Contents:
The coronavirus pandemic is not only the first time in history when a biological virus also affects the cybersecurity industry (through phishing attacks and COVID-19-themed malware) but the way the breakout has been handled so far also resembles how certain IT decision-makers may react when it comes to dealing with security issues.
So far, the crisis has been approached from different angles by governments around the world. The pandemic is now causing major disruptions in the way we live and work, and perhaps, irreversibly. It is an unprecedented health and economic disaster, which puts our collective ability to respond to the test.
How prepared are governments? How about us as citizens? Why don’t we all focus on prevention rather than on dealing with the consequences?
A comparison between decision making in Cybersecurity and the COVID-19 pandemic
If you think about it, in many cases, cyber-attacks and malware behave and spread in ways similar to a pandemic. Some digital threats are even called “viruses”, after all.
But how do cybersecurity leaders generally make decisions compared with how currently government officials are dealing with the COVID-19 pandemic?
Without the intention of trying to oversimplify the complexity and severity of the COVID-19 pandemic, I’ve discovered some similarities that I would like to point out.
#1. Inaction fueled by optimism bias
Even though we like to think of ourselves as rational creatures, it’s in human nature to disregard risk associated with – well, anything…
Why? The optimism bias phenomenon is to be blamed. In short, it refers to the belief that we have lower chances of being affected by negative events than other people and that we are more likely to experience positive events than our peers.
The term was coined by Neil D. Weinstein in 1980, who through his experiment discovered that most college students thought their chances of developing a drinking problem or getting divorced were lower than that of their colleagues. Simultaneously, the majority of these students also believed that the odds of positive things happening to them (such as owning a house and growing old) were much higher.
In a recent article, Marie Helweg-Larsen, Professor of Psychology, argues that certain people are refusing to change their behavior during the current coronavirus pandemic due to optimism bias. For instance, if you don’t believe chances are you may be infected, you might think that interacting with your grandmother won’t be harmful. This way, due to the infection’s uncertainty, you tend to minimize risk.
The perception around risk can be difficult to change. But since social distancing and staying at home are now typically considered the moral thing to do, people may be more likely to change their attitude when thinking about keeping others safe (and not themselves, in particular). So, no longer focusing on your own personal risk may fuel a more protective behavior.
Obviously, not only regular citizens found themselves under the optimism bias since the COVID-19 pandemic has emerged. In the same manner, leaders around the world have been crippled by inertia and tended to underestimate the critical impact the novel coronavirus would have on their countries, healthcare systems, and the economy.
How common is optimism bias in cybersecurity?
Of course, optimism bias can also be observed in the cybersecurity field. In short, this phenomenon prevents some security leaders from taking preventative measures and therefore hinders companies from achieving a good security posture.
The results of a study revealed that security executives are indeed affected by the optimistic bias. The report concludes they thought their risk to be substantially lower than that of the companies they were compared with. Furthermore, they seemed to be aware of the existing risks, yet still can not completely grasp the magnitude of a potential accident.
The same study has shown that subjects, at the very least, acknowledged their interconnectedness with their business partners. Even though they considered themselves to be less prone to risk than other companies, they seemed to perfectly understand that they could themselves become victims due to the third-parties they partnered up with. These dangers are nowadays commonly referred to as Supply Chain Attacks or Vendor Email Compromise (VEC) threats.
How to avoid bias when building your cybersecurity strategy
Biases impact decision-making processes and obviously, the cybersecurity industry is no exception to the rule.
So, how can you, as an IT decision-maker, avoid being under the influence of cognitive biases?
Here are a few points to consider:
- Becoming aware of optimism bias and accepting that the phenomenon is an inherent part of us as humans. This is the first step toward taking impartial, unbiased decisions.
- Looking at real-life examples. Understanding how organizations that match your own profile were impacted by cyberattacks and analyzing how your company would react when faced with a similar scenario. Would it be prepared to deal with an attack or miserably fail? How cyber resilient is your organization?
- Thinking about the overall positive impact of a strong cybersecurity strategy on your business. Now, organizations should not simply begin applying scare tactics upon themselves and should start realizing how threat prevention and mitigation will keep their company up and running.
#2. Testing and micro-segmentation
So far, countries that have proved to be the most successful in managing COVID-19 infections behaved the same way cyber resilient organizations do. And the ones that failed to keep the epidemic under control did not have all the prevention and mitigation measures in place.
For instance, as the epidemic was (not so) slowly increasing, Britons were encouraged to “keep calm and carry on” and let the herd immunity strategy, which was heavily criticized in the end, do the trick. Prime Minister Boris Johnson later admitted that Britain was going through the “greatest public health crisis for a generation” and started implementing some forms of social distancing measures.
After the first American case was announced in late January, when asked if he believed this would turn into a pandemic, President’s Donald Trump response was “No. Not at all. And we have it totally under control. It’s one person coming in from China, and we have it under control. It’s going to be just fine.”
In early March, Trump was still suggesting that the virus was “less serious than the flu” and reassuring people that “It will go away. Just stay calm. It will go away.” Meanwhile, the U.S. was falling behind on testing and some Trump administration officials were responding with untruths, suggesting that anyone who wanted could get tested when in reality, the shortage of testing kits was being revealed. As of March 30, 2020, the U.S. has the most confirmed COVID-19 cases in the world, surpassing China, Italy, and Spain.
In the meantime, South Korea, Singapore, and Taiwan have managed to contain the outbreak due to diligent testing and social distancing measures.
Below you can see the number of Tests conducted vs. Total confirmed cases in different countries around the world:
Along the same lines, the same testing (or monitoring) practices should be followed in cybersecurity.
Should threats remain hidden inside your organization, there will be room for lateral movement and future exploitation. However, the spread of malware infections can be stopped if you put a segmented architecture based on Zero Trust in place. This model originates from the belief that one should never trust anything inside an organization by default and should always verify everything in the first place. Zero trust networks are based upon micro-segmentation, which divides perimeters into small areas so that certain parts of your network remain isolated and have separate access. In case a data breach occurs, micro-segmentation limits further exploitation of your network.
What’s more, simply because people aren’t displaying any visible symptoms of COVID-19, that doesn’t necessarily mean they are not infected and therefore shouldn’t get tested. There have been cases of coronavirus false-negatives so far, which leaves experts worried about this type of inaccuracy amidst the outbreak.
However, even though universal testing may sound utopic due to logistical constraints and shortage of testing kits, the same should not apply when it comes to your organization’s security.
Most nations that have had a hard time enforcing social isolation rules have witnessed COVID-19 infections growing quicker. Italy, for instance, around a week ago, when around 41,000 people were infected and the outbreak was already out of control, was charging 50,000 individuals for breaking isolation laws. Fast forward another week later, the cases in Italy had almost doubled.
On the other hand, after imposing draconian lockdown measures and despite being the outbreak’s original source, China managed to flatten the coronavirus curve. They tried to proactively find infections rather than just passively wait for symptoms to develop. As you may already know, this approach is also considered a best practice in cybersecurity.
What’s more, a study has shown that as human mobility decreased in China after social distancing measures were put in place, so did new infections.
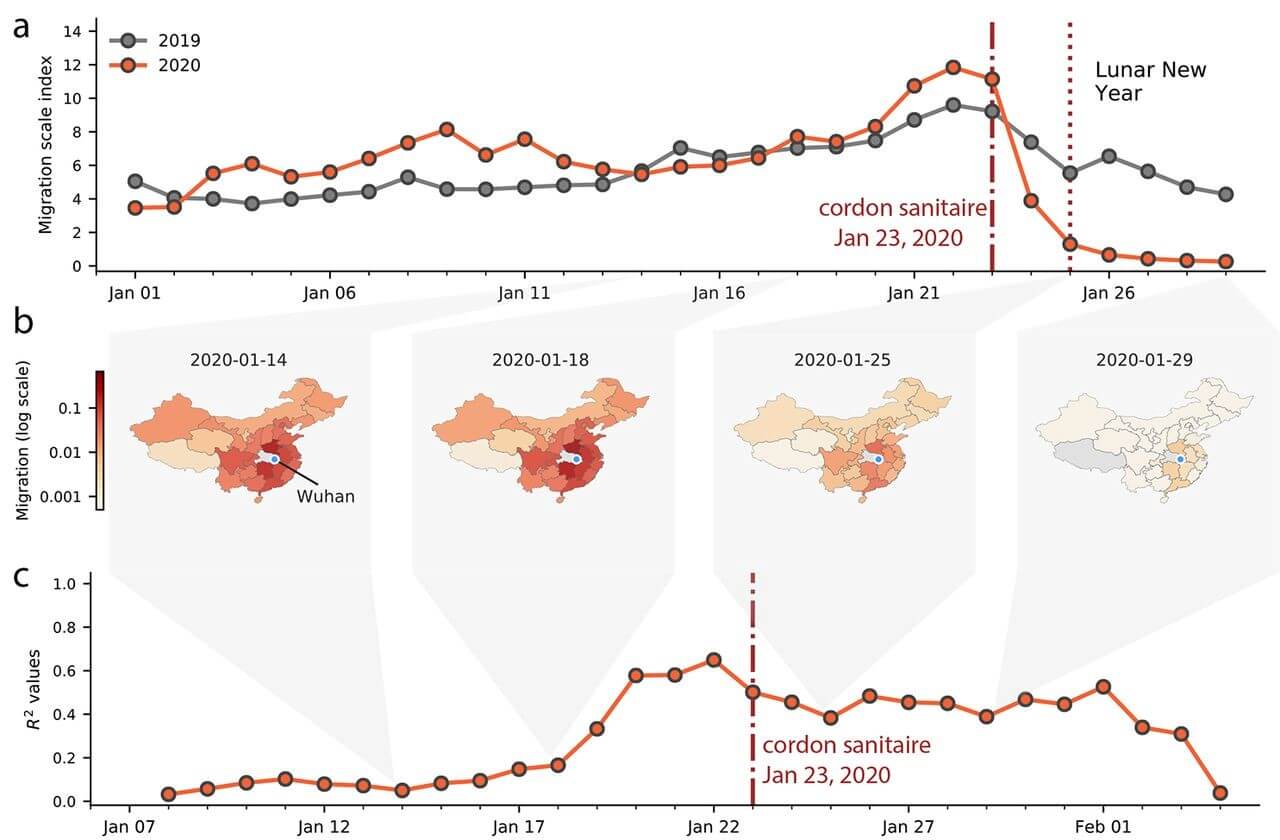
Image source: “The effect of human mobility and control measures on the COVID-19 epidemic in China”, available here
As you can see in Graph a, human mobility dropped after January 23, 2020, and was considerably lower than compared to January 2019, when cordon sanitaire (the health measures aimed at controlling the spread of the disease) was put in place for Wuhan. And after this date, the number of coronavirus cases and infection rate also started decreasing, as you can notice in the charts below:
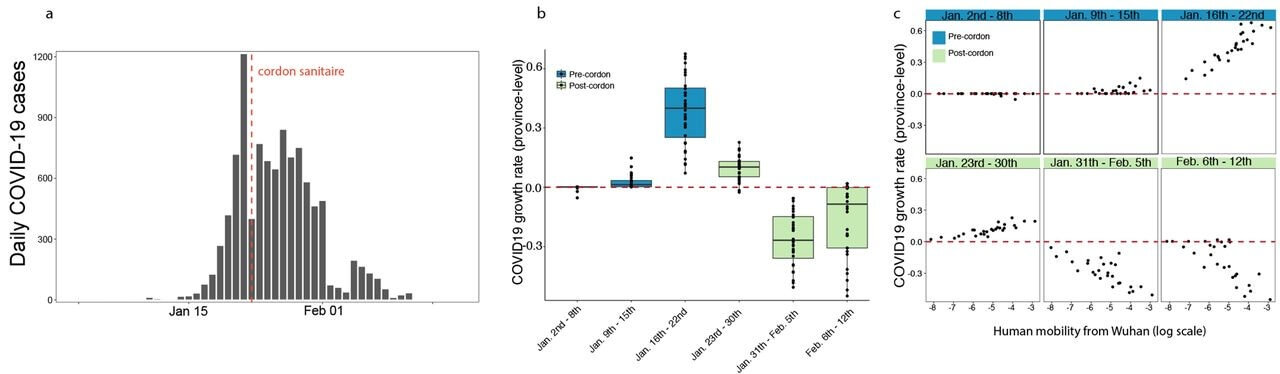
Image source: “The effect of human mobility and control measures on the COVID-19 epidemic in China”, available here
#3. Improving your defenses and mitigating risk
During this critical period, hospitals and governments had to beef up their defenses against COVID-19. Basically, now more medical supplies than ever, such as gloves, gowns, or ventilators, have to be purchased. Needless to say, having the right number of protective equipment is vital. However, unfortunately, many countries are unprepared, even though they should have been able to see a crisis like this one coming.
“When we have done exercises in the past for pandemic preparedness, supply chain issues were a well-documented challenge”, commented Saskia Popescu, an epidemiologist focused on hospital preparedness, for Vox.com. “This is something we’ve known about — maybe not to this extent, but this isn’t a shocker. It’s more surprising that we let it get this bad.”
Knowing that disaster could strike anytime is not to be neglected.
In a similar fashion, the same reasoning can be applied to an organization’s cybersecurity. Since being aware that cyber-attacks and data breaches can linger around the corner, would you not wish to protect your digital assets in the best possible way?
Only through proactive security measures, such as staying on top of your patching or scanning your organization’s incoming and outgoing traffic through DNS filtering coupled with reactive defenses, like using a next-gen Antivirus and then extending your defenses to email security and privileged access rights management, your organization can achieve true cyber resilience.
What organizations can learn from a cybersecurity standpoint
First of all, security leaders should accept that any organization is exposed to cyber threats. After all, it’s a matter of when (not if).
Secondly, another vital step refers to testing (or in other words, gaining visibility inside your organization). This is how you can understand exactly if or which parts of your business are being affected and in case of an existing infection, be able to address it correctly. As I’ve mentioned before, micro-segmentation is recommended. Dividing your network into different security segments with fine-grained security controls will help you isolate areas and limit the spread of a potential infection.
Last, but not least, organizations should operate with a prevention-first mindset and combine proactive and reactive protection measures. Prevention is still the best cure, after all.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Bottom Line
In today’s unprecedented context, how long the COVID-19 pandemic will last is still uncertain. However, what is clear is that it has raised highly complex issues and revealed serious flaws in crisis management in many countries around the world. The outbreak only shows that we are completely unprepared to deal with it. However, it’s (probably) not too late to act now, remain optimistic, and learn how to prevent future outbreaks.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








