Contents:
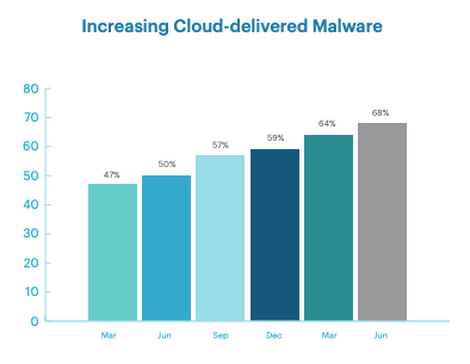
Cybersecurity Company Netskope issued the fifth edition of its Cloud and Threat Report that deals with the cloud data risks, menaces, and trends they see throughout the quarter.
According to the security firm report, cloud storage apps are responsible for more than 66% of cloud malware delivery.
In Q2 2021, 43% of all malware downloads were malicious Office docs, compared to just 20% at the beginning of 2020. This increase comes even after the Emotet takedown, indicating that other groups observed the success of the Emotet crew and have adopted similar techniques.
Collaboration apps and development tools account for the next largest percentage, as attackers abuse popular chat apps and code repositories to deliver malware. In total, Netskope detected and blocked malware downloads originating from 290 distinct cloud apps in the first half of 2021.
35% of All Workloads Vulnerable to the Public Internet Inside AWS, Azure, and GCP
Cybersecurity specialists explained that threat actors spread malware via cloud applications “to bypass blocklists and take advantage of any app-specific allow lists.”
Those who provide cloud services usually eliminate most malware instantly, but some hackers have discovered methods to do significant damage in the short time they spend in a system without being noticed.
Researchers stated that about 35% of all workloads are also vulnerable to the public internet inside AWS, Azure, and GCP, with public IP addresses that are accessible from anywhere on the internet.
“A popular infiltration vector for cybercriminals” are RDP servers which were exposed in 8.3% of workloads.
The average organization with anywhere between 500 and 2000 staff members now uses 805 individual apps and cloud services, with 97% of those being “unmanaged and often freely adopted by business units and users.”
The report also notes that “97% of cloud apps used in the enterprise are shadowing IT, unmanaged and often freely adopted by business units and users.”
Another concern is related to the employee’s habit of authorizing at least one third-party app in Google Workspace. The cybersecurity firm’s report states employees leaving a company upload three times more data to their personal apps in the final month of working there.
The analysts also say that remote work is still in full swing as of the end of June 2021, with 70% of study participants still working from home.
At the beginning of the pandemic, when users began working from home, we saw a spike in users visiting risky websites, including adult content, file sharing, and piracy websites.
Over time, this risky web surfing subsided as users presumably became more accustomed to working from home, and IT teams were able to coach users on acceptable use policies.
As stated by chief security scientist and advisory CISO at ThycoticCentrify Joseph Carson, the switch to a hybrid work environment in 2020 meant that cybersecurity had to evolve from being perimeter and network-based to one that is focused on cloud, identity, and privileged access management.
Organizations must continue to adapt and prioritize managing and securing access to the business applications and data, such as that similar to the BYOD types of devices, and that means further segregation networks for untrusted devices but secured with strong privileged access security controls to enable productivity and access.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








