Contents:
Cloud service providers, like, for instance, Huawei Cloud, are now targeted by some new variant of a past crypto-mining malware. This is Linux-based and its initial version started its activities in 2020 when the victims were Docker containers.
TrendMicro researchers were the ones who discovered this new version of the known crypto-mining malware. Therefore, it makes use of old features, but this new campaign brings also evolution and enhanced capabilities.
What’s New with This Crypto-mining Malware? The Infection Process
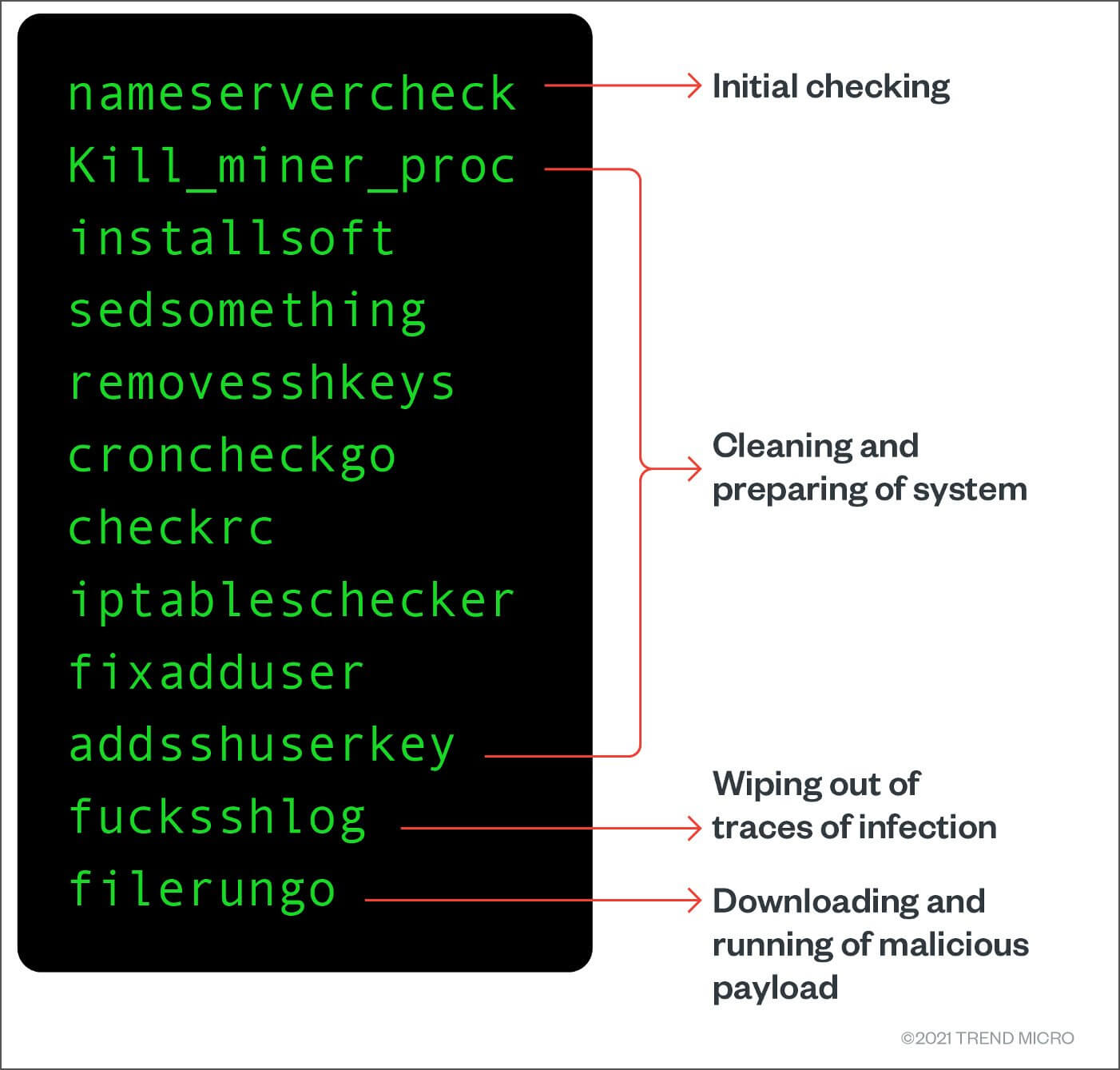
As described by researchers in their report, the recent version of this Linux crypto-mining malware has new features:
- The function that creates firewalls rules was commented out in the new samples;
- It still performs a network scanner dropping. This has the goal of host mapping using API-relevant ports;
- Only cloud environments are targeted this time;
- It looks for and removes previous malicious cryptojacking scripts;
- The coin miner will target a Linux system and infect it, so it removes created users;
- Once the previous users are deleted (created by other hackers), the cryptojackers add their own users;
- These go on the sudoers list, thus device root access is achieved;
- A personal ssh-RSA key is used for system changes and file permissions are changed to “locked”. This makes sure the malware is persistent;
- And this is basically a measure against other hackers, preventing them in the future to fully take over the machine;
- Tor proxy service is then installed. This way network detection cannot spot communications, so connections are anonymously bypassed.
- Then “linux64_shell”, ”ff.sh”, “fczyo”, “xlinux” (some binaries) are dropped but are somehow obfuscated.
- Binaries are so created that they can bypass automated detection and analysis tools;
- Finally, a device foothold is obtained, and the remote systems will be compromised with cryptominer and infected scripts.
Following the same report, researchers have also found what vulnerabilities were scanned during the attack. Therefore, hackers looked for weak SSH passwords, the Oracle WebLogic Server flaw dubbed CVE-2020-14882, weak passwords or unauthorized access related to Redis, PostgreSQL, or MongoDB, and weak passwords of SQLServer and of (FTP), File Transfer Protocol.
Linux cybersecurity attacks usually follow a pattern of crypto miners’ payload deployment. The researchers who discovered this new version of the crypto mining malware have informed Huawei about this threat, but there is no response yet from the company in this sense.
How to Stay Safe?
As always, Heimdal™ has your back. Detect and stop hidden cyber threats and be a step ahead of hackers with our Threat Prevention Tool. This combined with Next-Gen Antivirus will identify even undetectable malware. Or make a combo with all Heimdal™’s solutions as they together offer you ultimate and unified protection, cleaning your threat landscape.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










