Contents:
The FBI’s email systems were hacked, and spam emails mimicking FBI warnings were sent out. The emails were warning in regards to a “sophisticated chain assault” perpetrated by an advanced threat artist called Vinny Troia.
Thousands of these communications were distributed in two waves, according to SpamHaus, a spam-tracking organization, but unfortunately, the researchers feel that this might be only a minor component of the malicious campaign’s overall strategy.
Researchers at the Spamhaus Project were able to observe two waves of this campaign taking place, one at 5 AM (UTC) and a second one, just two hours later.
What Happened?
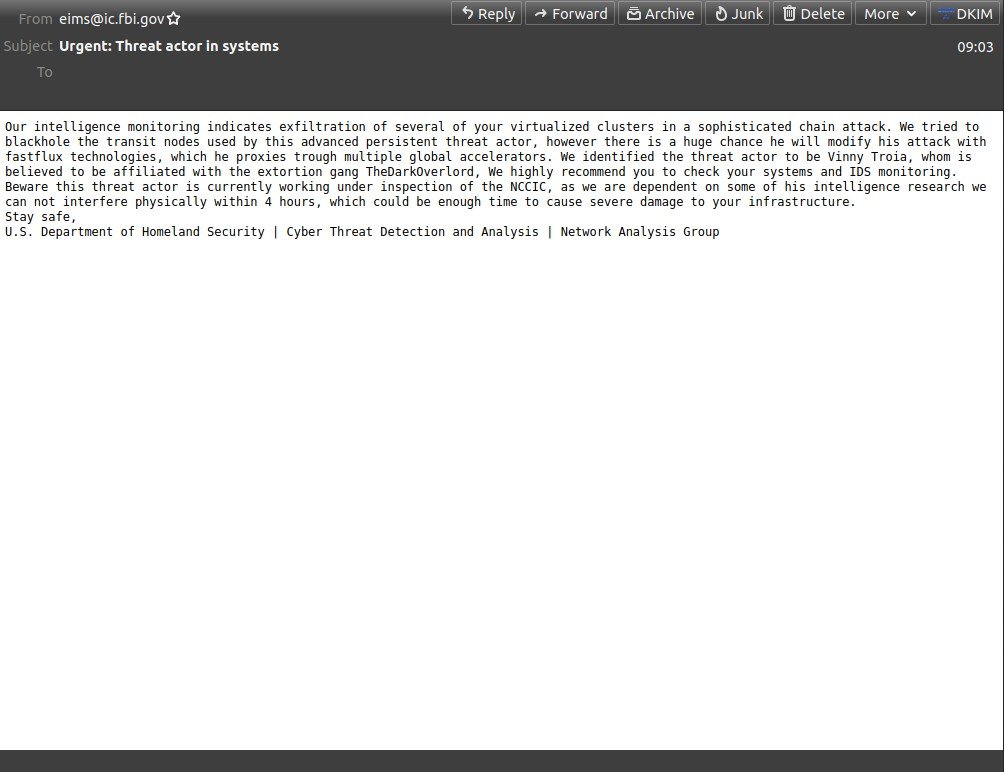
As reported by BleepingComputer the emails came from a legitimate email address, eims@ic.fbi.gov, and from the FBI’s IP address 153.31.119.142 (mx-east-ic.fbi.gov).
This email address is used by the FBI’s Law Enforcement Enterprise Portal (LEEP), and carried the subject “Urgent: Threat actor in systems.”
The false emails appear to have reached at least 100,000 inboxes. However, the figure is a cautious estimate, since the researchers feel “the campaign may have been much, much greater.”
We have been made aware of “scary” emails sent in the last few hours that purport to come from the FBI/DHS. While the emails are indeed being sent from infrastructure that is owned by the FBI/DHS (the LEEP portal), our research shows that these emails *are* fake.
— Spamhaus (@spamhaus) November 13, 2021
While the emails appear to be a hoax, the headers of the message reveal that their origin is validated by the DomainKeys Identified Mail (DKIM) method, indicating that they are sent from FBI servers.
While their helpdesk is overwhelmed with inquiries from frightened admins, the FBI stated that the emails’ content is fraudulent and that they are trying to resolve the situation.
The FBI and CISA are aware of the incident this morning involving fake emails from an @ic.fbi.gov email account. This is an ongoing situation and we are not able to provide any additional information at this time. We continue to encourage the public to be cautious of unknown senders and urge you to report suspicious activity to www.ic3.gov or www.cisa.gov.
FBI sent a second statement to BleepingComputer in which explained that the threat actor managed to make use of a software configuration in order to send out the emails.
The FBI is aware of a software misconfiguration that temporarily allowed an actor to leverage the Law Enforcement Enterprise Portal (LEEP) to send fake emails. LEEP is FBI IT infrastructure used to communicate with our state and local law enforcement partners. While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service. No actor was able to access or compromise any data or PII on FBI’s network. Once we learned of the incident we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks.
Who Could Be Behind the Attack?
The email alluded to the Dark Overlord, a worldwide hacking gang that supposedly steals data and demands large ransoms in exchange for its release.
According to the email, the “threat actor” was cybersecurity specialist Vinny Troia. Last year, Troia published an inquiry on the Dark Overlord.
These are very childish actions intended to discredit me for putting out a report which exposed his identity and involvement in several other hacking groups including the dark overlord, gnostic players, and shiny hunters. He is becoming bolder and much more blatant with his attacks.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security