Contents:
Cybersecurity researchers from Dutch cybersecurity firm Tesorion analyzed the Lorenz ransomware and have come up with a fix that could allow victims to decrypt their files without being forced to make a ransom payment.
Just like other ransomware attacks, Lorenz ransomware breaches a network and spreads laterally to other devices until it gains access to Windows domain administrator credentials.
Lorenz threat actors also implement the double-extortion model by stealing data before encrypting it and threaten to publish it if the victim doesn’t pay the ransom. Until now, ransom demands varied between $500.000 and $700.000.
While spreading throughout the system, they will harvest unencrypted files from victims’ servers, which they upload to remote servers under their control. This stolen data is then published on a dedicated data leak site to pressure victims to pay a ransom or to sell the data to other threat actors.
Below, you can see a Lorenz data leak website that was listing twelve victims, while having exposed data for ten of them.
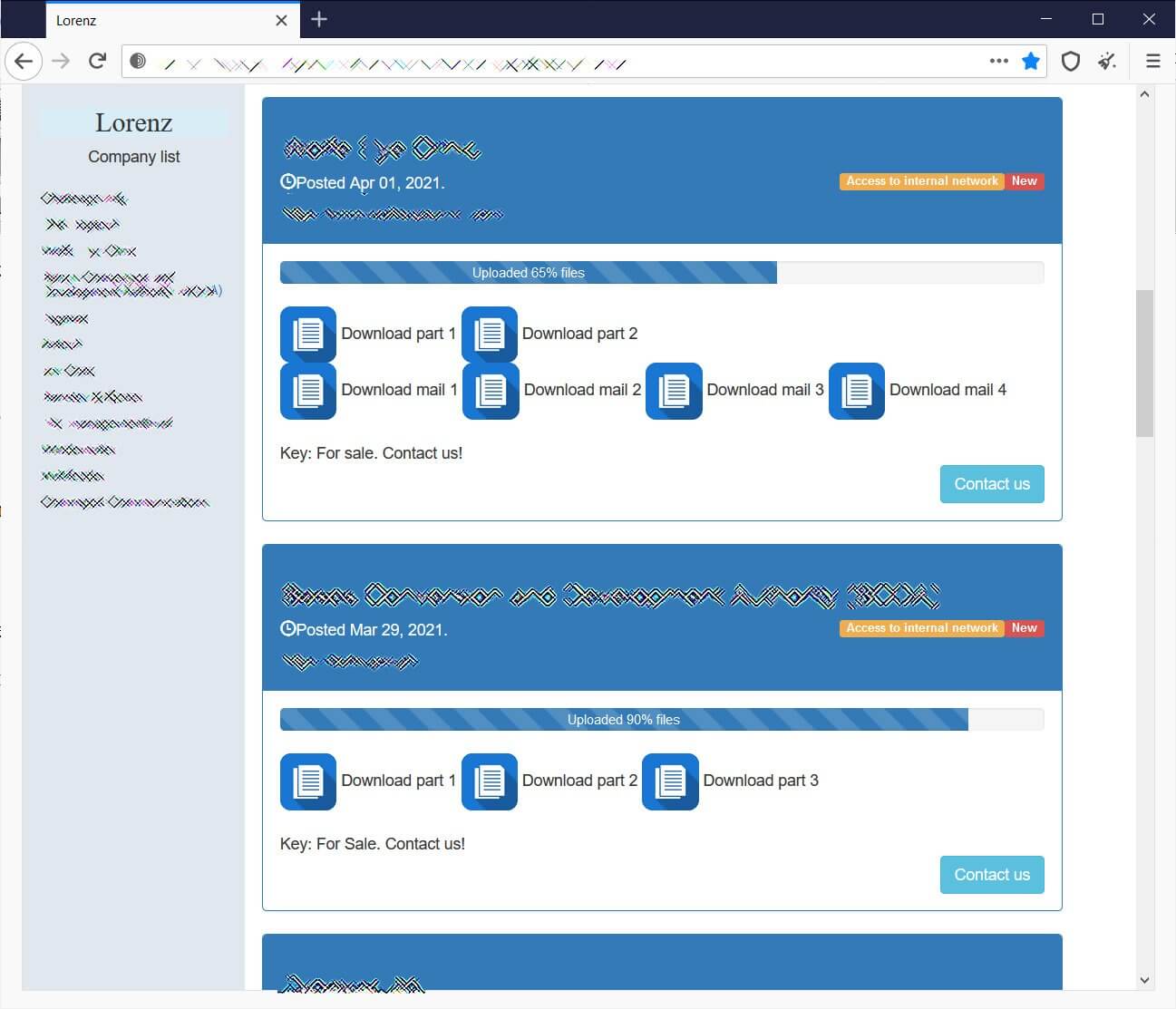
Lorenz Ransomware Decryptor Only Works for Certain Files
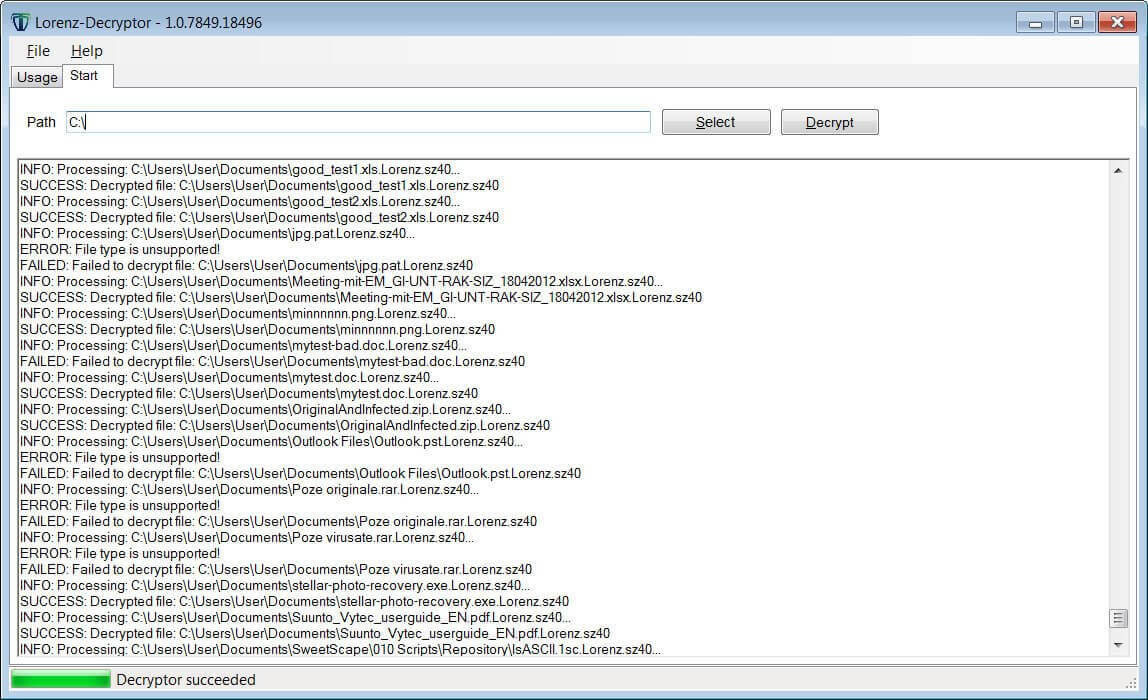
Following the Lorenz ransomware analysis, the cybersecurity firm Tesorion came to the conclusion that they can decrypt (non-corrupted) affected files in some cases without paying a ransom. Supported file types include Microsoft Office documents, PDF files, and some image and movie files.
The Lorenz ransomware decryptor, provided by Tesorion to victims for free, will be available for download via the NoMoreRansom initiative soon.
Even if the decryptor can’t decrypt every file type, it will help the ransomware victims to recuperate some important files without paying the ransom.
As shown by BleepingComputer, the decryptor can decrypt well-known file types, such as XLS and XLSX files, without a problem. However, it will not decrypt unknown file types or those with uncommon file structures.
In a blog post, Tesorion researcher Gijs Rijnders explains that a vulnerability in how they execute their encryption can lead to data loss, which would prevent a file from being decrypted even if the ransom payment was made.
The result of this bug is that for every file which’s size is a multiple of 48 bytes, the last 48 bytes are lost. Even if you managed to obtain a decryptor from the malware authors, these bytes cannot be recovered.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










