Contents:
Bumblebee, a freshly uncovered malware loader, is most probably the Conti syndicate’s latest creation, aimed to replace the BazarLoader backdoor leveraged for ransomware payloads delivery purposes.
According to researchers, the appearance of Bumblebee in phishing attempts in March coincided with a decrease in the use of BazarLoader for distributing file-encrypting malware.
The TrickBot botnet developers created BazarLoader to gain access to victim networks for ransomware assaults. Apparently, TrickBot is working for Conti at the present moment.
According to BleepingComputer, Google’s Threat Analysis Group said in a March report on a threat actor known as ‘Exotic Lily’ that gave early access for Conti and Diavol ransomware operations that the attacker started dropping Bumblebee instead of the normal BazarLoader malware to deploy Cobalt Strike.
How Bumblebee Works
The deployment mechanisms for Bumblebee are the same as for BazarLoader and IcedID, both of which have been detected in the past delivering Conti ransomware, according to Eli Salem, lead threat hunter, and malware reverse engineer at Cybereason.
Proofpoint claims to have discovered various email campaigns spreading Bumblebee within ISO attachments containing shortcut and DLL files, according to a study recently released.
A DocuSign document lure was used in one effort, which lead to a ZIP archive containing a malicious ISO container stored on Microsoft’s OneDrive cloud storage service.
According to Proofpoint, the malicious email also included an HTML file that seemed to be an email to an invoice that allegedly had not been paid.
Below you can see what that email looked like:
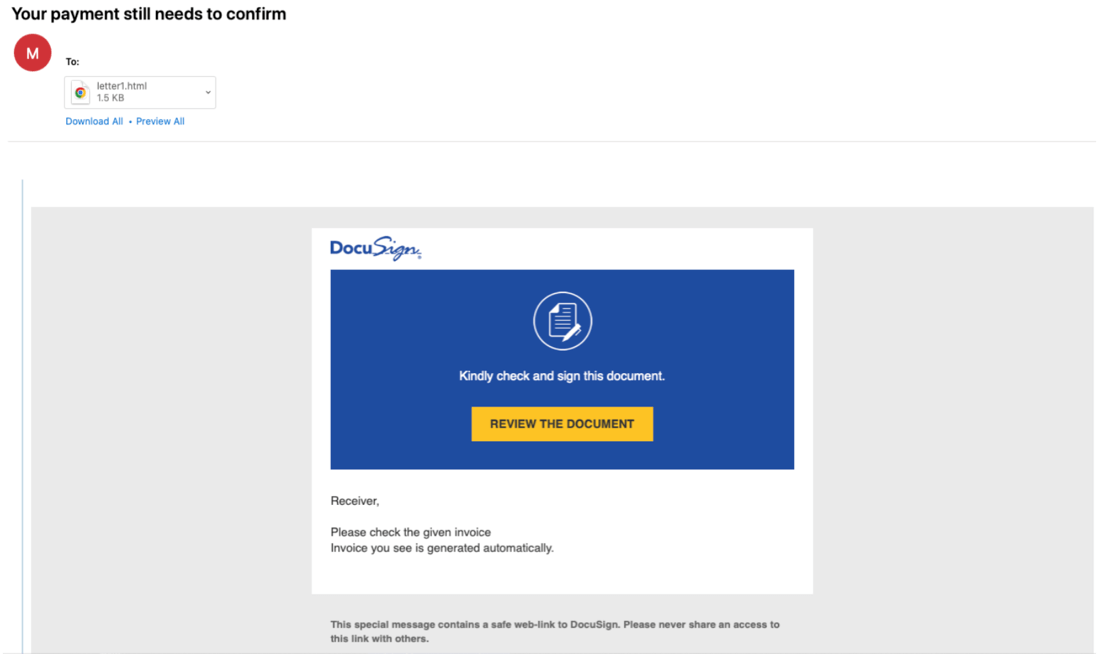
The redirect service utilized in the HTML file relied on the Prometheus TDS (traffic distribution service), which filters downloads based on the victim’s timezone and cookies. The malicious ISO hosted on OneDrive was likewise the eventual destination.
Proofpoint discovered a campaign in March that distributed Bumblebee via contact forms on a target’s website. The emails claimed that the website featured stolen photos and gave a link to an ISO file that included the malware.
The ISO file contained files named “ATTACHME.LNK” and “Attachments.dat”. If ran, the shortcut file “ATTACHME.LNK” executed “Attachments.dat” with the correct parameters to run the downloader, Bumblebee. (…) Proofpoint researchers attributed this campaign with high confidence to the cybercriminal group TA579. Proofpoint has tracked TA579 since August 2021. This actor frequently delivered BazaLoader and IcedID in past campaigns.
Bumblebee is a “new, highly sophisticated malware loader,” according to researchers, that combines extensive evasion techniques and anti-analysis tricks, including complex anti-virtualization methods.
Bumblebee’s authors copied the full anti-analysis code from the publicly available al-khaser PoC’malware’ application, according to a technical analysis published on Thursday by Eli Salem.
The virus searches for different tools for dynamic and static analysis, and it tries to identify any form of virtualized environment, according to Salem’s code analysis.
Bumblebee Commands
Proofpoint discovered that the Bumblebee loader includes the following commands:
- Shi: this represents a shellcode injection;
- Dij: this is about a DLL injection in other processes’ memory;
- Dex: pointing out to a download executable;
- Sdl: referring to unstalling loader;
- Ins: Visual Basic Script is enabled to persist for Bumblebee loading purposes.
Bumblebee was investigated by malware experts at Proofpoint and Cybereason, who found code, distribution mechanisms, and dropped payloads that were comparable to the TrickBot malware.
It seems that Bumblebee employs the same evasion strategy for RapportGP.DLL that TrickBot does for its web-inject module.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








