Contents:
The water supply system of Arkansas City, Kansas, activated manual operation mode to contain a cyberattack. The security team discovered the attack on Sunday morning.
City authorities say the water supply remains safe and there are no service disruptions.
FBI agents are part of the investigation. For now, there are no other details about the attackers’ techniques and purpose.
City Officials said
Enhanced security measures are currently in place to protect the water supply, and no changes to water quality or service are expected for residents
Source – Bleepingcomputer.com
Keeping US’s water systems safe
On September 20th, the Water Information Sharing and Analysis Center (WaterISAC) nonprofit organization released an AMBER threat advisory on Russian threat actors targeting the water sector. One day before, the U.S. Environmental Protection Agency (EPA) shared guidelines on cybersecurity best practices and evaluation methods for owners and operators of water and wastewater systems (WWSs).
In addition, earlier this year, January 2024, CISA released an Incident Response Guide: Water and Wastewater Sector. The guide warns that
The dependency that many U.S. critical infrastructure sectors – including Energy and Healthcare and Public Health – have on the WWS makes the Sector a target for cyber threat actors.
Cyber threat actors frequently use ransomware against WWS utilities. In recent years, various malicious cyber incidents have impacted WWS including, but not limited to, unauthorized access, and ransomware.
Source – CISA Incident Response Guide: Water and Wastewater Sector
Keeping US’s water systems safe has no doubt become a tricky job. Remaining offline and reverting digitalization is not an option. So, how do you bolster the security posture of critical public services?
Adopting a layered defense strategy is your best bet. There are three main choices to implement that:
- Buy, deploy and manage various security single-purpose tools to cover Endpoint Detection and Response, DNS security, patch management, privileged access management, etc. This can turn out to be resource consuming.
- Partner with an MSP or MSSP to take care of safeguarding the IT infrastructure.
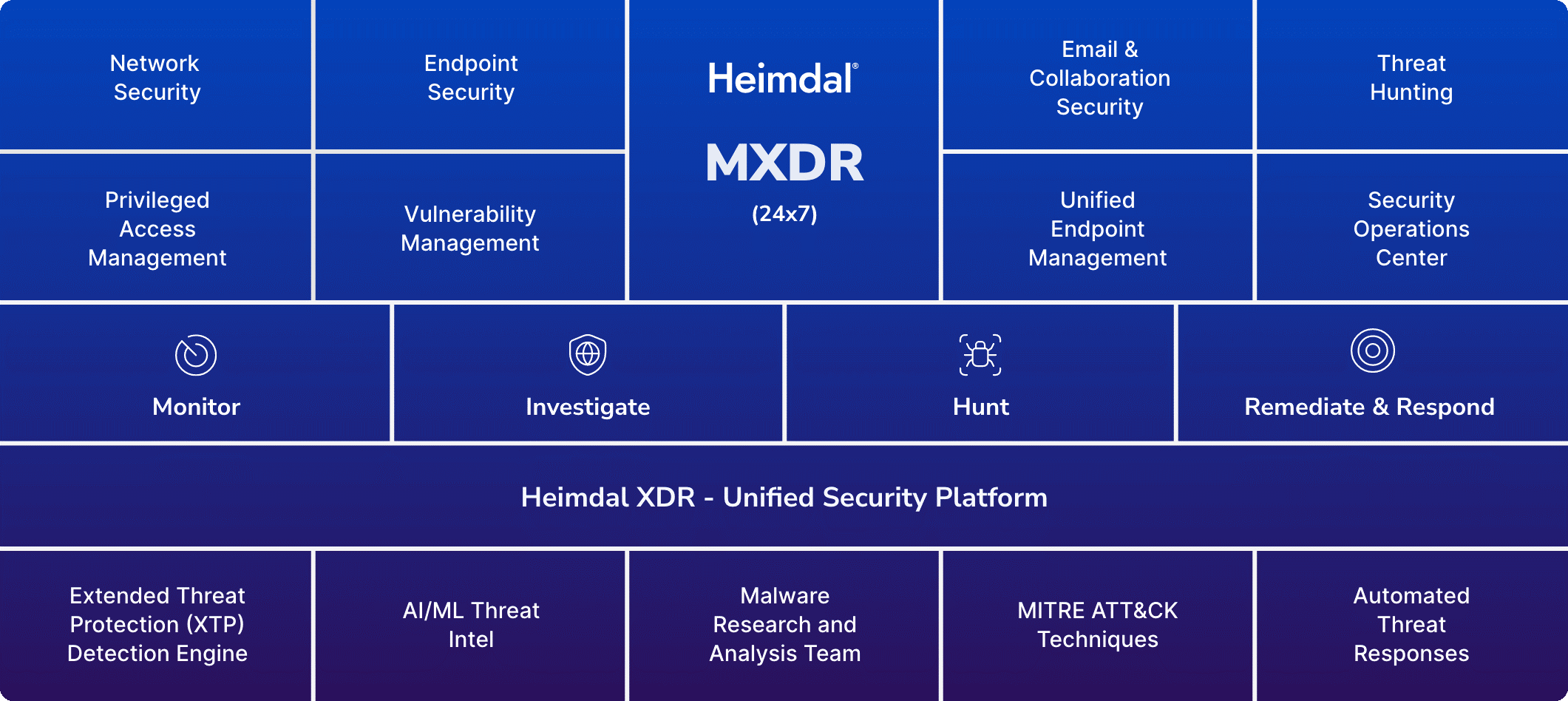
- Subscribe to a cybersecurity platform, like Heimdal’s XDR, to get all the tools you need on the same dashboard and working seamlessly together. There’s also an MXDR option, that solves an organization’s need for highly skilled personnel.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








