Contents:
Cyble Research and Intelligence Labs (CRIL) discovered multiple fake Zoom sites created to spread malware among Zoom users.
The sites were created with a similar user interface and disguised the malware as Zoom’s legitime application.
The whole discovery was triggered by a tweet mentioning the apparition of those sites:
Malware @Zoom downloads ?
/zoom-download.host
/zoom-download.space
/zoom-download.fun
/zoomus.host
/zoomus.tech
/zoomus.website
PDRhttps://t.co/7NJ4fEJ9Su@ULTRAFRAUD @malwrhunterteam @JAMESWT_MHT @illegalFawn @nullcookies @AlvieriD @BumbledBubble @ActorExpose pic.twitter.com/JYq2UJEMQ7— idclickthat (@idclickthat) September 12, 2022
Details About the Malware
CRIL analyzed the malware deployed by the fake sites and established that it was Vidar Stealer, a malicious code that has links to the Arkei stealer.
Vidar is designed to steal information from an infected device, including:
- Banking Information
- Saved Passwords
- IP Addresses
- Browser history
- Login credentials
- Crypto-wallets
Here is a list of fake Zoom sites to avoid:
- zoom-download[.]host
- zoom-download[.]space
- zoom-download[.]fun
- zoomus[.]host
- zoomus[.]tech
- zoomus[.]website
How Vidar Malware Works
The deceiving sites redirect users to this GitHub URL to download a malicious application: https[:]//github[.]com/sgrfbnfhgrhthr/csdvmghfmgfd/raw/main/Zoom.zip
The malicious application, upon execution, drops two binaries in the temporary folder:
- ZOOMIN~1.EXE
- Decoder.exe
A malicious .NET binary named Decoder.exe is injected into MSBuild.exe and executes the hackers’ code in order to steal information from the machine.
MSBuild (Microsoft Build Engine) is a platform that is used to create applications that are built using the .NET Framework. While the ZOOMIN~1.EXE file is a clean file and it executes the genuine Zoom installer only.
After being injected into MSBuild.exe, the malware retrieves the IP addresses linked to the DLLs and configuration data.
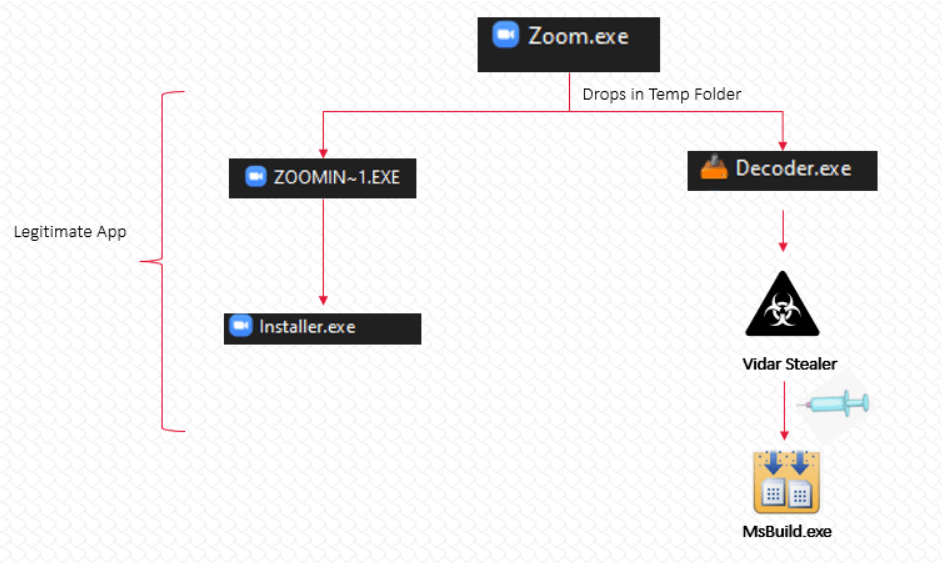
In this way, the malicious application receives the configuration data both from the C&C server and DLLs.
In order to remove itself from the victim’s device, the malware uses the following command line arguments after successfully executing the following commands:
C:\Windows\System32\cmd.exe” /c taskkill /im MSBuild.exe /f & timeout /t 6 & del /f /q
“C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe” & del C:\PrograData\*.dll & exit
How to Stay Safe
To stay safe on the Internet, there are several essential cybersecurity measures you can adopt:
- Avoid as much as possible using warez/torrent websites for downloading apps.
- Chose a strong password and implement multi-factor authentication.
- Constantly update all your systems and devices.
- Use a strong anti-virus program.
- Don’t open suspicious links or attachments.
- Invest in educating your employees so they will not be victims of phishing emails or social engineering.
- Block any URL used to spread malware.
- Monitor your network to prevent data exfiltration.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







