Contents:
The American fast-food restaurant chain Chick-fil-A is looking into “suspicious activity” linked to some of its customers’ accounts.
The company created a support page with advice for clients who notice any strange activity on their accounts, such as mobile orders placed without their approval, or loyalty points used to redeem or gift rewards without their consent.
We are investigating suspicious activity on some customer accounts. We are committed to protecting customers’ data and are working quickly to resolve the issue.
Customers are urged to change their passwords if they notice anything out of the ordinary. Furthermore, they should delete their stored credit or debit cards from their Chick-fil-A One accounts by heading to the Account option in the Chick-fil-A app and selecting “Manage payment methods.”
Cybersecurity researcher Dominic Alvieri was the first to tweet about the alert, which was displayed on Chick-Fil-A on Friday.
Chick-fil-A Accounts, for Sale on the Dark Web
According to a threat intelligence researcher, the hijacked accounts are used with disposable email addresses to buy food in widespread attack. Based on the account balance, linked payment method, or Chick-fil-A One points (rewards points), some of the stolen accounts are being sold for $2 to $200.
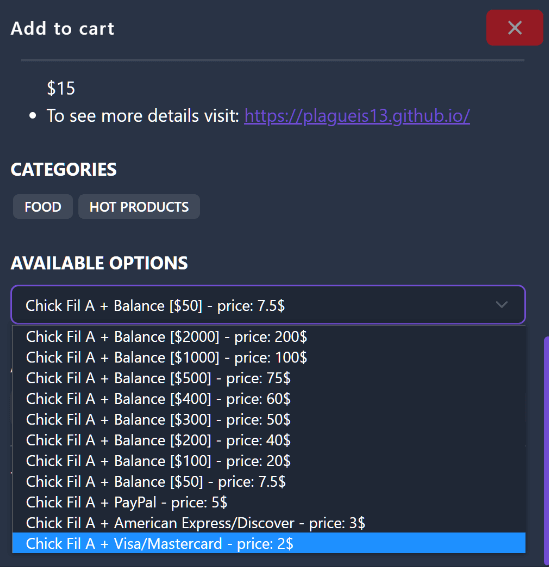
Customers have also reported on social networks that their accounts were hacked and their loyalty points were depleted, explains Bleeping Computer.
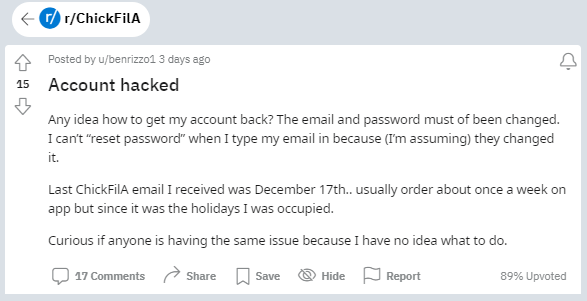
To prevent account hijacking, Chick-Fil-A has disabled the creation of new accounts and banned the use of disposable email addresses.
The Chick-fil-A support page for customers who observe suspicious activity on their accounts is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










