Contents:
Epsilon Red ransomware is a new player in the ransomware scenario which uses attacks that are relying on more than a dozen scripts before reaching the encryption stage and also uses a commercial remote desktop utility.
The name of the malicious group comes from the Marvel Universe as Epsilon Red is a little-known character, a Russian super-soldier with four tentacles that can breathe in space.

Researchers at Sophos have discovered the new Epsilon Red ransomware when they were investigating an attack at a fairly large U.S. company in the hospitality sector.
It seems the threat actor breached the enterprise network by exploiting unpatched vulnerabilities in the on-premise Microsoft Exchange server.
Andrew Brandt, the principal researcher at Sophos, says in its report that the attackers have probably leveraged the ProxyLogon set of vulnerabilities to reach machines on the network, as the ProxyLogon bugs have been widely publicized, with hackers jumping to the occasion and scanning the web for vulnerable devices in order to compromise the systems.
The critical severity made organizations across the world rush to install the patches, therefore in less than a month, more than 92% of vulnerable on-premise Microsoft Exchange servers were already updated.
An interesting fact about Epsilon Red is the fact that it’s written in Golang (Go) and is preceded by a set of unique PowerShell scripts made to prepare the ground for the file-encryption routine, with each of them having a specific purpose:
- kill processes and services for security tools, databases, backup programs, Office apps, email clients;
- delete Volume Shadow Copies;
- steal the Security Account Manager (SAM) file containing password hashes;
- delete Windows Event Logs;
- disable Windows Defender;
- suspend processes;
- uninstall security tools (Sophos, Trend Micro, Cylance, MalwareBytes, Sentinel One, Vipre, Webroot);
- expand permissions on the system.
The hackers’ MO is that after breaching the network, they will reach the machines over RDP and use Windows Management Instrumentation (WMI), and install the software in order to be able to run PowerShell scripts that ultimately deploy Epsilon Red executable.
The threat actor is installing a copy of Remote Utilities software – a commercial software for remote desktop operations, and the Tor Browser in order to make sure they still have a door open if they lose access through the initial entry point.
According to Peter Mackenzie, this version of Epsilon Red does not appear to be the work of professionals but it can cause quite a mess as it comes with no restrictions for encrypting file types and folders.
Epsilon Red has little functionality apart from encrypting files and folders but interestingly enough it contains code from the open-source tool godirwalk, therefore offering Epsilon Red the ability to scan the hard drive and add directory paths to a list of destinations for child processes that encrypt subfolders individually.
Epsilon Red encrypts everything in the targeted folders appending the suffix “.epsilonred” and drops in each processed folder the ransom note with instructions on how to contact the attackers for negotiating a data decryption price.
The attackers are using a slightly improved version of the ransom note used by REvil ransomware, having the original grammar and spelling mistakes being corrected.
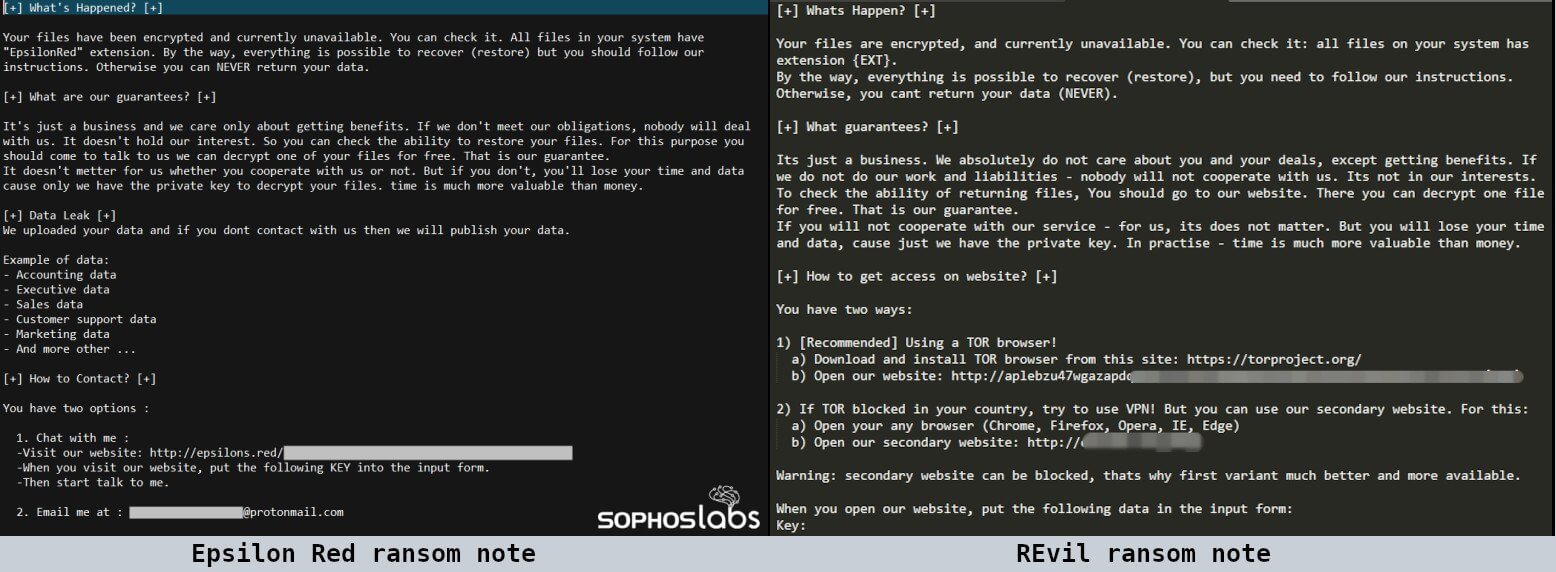
Even if they are quite new in the ransomware business, the ransomware gang has already attacked several companies and has also made some money, as the researchers from Sophos found that one victim of this ransomware threat recently paid about $210,000 in bitcoin.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








