Contents:
Another threat actor group is making way on the cyber threat landscape targeting organizations worldwide to deprive them of millions of dollars. This was dubbed ‘Elephant Beetle’, using in its attacks more than 80 unique tools and scripts.
Elephant Beetle Attack Methods
The researchers from Sygnia published a thorough report about the so-called ‘Elephant Beetle’. It seems that the malicious group waits for months to analyze the environment and financial transaction processes of the victim before actually moving to perform vulnerabilities’ exploitation.
Their method is based on injecting fraudulent transactions into the network and eventually performing theft of lots of money, amounting to millions of dollars. When caught, they maintain a low profile for some time then use a different system to make a comeback.
Apparently Elephant Beetle targets legacy Java applications on Linux systems, this representing their entry point in a company’s network.
This threat actor group’s method is not based on buying or developing zero-day exploits, but rather they choose to target common vulnerabilities that might be probably unpatched.
What Flaws Is Elephant Beetle Exploiting?
The Sygnia experts mentioned in their report that the Elephant Beetle group is targeting 4 vulnerabilities, these including:
- CVE-2017-1000486 found under the name of Primefaces Application Expression Language Injection;
- CVE-2015-7450 referring to a WebSphere Application Server SOAP Deserialization Exploit;
- CVE-2010-5326 pointing to an SAP NetWeaver Invoker Servlet Exploit;
- And eventually, EDB-ID-24963 or better known as SAP NetWeaver ConfigServlet Remote Code Execution.
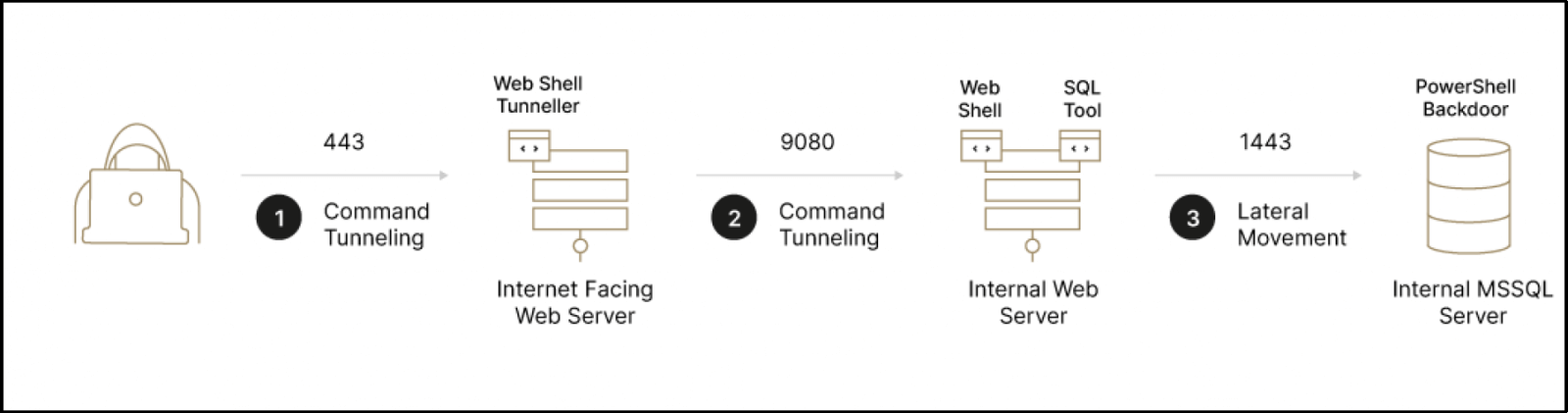
Exploiting these 4 vulnerabilities, threat actors can execute arbitrary code remotely by means of a web shell that is particularly obfuscated and crafted.
The actors choose to stay hidden for a period of months because they need to develop long-term surveillance and research first thing before letting the cyberattack unfold. How do they achieve this? They mimic legitimate packages in their attempt to blend with regular traffic. This way web shells are disguised as fonts, CSS, JS resources, or images, and payloads are packed by means of WAR archives.
Elephant Beetle and the Lateral Movement onto the Network
After this threat actor group manages to compromise the first web server, what happens next is that it leverages a custom Java scanner. This tool has the role to fetch an IP addresses’ list linked with a certain HTTP interface or port. According to the researchers, among the characteristics of this tool can also be mentioned its versatility and configurability and that Elephant Beetle chooses to massively leverage it in its operations.
The threat group move laterally within the network mainly through web application servers and SQL servers, leveraging known techniques such as Windows APIs (SMB/WMI) and ‘xp_cmdshell’, combined with custom remote execution volatile backdoors. For transferring tools and their outputs between compromised machines, the group leverage either a custom Java uploader/downloader tool or various web shells that have file uploading/downloading capabilities.
After the identification of potential internal server pivoting points is complete, RCE bugs or compromised credentials are used by the Elephant Beetle group to perform lateral movement onto the network.
Defense Recommendations
The same researchers make some recommendations on how to protect against this threat actor group dubbed Elephant Beetle. Thus:
- the use of the ‘xp_cmdshell’ procedure should be avoided and it must be disabled on MS-SQL servers. Its usage and configuration changes should be closely monitored.
- WAR deployments should be monitored too and it also must be checked if the logging policy of relevant apps includes the packages deployment feature.
- the possibility of .class file presence and creation in the WebSphere applications temp folders should be closely monitored.
- processes executed by web server parent services like for instance ‘w3wp.exe’, ‘tomcat6.exe’, or by database-related processes as ‘sqlservr.exe’ should be also overseen.
- segregation between DMZ and internal servers should be checked and implemented.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security