Contents:
In January 2021, news surfaced of a ransomware strain known as Deadbolt that targets backups and is intended at serious home users, hobbyists, and small companies. Deadbolt is designed to extort money from its victims. Users who needed backups and were knowledgeable enough to make them, but who lacked the time or funds to give their backup routine the attention it deserves were the type of customers that Deadbolt targeted.
What Happened?
In May, QNAP issued a warning to its customers about continuous assaults against NAS equipment that were being carried out by the DeadBolt ransomware organization.
Taipei, Taiwan, May 19, 2022 – QNAP® Systems, Inc. recently detected a new attack by the DEADBOLT Ransomware. According to the investigation by the QNAP Product Security Incident Response Team (QNAP PSIRT), the attack targeted NAS devices using QTS 4.3.6 and QTS 4.4.1, and the affected models were mainly TS-x51 series and TS-x53 series . QNAP urges all NAS users to check and update QTS to the latest version as soon as possible, and avoid exposing their NAS to the Internet.
As Cyware explained, the attacks began in January, and the threat actor is demanding a ransom payment of 0.03 bitcoins in exchange for the decryption key.
DeadBolt makes use of a variety of advanced TTPs, one of which is comprised of several payment alternatives, one of which is reserved for the user, and the other of which is reserved for the vendor.
However, even if the vendors pay the ransom, they will not be given a master key to open all of the victims’ data. This is the case regardless of whether or not they pay the money.
This is the first time that a ransomware gang has combined two ransoms into a single assault, which distinguishes it as a one-of-a-kind danger.
In contrast to other families of ransomware, which give difficult-to-understand processes, the operators of this virus have developed an online user interface that, after the ransom is paid and a decryption key is supplied, decrypts the data of victims.
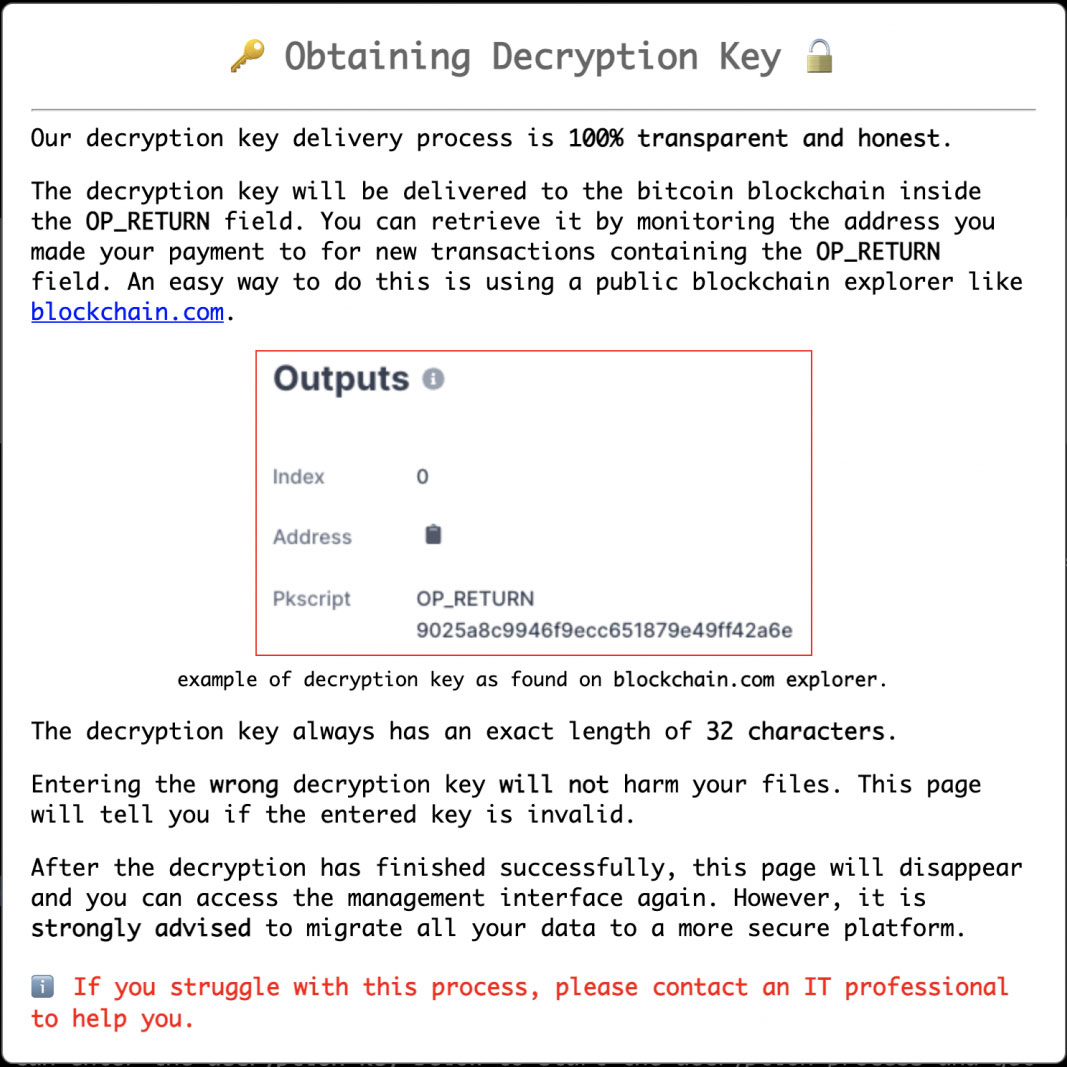
A further innovative aspect is that the victims do not have to make contact with the attackers in order to get the decryption key since the blockchain transaction does it automatically.
According to Trend Micro, data that were encrypted by the ransomware cannot be decrypted since the master key decryption procedure has not been able to be verified. This makes it impossible to decrypt the contents.
Even though the vendor master decryption key did not work in DeadBolt’s campaigns, the concept of holding both the victim and the vendors ransom is an interesting approach. It’s possible that this approach will be used in future attacks, especially since this tactic requires a low amount of effort on the part of a ransomware group.
DeadBolt represents several innovations in the ransomware world: It targets NAS devices, has a multitiered payment and extortion scheme, and has a flexible configuration. But perhaps its main contribution to the ransomware ecosystem will be the legacy of its heavily automated approach. There is a lot of attention on ransomware families that focus on big-game hunting and one-off payments, but it’s also important to keep in mind that ransomware families that focus on spray-and-pray types of attacks such as DeadBolt can also leave a lot of damage to end users and vendors.
If Ransomware Is a Concern for You
Join us on Tuesday, June 21st, 1pm BST/2pm CEST for our next webinar, when Cyber-Security & Heimdal Product Expert Andrei Hinodache and Pre-Sales Engineering Manager Robertino Matausch will explain why ransomware is on the rise, and how should executives evaluate their company’s ability to prevent and recover from ransomware attacks.
What’s more, we will be showing you how to do this LIVE! Our experts will walk you through ransomware incident preparedness, technical testing through live simulations, detection, and suggestions for thwarting attackers by hardening systems and infrastructure.
Make sure you register here!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










