Contents:
17 large organizations have been alerted by the New York State Office of the Attorney General that over one million of their clients have had their accounts hacked in credential stuffing attacks.
As explained by my colleague,
Credential stuffing is a form of cyberattack where hackers are taking over massive databases of usernames and passwords, many of which are stolen in recent data breaches, and use an automated method to “stuff” the account logins into other online services.
Unfortunately, carrying out credential stuffing attacks is getting increasingly simple and inexpensive. User behavior is still the principal source of power when it comes to this type of cyberattack because users can’t seem to break the habit of reusing the same credentials across more than one platform.
The main objective of the threat actors is to obtain access to as many accounts as possible to collect the personal and financial information linked with those accounts, which may then be put up for sale on hacker forums or the dark web markets.
Also, the stolen private data could potentially be used by the attackers to perform identity theft or make illicit purchases.
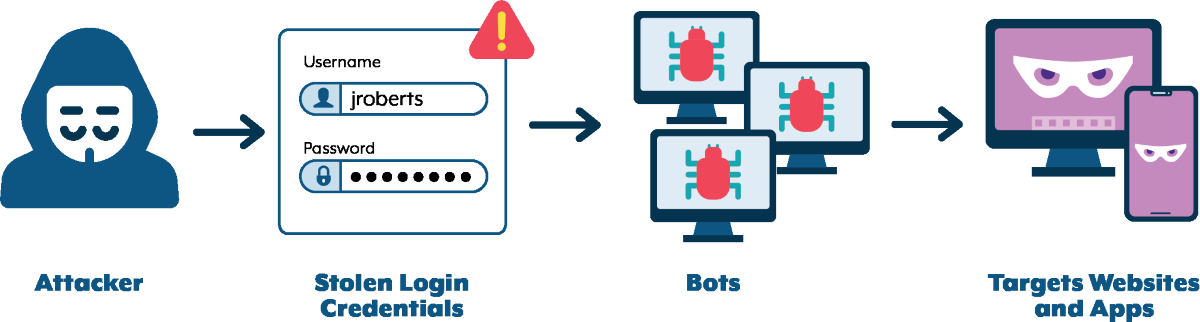
The Discovery of the Credential Stuffing Attacks
As per BleepingComputer, after conducting a “sweeping investigation” that kept going for several months, the New York State Office of the Attorney General (NY OAG) has eventually found the hacked accounts.
The investigation involved the surveillance of numerous online communities especially created to share validated credentials acquired in previously undiscovered credential stuffing attacks.
Mitigations
After reviewing thousands of posts, the OAG compiled login credentials for customer accounts at 17 well-known companies, which included online retailers, restaurant chains, and food delivery services.
In all, the OAG collected credentials for more than 1.1 million customer accounts, all of which appeared to have been compromised in credential stuffing attacks.
Following the discovery of the attacks, the Office of the Attorney General (OAG) alerted the relevant companies so that passwords could be reset and consumers could be notified.
As mentioned by BleepingComputer, cloud service company Akamai Technologies released a report in May 2021 stating there were over 193 billion credential stuffing attacks worldwide in 2020, with a 45% growth over the previous year.
Also, according to a Digital Shadows report, over 15 billion credentials are currently being traded or sold online, the majority of which belong to customers.
Right now, there are more than 15 billion stolen credentials being circulated across the internet, as users’ personal information stands in jeopardy.
Businesses have the responsibility to take appropriate action to protect their customers’ online accounts and this guide lays out critical safeguards companies can use in the fight against credential stuffing. We must do everything we can to protect consumers’ personal information and their privacy.
Recommendations for Companies
Furthermore, the New York State Office of the Attorney General released a report yesterday that included additional information about its credential stuffing investigation and how companies should safeguard their clients and handle similar incidents.
Organizations are advised to:
- implement bot detection software,
- enable multi-factor authentication and password-less authentication,
- monitor customer traffic for indications of attack attempts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










