Contents:
In a recent series of cyberattacks, suspected Chinese hackers targeted government and affiliated bodies across the globe. The threat actors exploited a zero-day vulnerability in Barracuda’s Email Security Gateway (ESG). Organizations in the Americas were significantly affected.
Nearly one-third of the compromised devices in this campaign belonged to governmental entities, with most breaches occurring between October and December 2022, according to Mandiant’s newest report.
The analysis highlighted the widespread targeting of North American local governments, with the rate reaching 17% for U.S.-specific attacks.
Cyberespionage, the Main Objective
Cyberespionage appears to be the main objective, with the attackers (identified as UNC4841) specifically extracting data from high-profile users in the government and tech sectors, explains Bleeping Computer.
On May 20, Barracuda alerted customers about the vulnerability, also initiating a patch on all susceptible devices. By the end of the month, it became clear that this vulnerability had been exploited since at least October 2022, allowing hackers to install new malware and steal data.
A week later, customers were warned that they must replace all hacked appliances, including those that had been patched (Mandiant estimates that only about 5% of all ESG appliances were compromised in the attacks).
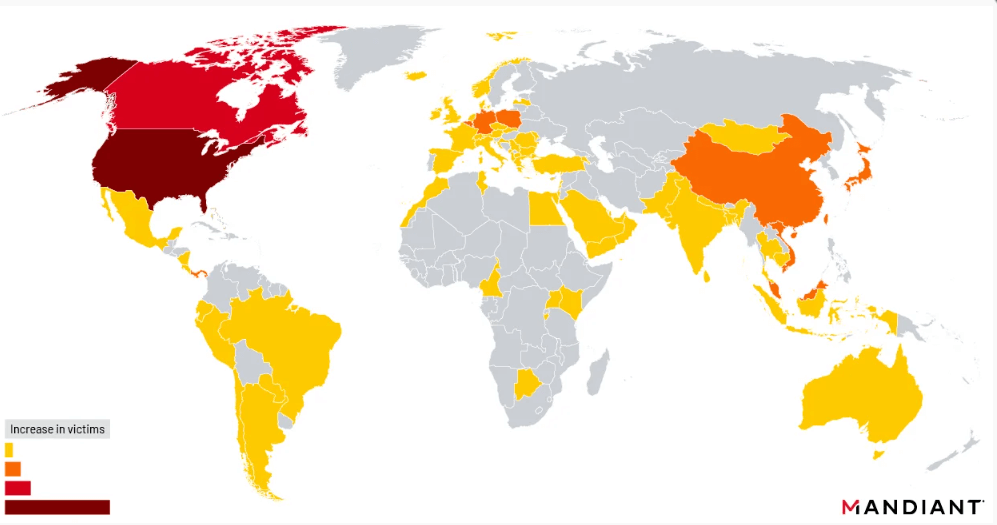
Affected Customers (Source)
The attackers deployed unknown malware, like SeaSpy and Saltwater, and a tool called SeaSide to remotely access systems. Furthermore, CISA shared insights about the Submarine (or DepthCharge) and Whirlpool malware, used in these attacks to retain control, especially after Barracuda’s advisory on May 20.
The cybersecurity company emphasized the strategic nature of the operation, pointing to the attacker’s readiness to tackle potential disruptions.
Despite this operation’s global coverage, it was not opportunistic, and that UNC4841 had adequate planning and funding to anticipate and prepare for contingencies that could potentially disrupt their access to target networks.
Extract from Mandiant’s Report (Source)
FBI: Barracuda ESG Appliances Are Still a Target
Despite Mandiant and Barracuda not discovering new ESG compromises after the patches, the FBI issued a warning that the patched systems are still susceptible to breaches.
The FBI corroborated Barracuda’s cautionary note, encouraging users to change hacked devices promptly and review their networks for potential vulnerabilities. They also advised updating privileged credentials to prevent attackers from retaining access.
According to the FBI, “All affected Barracuda ESG appliances, including those patched by Barracuda, remain vulnerable.” They confirmed that the continued network vulnerabilities are likely due to cyber actors linked to the People’s Republic of China (PRC).
More than 200 thousand organizations, including government agencies and well-known corporations, rely on Barracuda’s security solutions.
The full report on “UNC4841 Operations Following Barracuda ESG Zero-Day Remediation” is available here.
The FBI’s announcement is available here.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










