Contents:
An ongoing campaign is targeting business routers using a new malware, the HiatusRAT router malware. The Hiatus campaign affects DrayTek Vigor router models 2960 and 3900.
The hackers aim to steal data and transform the infected device into a covert proxy network. DrayTek Vigor are VPN routers largely used by small and medium-size companies.
Details About the Campaign
The campaign started in July 2022 and has not ended yet, researchers at Black Lotus Labs say. Cybercriminals use three elements: a malicious bash script, a Remote Access Trojan (RAT) – HiatusRAT, and a variation of tcpdump, to capture traffic.
The malware, who gives the name of the campaign, is the most intriguing part. HiatusRAT can download additional malicious code, transform the machine into a proxy for C2 server traffic, and do specific commands on the infected device.
Once a targeted system is infected, HiatusRAT allows the threat actor to remotely interact with the system, and it utilizes prebuilt functionality – some of which is highly unusual – to convert the compromised machine into a covert proxy for the threat actor. The packet-capture binary enables the actor to monitor router traffic on ports associated with email and file-transfer communications.
Until now, the campaign affected at least a hundred of businesses. Targets are spread in Europe, North America, and South America.
Details About the Attack
After breaching a device, the threat actors deploy the bash script which then downloads and executes the HiatusRAT. Next, the malware steals the following data: system data, network data, file system data, and process data.
Hackers also use the RAT to communicate with the C2 server every 8 hours. This allows the attacker the supervise the compromised router.
The reverse engineer analysis revealed the following malware features:
config – load new configuration from the C2
shell – spawn a remote shell on the infected device
file – read, delete, or exfiltrate files to the C2
executor – fetch and execute a file from the C2
script – execute a script from the C2
tcp_forward – transmit any TCP data set to the host’s listening port to a forwarding location
socks5 – set up a SOCKS v5 proxy on the breached router
quit – stop the malware execution
The SOCKS proxy helps move data from other breached devices through the infected router, obscuring network data and imitating legitimate actions.
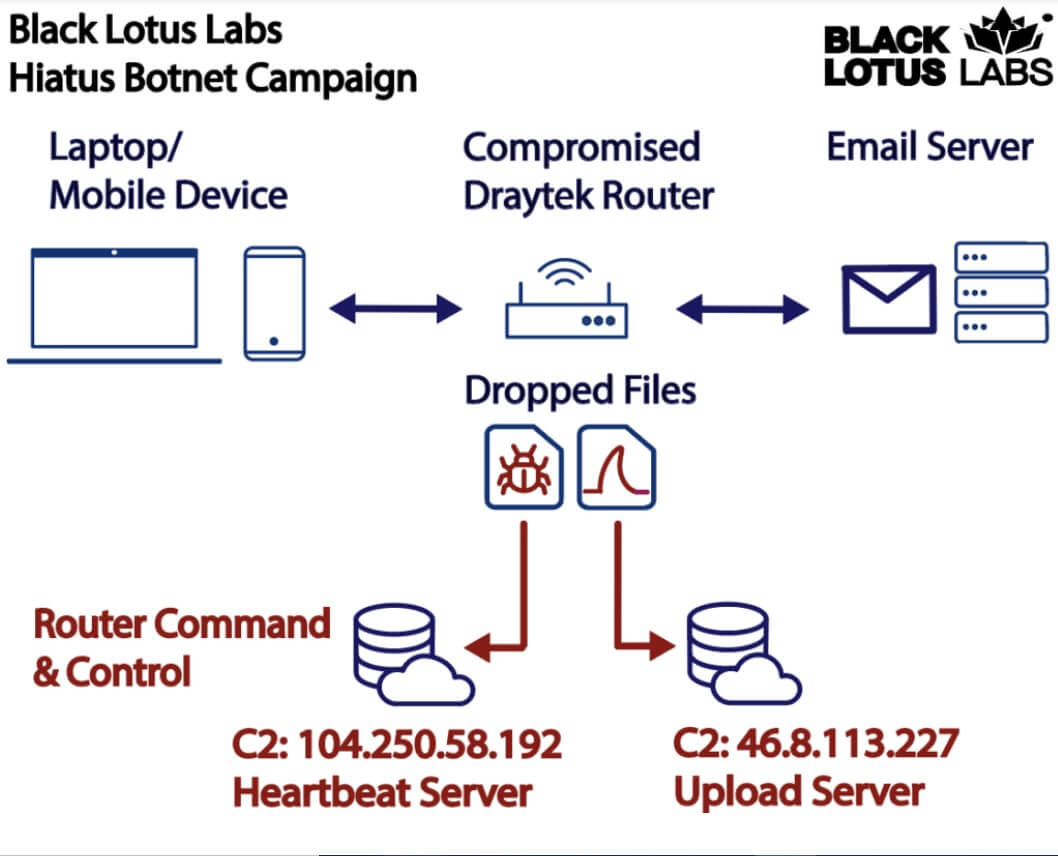
The bash script also deploys a packet-capturing program that monitors network activity to TCP ports related to mail servers and FTP connections. Ports have unencrypted communication, making it easy for hackers to steal data.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







