Contents:
Earlier this week, Kingfisher’s name appeared on the LockBit ransomware group’s leak site alongside claims of 1.4TB of the company`s data having been stolen, including personal details of employees and customers.
The company acknowledged the attack on its IT systems but claims threat actors couldn`t have stolen as much data as they claimed.
More on the Matter
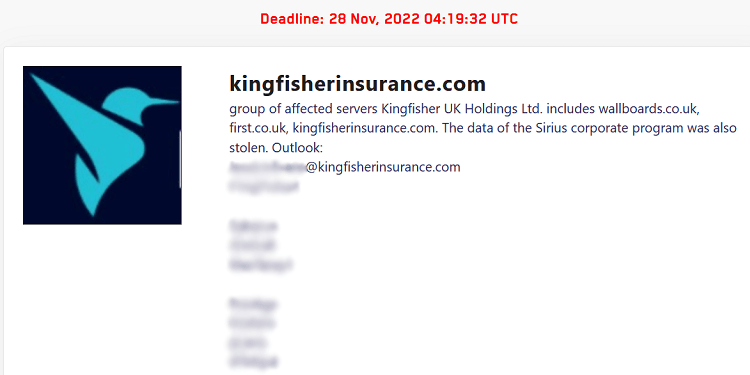
On Monday, claims about a breach targeting the servers of the British Kingfisher Insurance company have surfaced on LockBit’s leak site. According to the ransomware gang, the dataset includes personal data of employees and customers as well as contacts and corporate mail archives belonging to Kingfisher, as well as well as one of the company’s vehicle insurance brands, First Insurance.
The threat actors posted several email addresses that appear to belong to Kingfisher Insurance staff, as well as passwords to several management system accounts, such as Workday and Access.
Announcement on LockBit’s leak site.
Cybernews describes Kingsfisher as a UK insurance company owning several prominent UK-based insurance brands, such as Classic Insurance Services, ClubCare Insurance, Cork Bays & Fisher, First Insurance to name a few.
The British company’s IT team reportedly took to blocking all external access and affected servers were brought offline as soon as the cyberattack became known, but the investigation concluded that business operations have not been impacted.
It is impossible for the criminal group behind this incident to have taken 1.4TB of data from the servers they indicate.
LockBit as a Threat
A report by threat intelligence firm Digital Shadows shows that in the second quarter of 2022, LockBit was the most active group in the cybercrime underworld holding a record for the highest number of victims in a quarter, specifically 231 victims.
LockBit has been a constant threat since 2019, working as a ransomware-as-a-service (RaaS) by recruiting threat actors to breach networks and encrypt devices, while also releasing a second and even a third generation of malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







