Contents:
While it became normality for phishing operations that distribute weaponized Microsoft Office documents to trick recipients into enabling the macros to prompt the infection chain directly, a new discovery shows hackers use non-malicious documents to disable security warnings prior to executing macro code to infect victims’ devices.
According to McAfee researchers, the new technique involves the sending of a phishing email containing a supposedly harmless Microsoft Word attachment.
Once opened, it activates a chain of events that ultimately downloads the payload for the notorious banking and data exfiltration malware Zloader.
The cybersecurity firm observed that ZLoader infections employing this method have been primarily reported in the U.S., Canada, Spain, Japan, and Malaysia.
ZLoader is spread through aggressive email operations where the email contains a malicious attachment with provocative titles and invoices with links to infected Microsoft Word files.
ZLoader hackers aim to steal credentials and Personally Identifiable Information (PII) from users of targeted financial institutions.
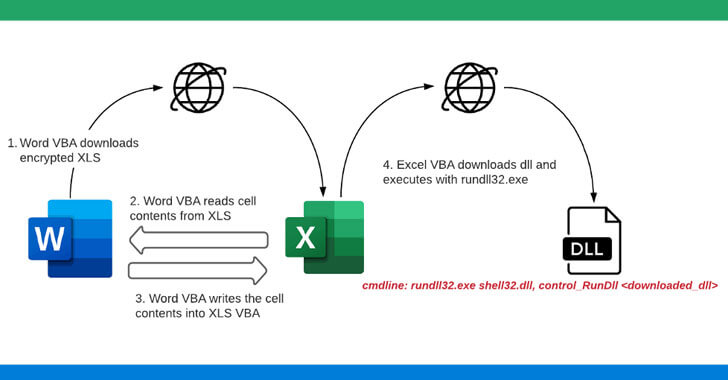
During the investigation, the cybersecurity specialists discovered the infection chain began with a phishing email that included a Microsoft Word document attachment. When opened, it downloaded a password-protected Microsoft Excel file from a remote server.
It is important to know that macros have to be enabled in the Word document to initiate the download itself.
After downloading the XLS file, the Word VBA reads the cell contents from XLS and creates a new macro for the same XLS file and writes the cell contents to XLS VBA macros as functions.
Once the macros are written and ready, the Word document sets the policy in the registry to ‘Disable Excel Macro Warning’ and invokes the malicious macro function from the Excel file. The Excel file now downloads the ZLoader payload. The ZLoader payload is then executed using rundll32.exe.
Because macros constitute such a significant security risk, the feature is normally disabled by default, but the solution has had an unfortunate side-effect of cybercriminals crafting convincing social engineering lures to fool victims into authorizing them.
By deactivating the security warning presented to the user, the attacks are significant because of the steps it takes to bypass detection and to get unnoticed.
Malicious documents have been an entry point for most malware families and these attacks have been evolving their infection techniques and obfuscation, not just limiting to direct downloads of payload from VBA, but creating agents dynamically to download payloads.
Usage of such agents in the infection chain is not only limited to Word or Excel, but further threats may use other living off the land tools to download its payloads.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










