Contents:
Cisco has confirmed that the Yanluowang ransomware gang infiltrated their corporate network in May and that the attacker attempted to extort money from them by threatening to post stolen material online.
The corporation disclosed that the threat actors could only access a Box folder that was connected to a hacked employee’s account to gather and take non-sensitive material.
On May 24, 2022, Cisco identified a security incident targeting Cisco corporate IT infrastructure, and we took immediate action to contain and eradicate the bad actors. In addition, we have taken steps to remediate the impact of the incident and further harden our IT environment. No ransomware has been observed or deployed and Cisco has successfully blocked attempts to access Cisco’s network since discovering the incident.
According to their statement, the malicious parties posted a list of the files from this security breach on the dark web on August 10. Cisco has been aggressively gathering data about the malicious attacker prior to this disclosure to aid in safeguarding the security community.
How Did the Breach Happen?
The Yanluowang threat actors hijacked a Cisco employee’s personal Google account, which contained credentials synchronized from their browser, and used those credentials to enter Cisco’s network.
Through MFA fatigue and a series of sophisticated voice phishing attacks carried out by the Yanluowang gang under the guise of reputable assistance businesses, the attacker persuaded the Cisco employee to accept multi-factor authentication (MFA) push alerts.
The cybercriminals were able to access the VPN in the scope of the targeted user after ultimately tricking the victim into approving one of the MFA alerts. Once the Yanluowang operators had acquired access to the corporate network, they expanded laterally to domain controllers and Citrix servers.
After establishing access to the VPN, the attacker then began to use the compromised user account to logon to a large number of systems before beginning to pivot further into the environment. They moved into the Citrix environment, compromising a series of Citrix servers and eventually obtained privileged access to domain controllers.
Upon obtaining domain admin access, they deployed a number of payloads, including a backdoor, on infected systems and collected further information using enumeration tools including ntdsutil, adfind, and secretsdump.
In the end, Cisco discovered them and banned them out of its environment, but they persisted in trying to get back in over the coming weeks.
Hackers Allegedly Exfiltrated Cisco Data
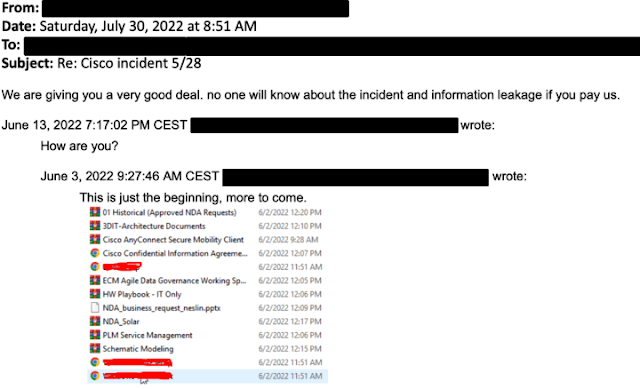
A directory listing of files purportedly stolen during the attack was sent over email to BleepingComputer last week by the threat actor responsible for the Cisco intrusion.
3.100 files totaling 2.75GB of data, were exfiltrated, according to the threat actor. Non-disclosure agreements, data dumps, and engineering drawings are present in a large number of these files.
A redacted NDA agreement that was obtained in the attack was also supplied to BleepingComputer by the threat actors as evidence of the incident and a “hint” that they had infiltrated Cisco’s network and taken files.

No Ransomware Deployment
Cisco added that despite the Yanluowang gang’s reputation for encrypting the files of their victims, it did not discover any signs of ransomware payloads during the attack.
While we did not observe ransomware deployment in this attack, the TTPs used were consistent with “pre-ransomware activity,” activity commonly observed leading up to the deployment of ransomware in victim environments. Many of the TTPs observed are consistent with activity observed by CTIR during previous engagements. Our analysis also suggests reuse of server-side infrastructure associated with these previous engagements as well. In previous engagements, we also did not observe deployment of ransomware in the victim environments.
American store Walmart, whose systems the Yanluowang gang claims to have recently infiltrated, has rejected the hack and told BleepingComputer that it has not discovered any proof of a ransomware attack.
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










