Contents:
‘0mega,’ a brand-new ransomware group, targets businesses all over the world with double-extortion attacks and asks for millions of dollars in ransom.
0mega made its debut in May 2022, and since then, the novel ransomware campaign has targeted an impressive number of victims.
More on 0mega Ransomware
According to BleepingComputer, no ransomware sample for the 0mega operation has been discovered so far, so there is little information about the encryption method used.
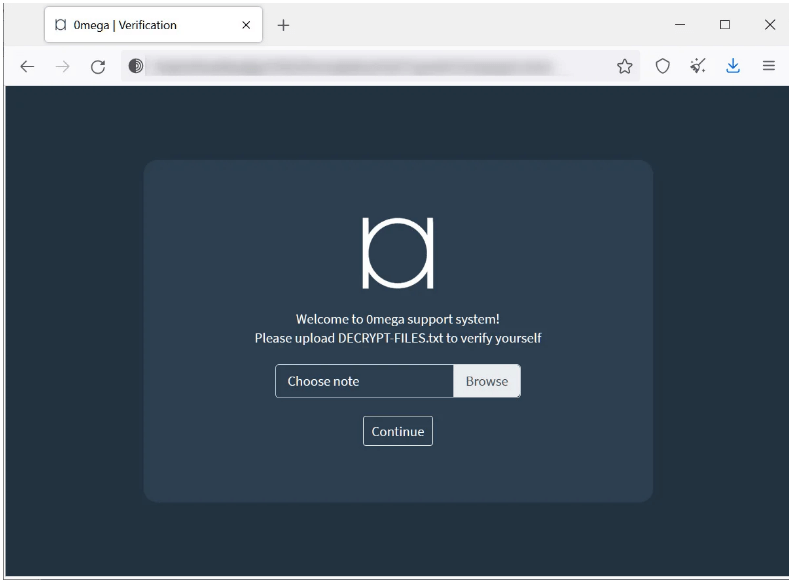
What we do know is that the ransomware adds the.0mega extension to the names of the encrypted files and generates ransom messages with the filename DECRYPT-FILES.txt.
Some notes also contain threats about how the 0mega ransomware group will announce business partners and trade associations about the attack if the companies fail to pay the ransom.
A link to a Tor payment negotiation webpage with a “support” chat is also provided in these ransom notes so that victims can get in touch with the threat actors. In order to access the page, victims are required to upload their ransom notes, which include a unique Base64-encoded blob used by the site to recognize the victim.
Like virtually every other ransomware campaign that targets organizations, 0mega has a specific website for data leaks where cybercriminals post stolen information if their victims refuse to pay the requested ransom.
The ransomware gang’s leak site is currently hosting 152 GB of stolen information belonging to an electronics repair firm they attacked in May 2022.
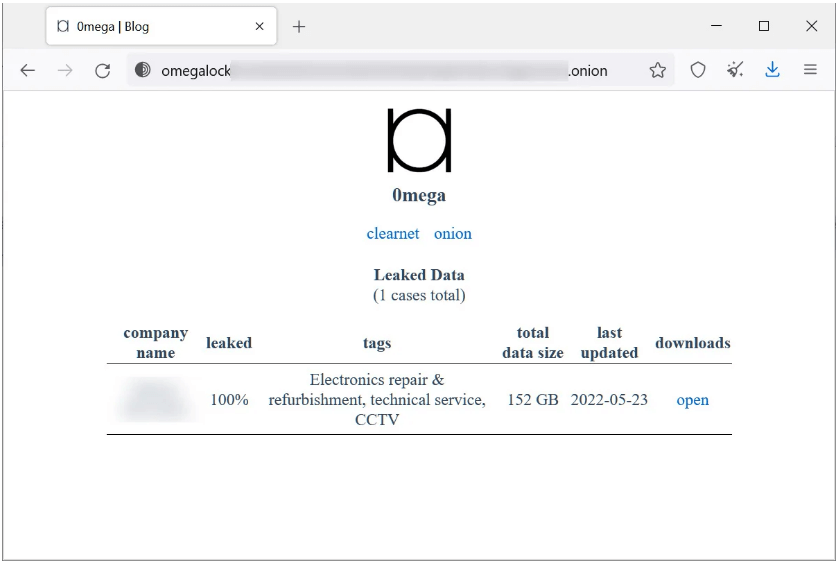
BleepingComputer reports that an additional victim was identified last week but has since been eliminated, suggesting that the business may have paid a ransom.
However, last week there was an additional victim that has since been removed, indicating that the company may have paid a ransom.
However, last week there was an additional victim that has since been removed, indicating that the company may have paid a ransom. Given that this campaign is still in its early stages, future attacks are likely to increase, so we will definitely come back with more information on this new ransomware organization.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










