Contents:
A new Linux malware dubbed BPFdoor has been recently identified. Its targets have been Linux and Solaris systems and what’s more, is that it has passed unnoticed for over 5 years.
More Details on the BPFdoor Malware
BPF can be described as a Linux/Unix backdoor that lets hackers establish a connection to a Linux shell remotely and was detailed in a report by DoublePulsar and also in a report by Sandfly Security. This way, threat actors can further achieve access to a device that is compromised.
This malware shows the following features:
- doesn’t have to open ports;
- firewalls cannot block it;
- has the capacity to reply to commands from any web-based IP address.
Because BPFDoor doesn’t open any inbound network ports, doesn’t use an outbound C2, and it renames its own process in Linux (so ps aux, for example, will show a friendly name) it is highly evasive.
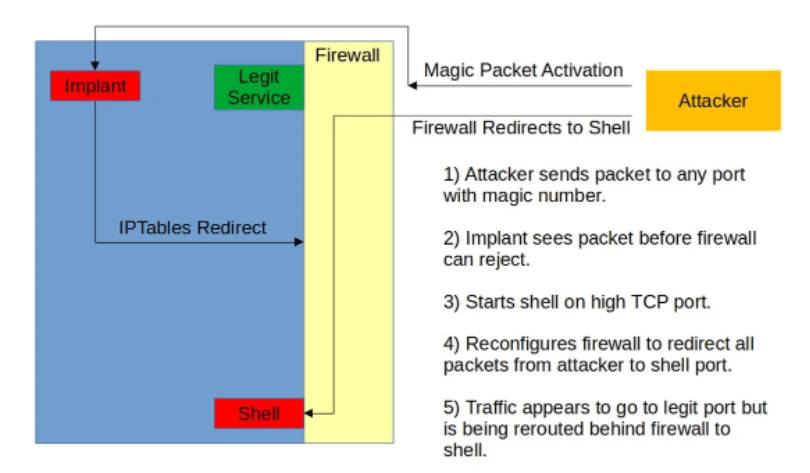
The malware is also a passive backdoor. What does that mean? It can monitor one or more ports for incoming packets from one or more hosts, which threat actors can use to remotely execute commands on the infiltrated network.
A Berkeley Packet Filter sniffer is employed by this backdoor which operates at the network layer interface. This way, it can see any network traffic as well as transmit packets to any destination. This also triggers its capacity to bypass firewalls.
The malware is suited for Solaris SPARC and Linux systems as well as it can be ported to BSD, according to BleepingComputer following a statement from Craig Rowland, Sandfly Security’s founder.
Also, Kevin Beaumont from DoublePulsar, says that a “magic” password is employed for the implant’s actions control purposes.
Operators have access to a tool which allows communication to the implants, using a password, which allows features such as remotely executing commands. This works over internal and internet networks.
Only ICMP, UDP, and TCP packets are parsed by BPFdoor, which looks for a certain data value. But what makes BPFdoor noticeable is its capacity to monitor any port for the magic packet. This happens even with ports employed by legitimate services, for instance, FTP or SSH.
In the case when the TCP and UDP packets include this “magic” data the backdoor looks for and a valid password, BPFdoor starts performing a supported command, for example, bind or reverse shell configuration.
Below there is a representation of BPFdoor’s process:
Kevin Beaumont also managed to identify BPFdoor activity on networks belonging to organizations from different locations like the U.S., South Korea, Hong Kong, Turkey, India, Vietnam, and Myanmar, according to BleepingComputer. He found 11 Speedtest servers compromised by this malware.
BPFdoor and Its Anti-Evasion Techniques
According to the Sandfly Security’s report previously mentioned, here are the anti-evasion techniques BFPdoor uses:
- lives in the system memory and engages in anti-forensic actions (the process environment is wiped);
- through the loading of a Berkeley Packet Filter (BPF) sniffer it can see packets regardless of any locally running firewalls;
- performs changes on ‘iptables’ rules when a relevant packet is received. This way hacker’s communication by means of the local firewall is enabled;
- the binary name appears as a similar one to a Linux system daemon;
- it can rename and execute itself under /dev/shm/kdmtmpflush;
- eventually, before deleting the binary, it changes its date to October 30, 2008.
A reason why these anti-evasion techniques are employed could be that the threat actors intend to achieve binary protection if its deletion happens not to work, according to Craig Rowland.
The interesting part about this is the timestomp happens by the forked process before the main process tries to delete the binary. We assume this is a failsafe mechanism. If the implant should fail to load and not delete itself from /dev/shm/kdmtmpflush then the file left behind will have an innocuous looking time on it that masks when it was created. It would also make incident response harder if you are looking for recently created files (this one looks like it was created 14 years ago).
BPF’s Commands and Detection
Another analysis on this backdoor comes from Tristan Pourcelot, highlighting the hardcoded names the malware employs to match command strings inside relevant packets. These are:
- justtryit, justrobot, and justforfun for establishing a bind shell on ports 42391 via 42491 purposes;
- socket or sockettcp for the configuration of a reverse shell with an IP address from the packet.
Renaming the binary to appear as a normal Linux daemon using the options below is one of BPFdoor’s tactics for avoiding discovery:
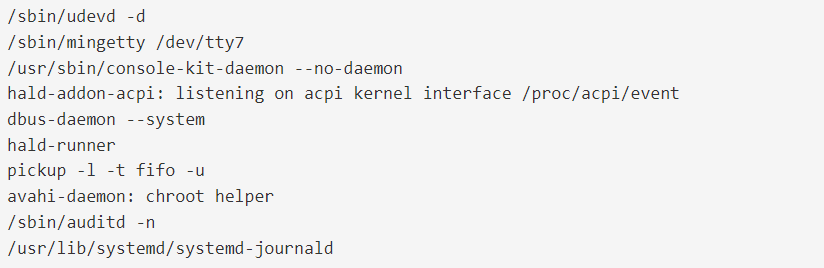
The BPFdoor is updated on a regular basis according to Pourcelot, and each release comes with distinct names for processes, files, and commands.
There were discovered at least 21 BFPdoor’s versions on VirusTotal. The backdoor managed to go undetected for a long time, the implant’s detection rate improving though after Beaumont, Rowland, and Pourcelot’s reports.
It Seems to Be Made in China
PwC researchers associated the BPFdoor with a China-based actor named Red Menshen (formerly Red Dev 18).
Red Menshen (formerly Red Dev 18) deployed its bespoke BPFDoor malware to multiple organisations in the Asia Pacific region, including telecommunication providers based in several countries. (…) We also identified that the threat actor sends commands to BPFDoor victims via Virtual Private Servers (VPSs) hosted at a well-known provider, and that these VPSs, in turn, are administered via compromised routers based in Taiwan, which the threat actor uses as VPN tunnels.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










