Contents:
Cybercriminals use fake accounts on Twitter and GitHub to spread fake proof-of-concept (PoC) exploits for zero-day vulnerabilities. They impersonate cybersecurity researchers to push Windows and Linux with malware.
How the Scam Works
These impersonators pretend to work at a fake cybersec company, named “High Sierra Cyber Security”, or even at well-known organizations. They create GitHub repositories, promoting them on Twitter to gain the victim’s trust. To appear legitimate, the fake accounts use a convincing profile photo.
They pretend to offer exploits for zero-day flaws in popular software like Chrome, Discord, Signal, WhatsApp, and Microsoft Exchange. Threat actors seem tenacious and open new accounts and repositories after the removal of the old ones.
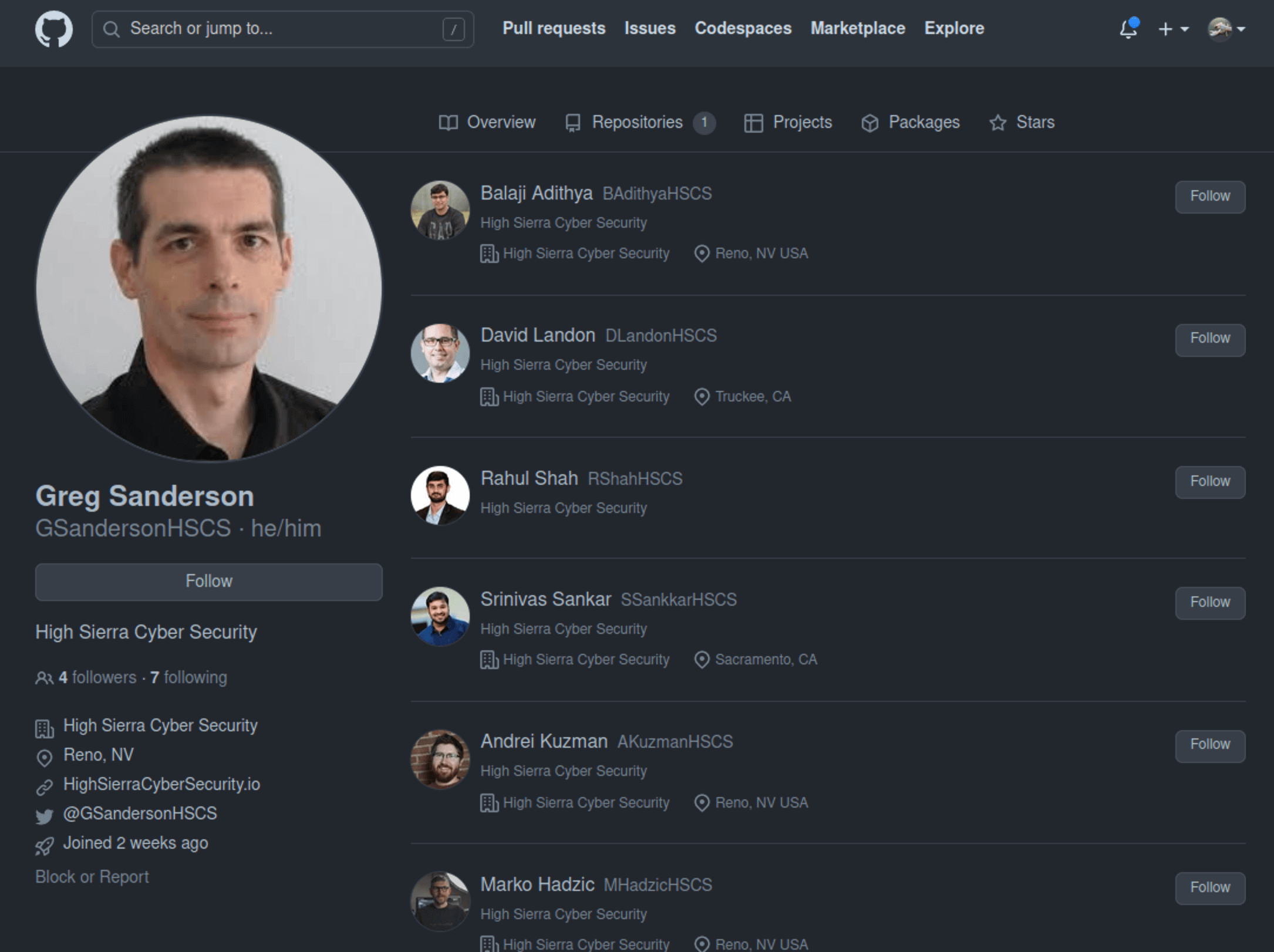
These GitHub repositories are malicious and should be avoided:
- github.com/AKuzmanHSCS/Microsoft-Exchange-RCE
- github.com/MHadzicHSCS/Chrome-0-day
- github.com/GSandersonHSCS/discord-0-day-fix
- github.com/BAdithyaHSCS/Exchange-0-Day
- github.com/RShahHSCS/Discord-0-Day-Exploit
- github.com/DLandonHSCS/Discord-RCE
- github.com/SsankkarHSCS/Chromium-0-Day
Also, these Twitter accounts are fake:
- twitter.com/AKuzmanHSCS
- twitter.com/DLandonHSCS
- twitter.com/GSandersonHSCS
- twitter.com/MHadzicHSCS
The campaign targets cybersecurity researchers and companies that do vulnerability research. These fake accounts were first discovered by VulnCheck in May 2023.
Details About the Malware
The malicious load was a Python script (‘poc.py’) functioning as a malware downloader for Linux and Windows systems.
The script downloads a ZIP archive from an external URL to the victim’s computer depending on their operating system, with Linux users downloading ‘cveslinux.zip’ and Windows users receiving ‘cveswindows.zip.’
The malware is saved to the Windows %Temp% or the Linux /home/<username>/.local/share folders, extracted, and executed.
Over 60% of antivirus engines on VirusTotal have identified the Windows binary (‘cves_windows.exe’) that is included in the ZIP. Only three scanners were able to detect the far stealthier Linux binary (‘cves_linux’).
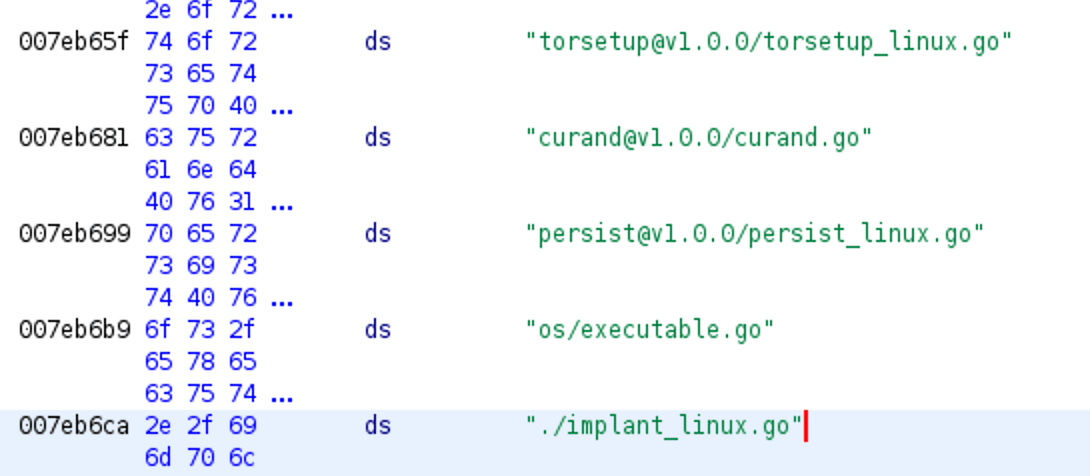
Although it’s unclear what type of malware carries, both executables install a TOR client with the Windows version showing some password-stealing trojan features.
Targeting Security Experts
This is not the first campaign of this kind. Lazarus, a North Korean state-sponsored group, launched a similar one in 2021. To target researchers with malware and zero-days, they developed false vulnerability researcher profiles on social media.
More recently, academics found thousands of repositories on GitHub offering fake proof-of-concept (PoC) exploits for various vulnerabilities, some of them infecting users with malware, malicious PowerShell, obfuscated info-stealer downloaders, Cobalt Strike droppers, and more.
Threat actors can get vulnerability research that they can employ in their own assaults by focusing on the cybersecurity community. Furthermore, the malware may frequently grant initial access to a cybersecurity firm’s network, opening the door for additional data theft and extortion attempts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







