Contents:
Researchers have recently discovered a new malware they named BHUNT. This targets passwords, security phrases, and cryptocurrency wallet contents.
BHUNT Crypto Stealer: More Details
The Bitdefender researchers were the ones who identified this new malware dubbed BHUNT and analyzed it in a report recently published.
We named the stealer BHUNT after the main assembly’s name. BHUNT is a modular stealer written in .NET, capable of exfiltrating wallet (Exodus, Electrum, Atomic, Jaxx, Ethereum, Bitcoin, Litecoin wallets) contents, passwords stored in the browser, and passphrases captured from the clipboard.
How does BHUNT evade detection? This malware is encrypted by means of two virtual machine packers: Themida and VMProtect, a thing that makes it hard to detect.
The malware executable is also signed using a stolen Piriform digital signature by threat actors. However, the Digitial Signature Information window shows that this is invalid because of a binary mismatch.
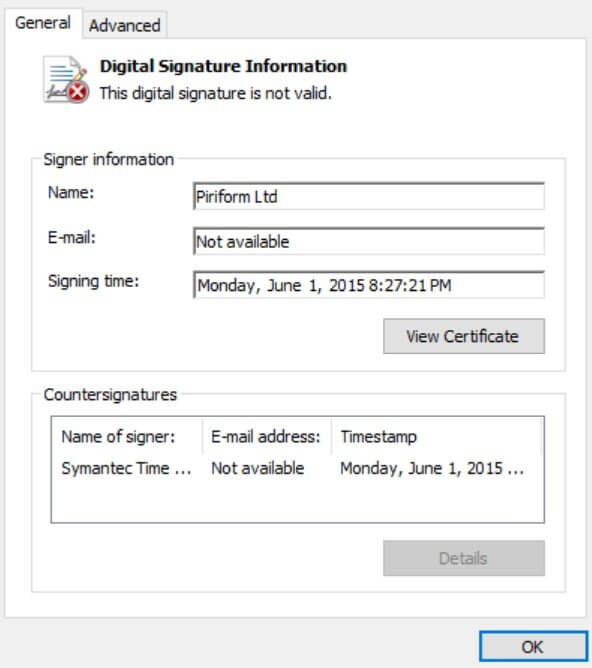
According to the researchers, BHUNT malware is injected into the executable explorer.exe, managing to reach the targeted system by means of KMSpico downloads. KMSpico stands for a well-known utility that allows the illegal activation of Microsoft products.
Which Countries Are Impacted by BHUNT Malware?
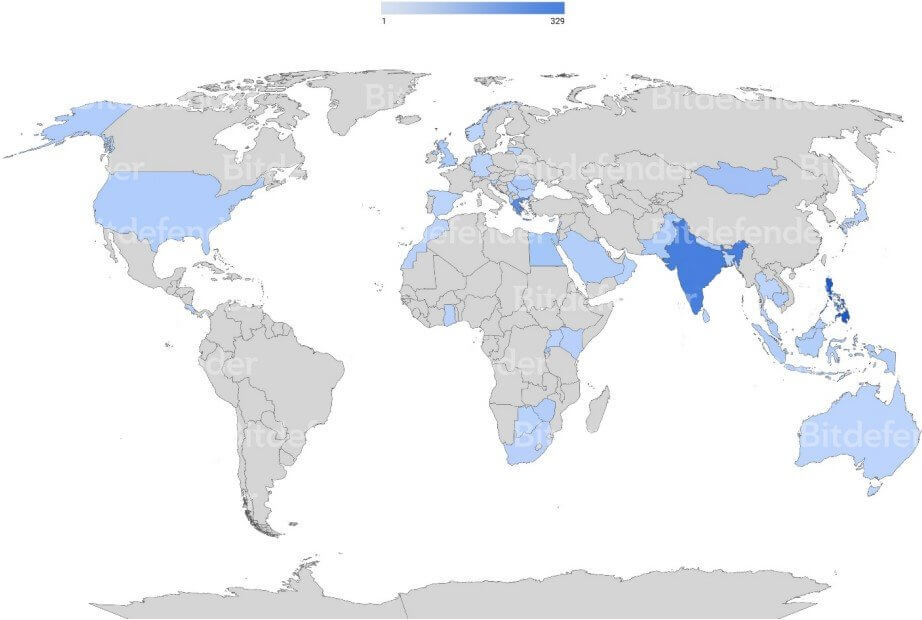
The experts highlighted in their report that the malware shows a global propagation, however, the most impacted country seems to be India, as shown in the heatmap below.
The Modules of BHUNT Malware
Experts stressed the fact that ‘mscrlib.exe’ represents the main BHUNT component which has the role to extract other modules. Every module has a certain goal. For instance, one intends to work on cryptocurrency wallets theft, other perform passwords theft.
Therefore, BHUNT ‘mscrlib.exe’ includes the below modules:
- blackjack – this module steals file contents from wallets, followed by a base64 encoding and uploading to the C2 server
- chaos_crew – works on payload downloading
- golden7 – targets the clipboard to steal passwords from there, then the files are uploaded to the C2 server
- Sweet_Bonanza – targets browsers like Chrome, Opera, Safari, IE, Firefox and steals data from there
- mrpropper – this has the role to work on erasing traces
What Wallets Does the BHUNT Malware Target?
BHUNT malware targets the following crypto wallets:
- Exodus
- Electrum
- Atomic
- Jaxx
- Ethereum
- Bitcoin
- Litecoin
The experts who found this malware also declared that
While the malware primarily focuses on stealing information related to cryptocurrency wallets, it can also harvest passwords and cookies stored in browser caches. This might include account passwords for social media, banking, etc. that might even result in an online identity takeover. (…) BHUNT stealer exfiltrates information about cryptocurrency wallets and passwords, hoping for financial gain. Its code is straightforward and the delivery method is similar to that of existing successful malware, like Redline stealer. (…) The most effective way to defend against this threat is to avoid installing software from untrusted sources and to keep security solutions up to date.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










