Contents:
When you hear the term cloud computing, know that it has little to do with the famous cloud number 9 some sing about – it is a key concept in the current and future evolution of technology. Like everything else, though, it has its strengths and downsides, so let us have a closer look at some of the most relevant cloud computing threats and vulnerabilities, not without first defining the notion. According to Edwards Zamora,
Cloud computing consists of the set of systems and services working in unison to provide distributed, flexible, and measurable resources to consumers of cloud services. The National Institute of Standards and Technology (NIST) defines cloud computing as a model that consists of on-demand self-service, broad network access, resource pooling, rapid elasticity and measured service (Mell & Grance, 2011). Essentially, cloud computing allows consumers to provision for themselves resources available from a cloud services provider. Consumers are able to access their cloud resources from a wide variety of devices including mobile, thin clients, and traditional desktops. […] Physical and virtual systems are combined to provide consumers with resources dynamically without the user needing to know the details of how it all works.
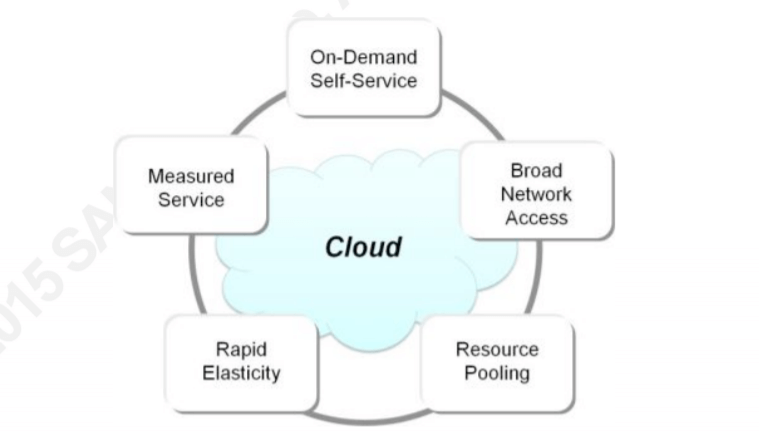
Source: Cloud Testing Methodology, Edward Zamora
As i-SCOOP notes:
Cloud computing is also one of the essential enablers of Industry 4.0, has been shaping the software and business applications market for over a decade, has an important place in the development of the Internet of Things and is essential to manage data, including big data, to give just a few examples.
Cloud technology is also used for hosting popular services like e-mail, social media, business applications. The average person checks their phone 221 times per day to look at e-mails, browse the Internet or use smartphone applications. Besides, 82% of large enterprises are now using cloud computing and up to 78% of small businesses are expected to adopt cloud technology in the next few years.
Depending on the delivery methods, the 4 main cloud delivery models are the following:
Public Cloud – owned and operated by a third-party provider, can be used by everyone, so it’s publicly accessible. Examples: Microsoft Azure, Google. Private Cloud – a distinct cloud, whose main key trait is privacy, which can be used in several ways by a specific organization. Hybrid Cloud – a computing environment which combines a public cloud and a private one (or more) by allowing the exchange of data and applications between them. Community Cloud – a cloud used by a community of people with, possibly, shared or common profiles, for a common shared purpose.
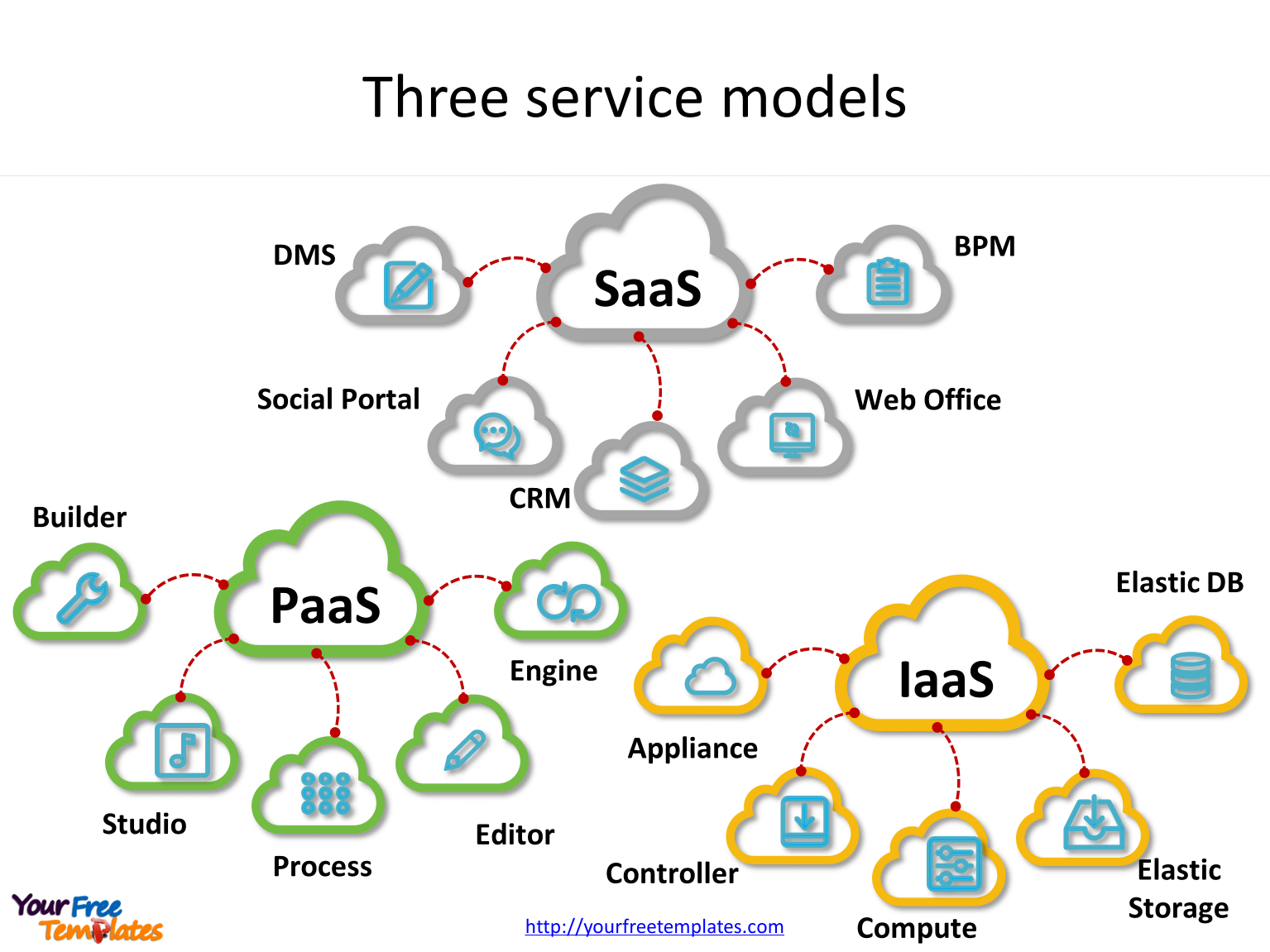
Depending on the types of services and resources a customer subscribes to, here are the 3 main cloud services available:
Software as a Service (SaaS). The choice of most businesses, SaaS utilizes the Internet to deliver applications that are managed by a third-party vendor to the users. Many SaaS applications run directly through the web browser, meaning they do not require to be downloaded or installed. SaaS is the best option for: – short-term projects that require quick, easy and affordable collaboration. – startups or small companies that need to launch e-commerce quickly. – applications that need both web and mobile access. – applications that aren’t needed very often. Platform as a Service (PaaS). Cloud platform services deliver a platform that can be modified by developers to create customized applications. PaaS is particularly useful when: – multiple developers are working on the same development project. – other vendors must be included, PaaS providing great speed and flexibility to the whole process. – you need to create customized applications. – you are rapidly developing and deploying an application, because it can reduce costs and simplify challenges. Infrastructure as a Service (IaaS). Cloud infrastructure services are made of highly scalable and automated compute resources. IaaS is self-service for accessing and monitoring computers, networking, storage and so on, allowing businesses to purchase resources on-demand. IaaS is most advantageous: – for small companies or startups, to avoid spending time and money on purchasing and creating hardware and software. – for larger companies, who want to purchase only what they actually consume / need. – for companies who experience rapid growth and want to change out easily specific hardware and software.
Among the benefits of cloud computing we mention:
A. Mobility
Cloud computing allows mobile access to your company’s data via various types of devices – smartphones, tablets, laptops, which is particularly useful in the context of the Coronavirus and work from home policy.
B. Easy to scale server resources
Most cloud servers provide access to an intuitive site management dashboard where you can view your site’s performance in real-time. Server resources can be scaled up or down on the spot, without having to wait for your hosting provider’s approval.
C. Safety from server hardware issues and loss prevention
By choosing a cloud service you make sure you avoid any physical server issue like hacking, hardware failure or system overload. We could also include here natural disasters or fires that could destroy your equipment. Most cloud-based services provide data recovery for all kinds of emergency scenarios, from natural disasters to power outages.
D. Faster website speed and performance
Usually, a cloud server should equal whipping speed, which will allow you to increase your site’s capacity, providing you with a great competitive edge.
E. Automatic software updates
Any busy man knows how irritating having to wait for system updates to be installed is. Instead of forcing an IT department to perform a manual, organisation-wide, update, cloud-based applications automatically refresh and update themselves.
F. Sustainability
If you aim to have a positive impact from an environmental point of view too, bear in mind that by choosing cloud computing you help cut down on paper waste, improve energy efficiency and reduce commuter-related emissions. As I already mentioned, cloud computing can bring amazing benefits to companies, but it also has its downsides. If we want to discuss cloud computing threats and vulnerabilities, though, we must not forget the context of the times we live in. According to Gartner,
The shortage of technical security staff, the rapid migration to cloud computing, regulatory compliance requirements and the unrelenting evolution of threats continue to be the most significant ongoing major security challenges. However, responding to COVID-19 remains the biggest challenge for most security organizations in 2020. “The pandemic, and its resulting changes to the business world, accelerated digitalization of business processes, endpoint mobility and the expansion of cloud computing in most organizations, revealing legacy thinking and technologies,” says Peter Firstbrook, VP Analyst, Gartner.
Here are the main cloud computing threats and vulnerabilities your company needs to be aware of:
1. Lack of Strategy and Architecture for Cloud Security
Many companies become operational long before the security strategies and systems are in place to protect the infrastructure, in their haste to migrate to the cloud.
2. Misconfiguration of Cloud Services
Misconfiguration of cloud services is a growing cloud computing threat you must pay attention to. It is usually caused by keeping the default security and access management settings. If this happens, important data can be publicly exposed, manipulated or deleted.
3. Visibility Loss
Cloud services can be accessed through multiple devices, departments and geographic places. This kind of complexity might cause you to lose sight of who is using your cloud services and what they are accessing, uploading or downloading.
4. Compliance Violation
In most cases, compliance regulations require your company to know where your data is, who has access to it, how it is processed and protected. Even your cloud provider can be asked to hold certain compliance credentials. Thus, a careless transfer of your data to the cloud or moving to the wrong provider can bring potentially serious legal and financial repercussions.
5. Contractual Breaches
Any contractual partnerships you have or will develop will include some restrictions on how any shared data is used, how it is stored and who has authorized access to it. Unknowingly moving restricted data into a cloud service whose providers include the right to share any data uploaded into their infrastructure could create a breach of contract, which could lead to legal actions.
6. Insecure Application User Interface (API)
Operating systems in a cloud infrastructure is sometimes done through an API that helps to implement control. API’s are sets of programming codes that enable data transmission between one software product and another and contains the terms of this data exchange. Application Programming Interfaces (API) have two components: technical specification describing the data exchange options, in the form of a request for processing and data delivery protocols, and the software interface written to the specification that represents it.
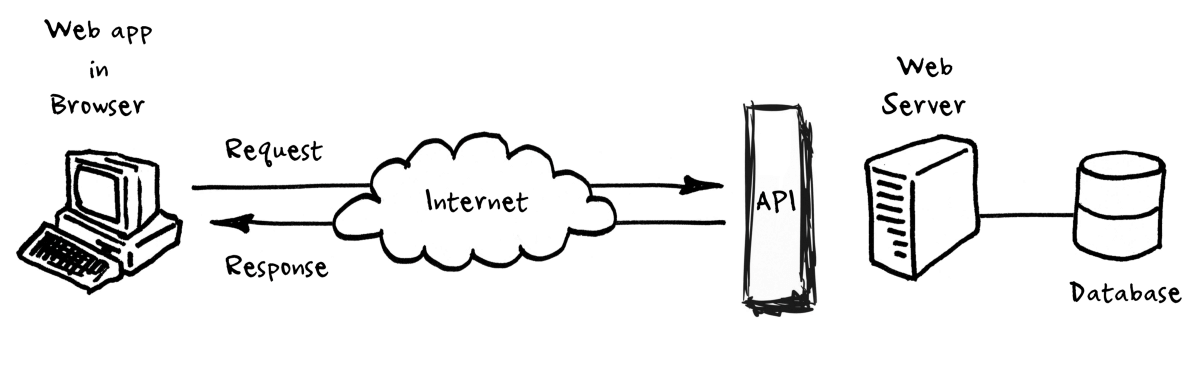
Source: Medium
Any API can be accessed internally by your staff and externally by consumers – the external-facing API can represent a cloud computing threat. Any insecure external API might become a gateway for unauthorized access to cybercriminals who might steal data and manipulate services.
7. Insider Threats
Your employees, contractors and business partners can, without having any malicious intent, become some of your biggest security risks due to a lack of training and negligence, as we have already shown. Moving to the cloud introduces a new layer of insider threat, from the cloud service provider’s employees. Since it is clear, although there are so many threats and vulnerabilities, that cloud computing could be really helpful to any company if used correctly and that it is here to stay, let us now mention some of the safety measures you can take.
Here’s what you can do to efficiently combat cloud computing threats and vulnerabilities:
1. Manage User Access
Not every employee needs access to every application, file or bit of information. By setting proper levels of authorization you make sure that everyone gets to view or manipulate only the data and the applications necessary for them to do their job.
2. Deploy Multi-Factor Authentication
Stolen credentials are one of the most common methods hackers use to get access to your company’s online data. Protect it by deploying multi-factor authentication and make sure that only authorized personnel can log in and access data.
3. Detect Intruders with Automated Solutions that Monitor and Analyze User Activity
Abnormal activities can indicate a breach in your system, so try using automated solutions that can help you spot irregularities by monitoring and analyzing user activities in real-time. This is a very efficient tool in the combat against cloud computing threats and vulnerabilities.
4. Consider Cloud to Cloud Back-Up Solutions
The chances of losing data because of your cloud provider’s mistake are pretty low – unlike losing them due to human error. Check with your cloud provider for how long they store deleted data, if there are any fees to restore it or turn to a cloud to cloud back-up solution.
5. Provide Anti-Phishing Training for Employees
The Heimdal™ Security team is very fond of education – we really believe that knowledge is power and that many things can be confronted if we know about them and try our best to prevent them. It goes without saying that we recommend you to discuss with all your employees about the dangers of phishing. (We actually wrote more about this here, here and here.)
6. Develop an Off-Boarding Process to Protect against Departing Employees
Always make sure that the employees that leave your company can no longer access your systems, data or customer information by revoking all the access rights. You can manage this internally or outsource the task to someone who knows how to implement the process.
Heimdal™ Security can also help. Here’s how!
In our opinion, you can choose between 3 approaches – or opt for all of them if you want top cybersecurity for your company: Manage user access with Heimdal™ Privileged Access Management, our Privileged Access Management (PAM) software which helps your organization achieve not just better cybersecurity, but also full compliance and higher productivity. Heimdal™ Privileged Access Management will allow your system admins to approve or deny user requests from anywhere or set up an automated flow from the centralized dashboard. Moreover, all the activities will be logged for a full audit trail. Heimdal® Privileged Access
Management
Heimdal® Email Security


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











