Contents:
A new cyberespionage group targeting hotels, governments, and private businesses all over the world has been recently spotted by cybersecurity specialists at ESET.
According to them, the cyberespionage gang, dubbed FamousSparrow, is an Advanced Persistent Threat (APT) that has been operative since at least 2019. The APT is among those that targeted the ProxyLogon vulnerabilities earlier this year but it hasn’t been noticed until now.
FamousSparrow Goes Global
Even though the hacking group’s targets are usually hotels, security specialists have noticed the gang also attacked international companies, law organizations, and governments. Some of their victims are from the United Kingdom, Lithuania, Guatemala, Saudi Arabia, Brazil, Burkina Faso, South Africa, Canada, Israel, France, Taiwan, and Thailand.
ESET researchers Matthieu Faou and Tahseen Bin Taj stated:
The targeting, which includes governments worldwide, suggests that FamousSparrow’s intent is espionage.
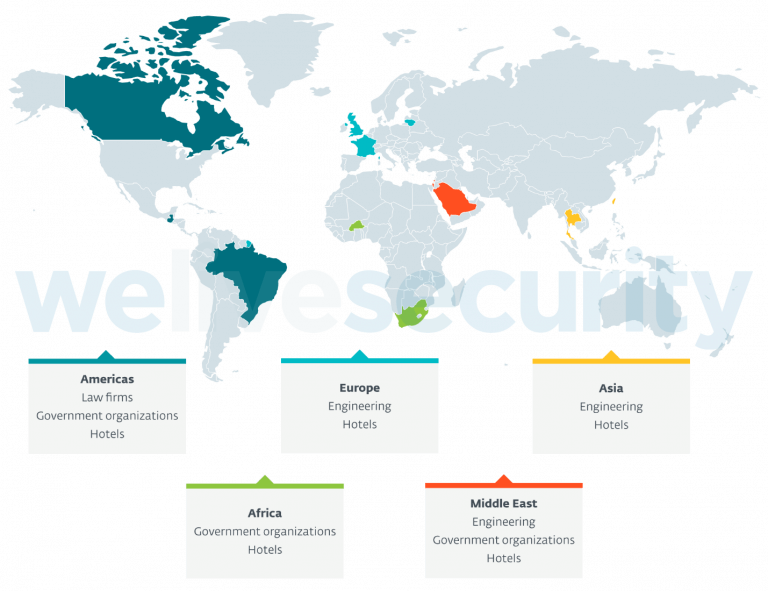
FamousSparrow Operation Mode
As stated by the specialists who were able to discover the initial compromise vector for certain cases, FamousSparrow compromised its victims’ systems via vulnerable internet web apps. The threat actor also exploited Remote Code Execution (RCE) vulnerabilities in Microsoft SharePoint, Oracle Opera (business software for hotel management), and the Microsoft Exchange security bugs known as ProxyLogon (in March 2021).
According to ESET, once a server is compromised, the APT infects it with custom tools such as:
- A version of Mimikatz
- a small tool that drops ProcDump on disk (created to collect credentials)
- NetBIOS scanner Nbtscan
- SparrowDoor own custom backdoor
The cybersec organization said that the backdoor is able to:
- rename or remove files;
- create directories;
- halt processes;
- send information such as file attributes,
- file size and file write time;
- exfiltrate the content of a specified file;
- write data to a specified file;
- remove persistence settings and all SparrowDoor files from the target devices.
FamousSparrow is currently the only user of a custom backdoor that we discovered in the investigation and called SparrowDoor. The group also uses two custom versions of Mimikatz.
The presence of any of these custom malicious tools could be used to connect incidents to FamousSparrow.
Connections to Other APT Operations
Researchers believe FamousSparrow is connected to other APT groups such as SparklingGoblin and DRBControl as they found similar malware versions but also state the newly discovered hacking group has its own entity.
They remind organizations everywhere of the importance of patching Internet-facing applications immediately. If this action is not possible, companies should not expose the apps to the Internet at all.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










