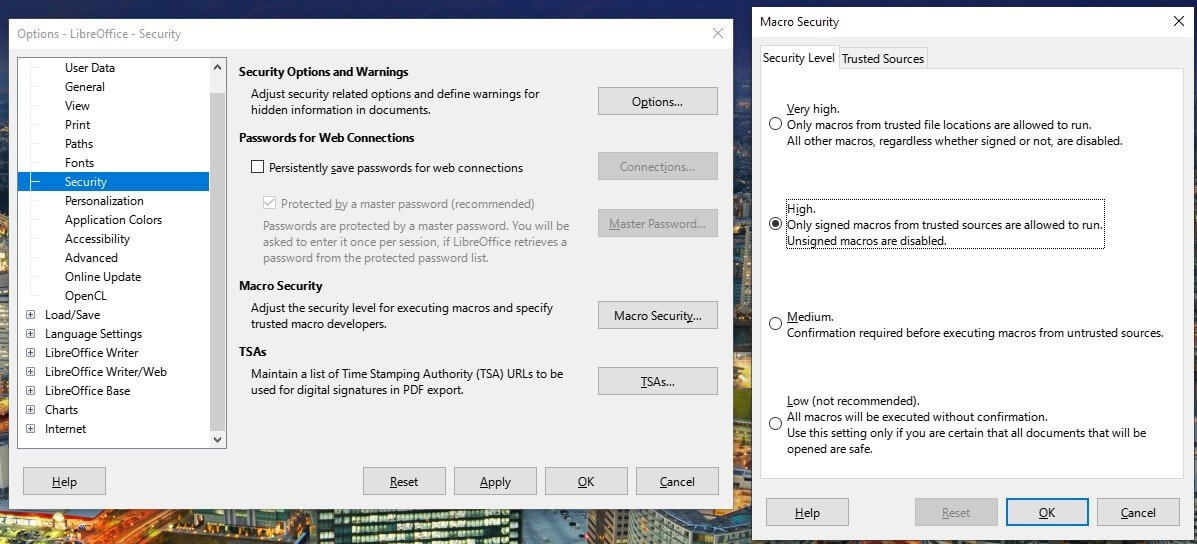
As recommended by BleepingComputer, users having an outdated and vulnerable version of the app shouldn’t count on the “trusted list” feature because a compromised document could still seem to come from a reputable source if the signature algorithm is incorrect.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










