Contents:
The Dridex malware is a banking trojan that was originally designed to steal victims’ online banking credentials but has since evolved into a loader that downloads various modules that can be used to perform various malicious actions, such as installing additional payloads, spreading to other devices, taking screenshots, and more.
Dridex infections have been related to ransomware attacks carried out by activities linked to the Evil Corp hacker gang.
What Happened?
Cryptolaemus, a cybersecurity research firm, has warned that the Log4j vulnerability is currently being used to infect Windows devices with the Dridex Trojan and Linux devices with Meterpreter.
We have verified distribution of #Dridex 22203 on Windows via #Log4j #Log4Shell. Class > MSHTA > VBS > rundll32.
Class: https://t.co/ivdZSd1QGR
Payload URLs: https://t.co/RoZubNKUs5
DLL sample: https://t.co/6P8aHdim8v
HTA > DLL run: https://t.co/KdGZfmHkMN pic.twitter.com/IsoYWfdKcq— Cryptolaemus (@Cryptolaemus1) December 20, 2021
According to Joseph Roosen, threat actors harness the Log4j RMI (Remote Method Invocation) exploit variant to force susceptible devices to load and execute a Java class from an attacker-controlled remote server.
As explained by BleepingComputer, when the Java class is launched, it will first try to download and launch an HTA file from multiple URLs, which will install the Dridex trojan. If the Windows instructions cannot be executed, it will assume the device is running Linux/Unix and will download and run a Python script to install Meterpreter.
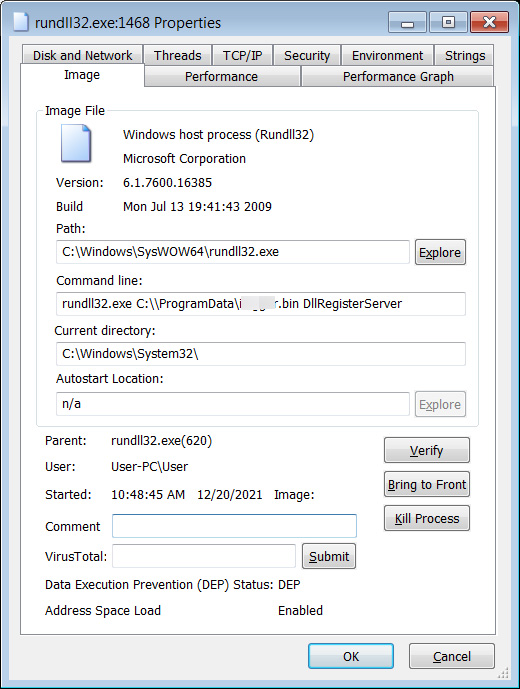
The Java class on Windows will download and open an HTA file, resulting in the production of a VBS file in the C:ProgramData folder. This VBS program serves as Dridex’s principal downloader and has previously been seen in Dridex email campaigns.
When run, the VBS code will check several environment variables to see if the user is a member of a Windows domain. If the user is a domain member, the VBS code will download the Dridex DLL and run it with Rundll32.exe.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








