Contents:
Customers of Booking.com are being “caught off guard” by an email and WhatsApp phishing campaign. It demands credit card details to confirm a hotel reservation after booking. A targeted Booking.com customer has reported the incident to Heimdal® and shared images.
The scheme uses InfoStealing malware and social engineering to steal financial data from unsuspecting users. It seems threat actors are exploiting the lack of two-factor authentication from the vendor side.
We spoke with hotels that told us Booking.com admitted the existence of a breach when they contacted them. At the same time, they gave scant advice on security measures.
An individual targeted by the phishing campaign shared with us some WhatsApp messages he received from an “employee” of the hotel he booked on Booking.com.
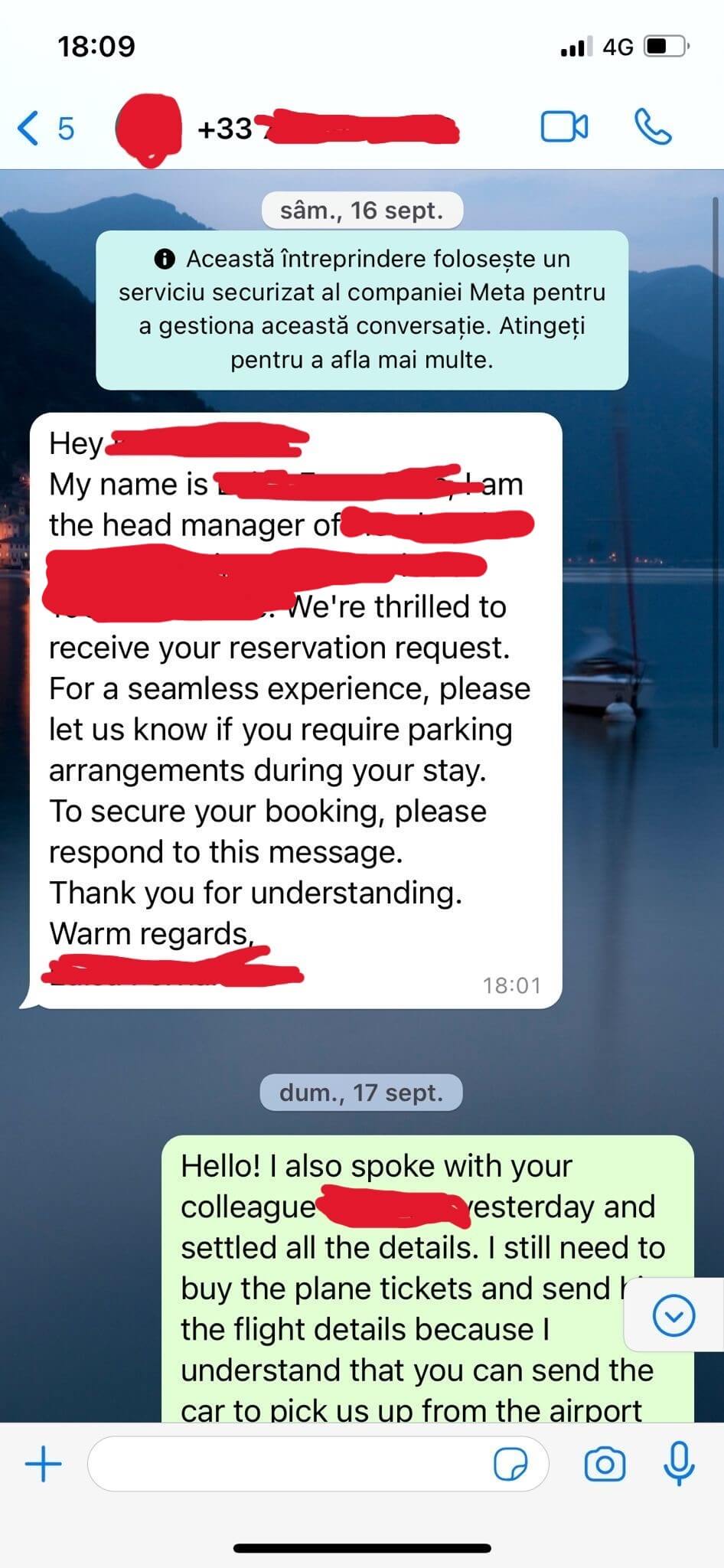
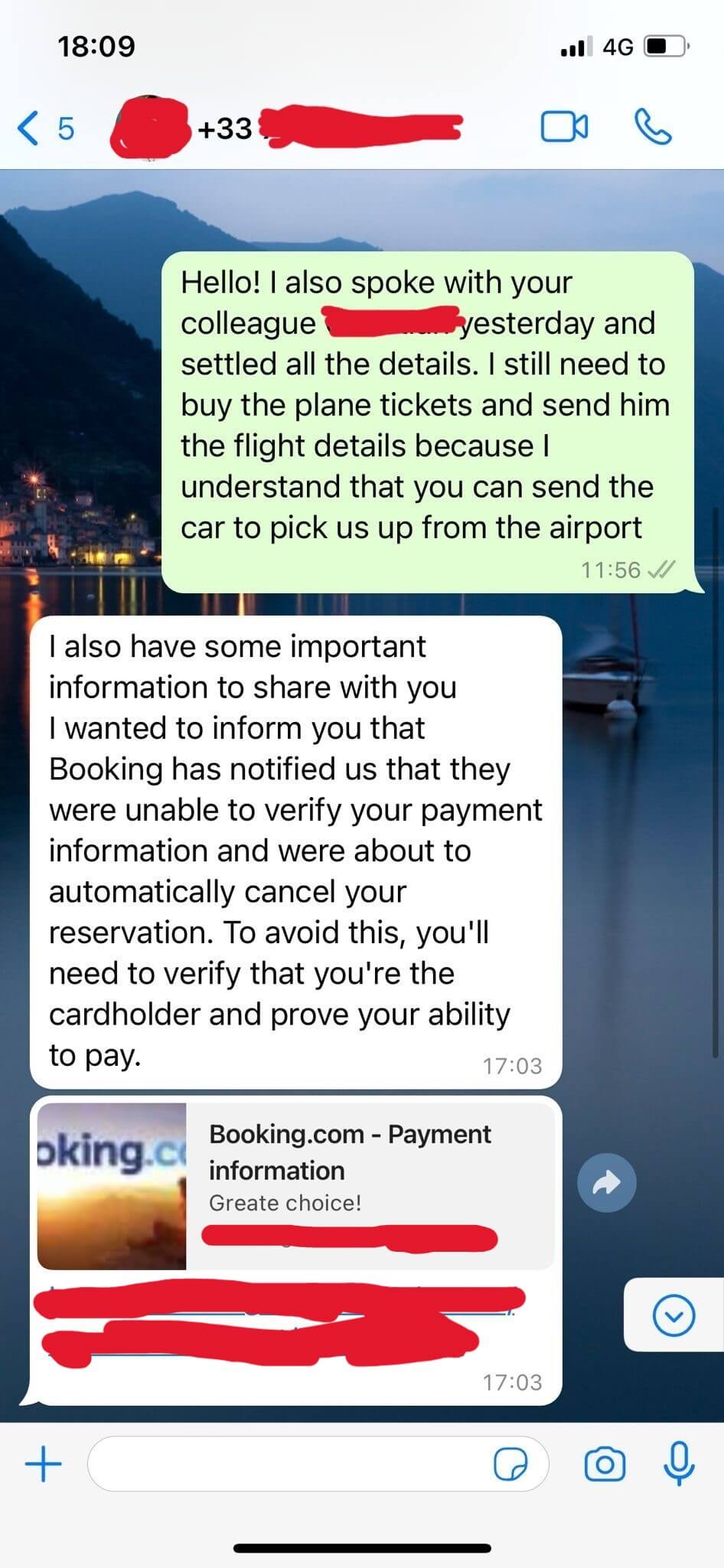
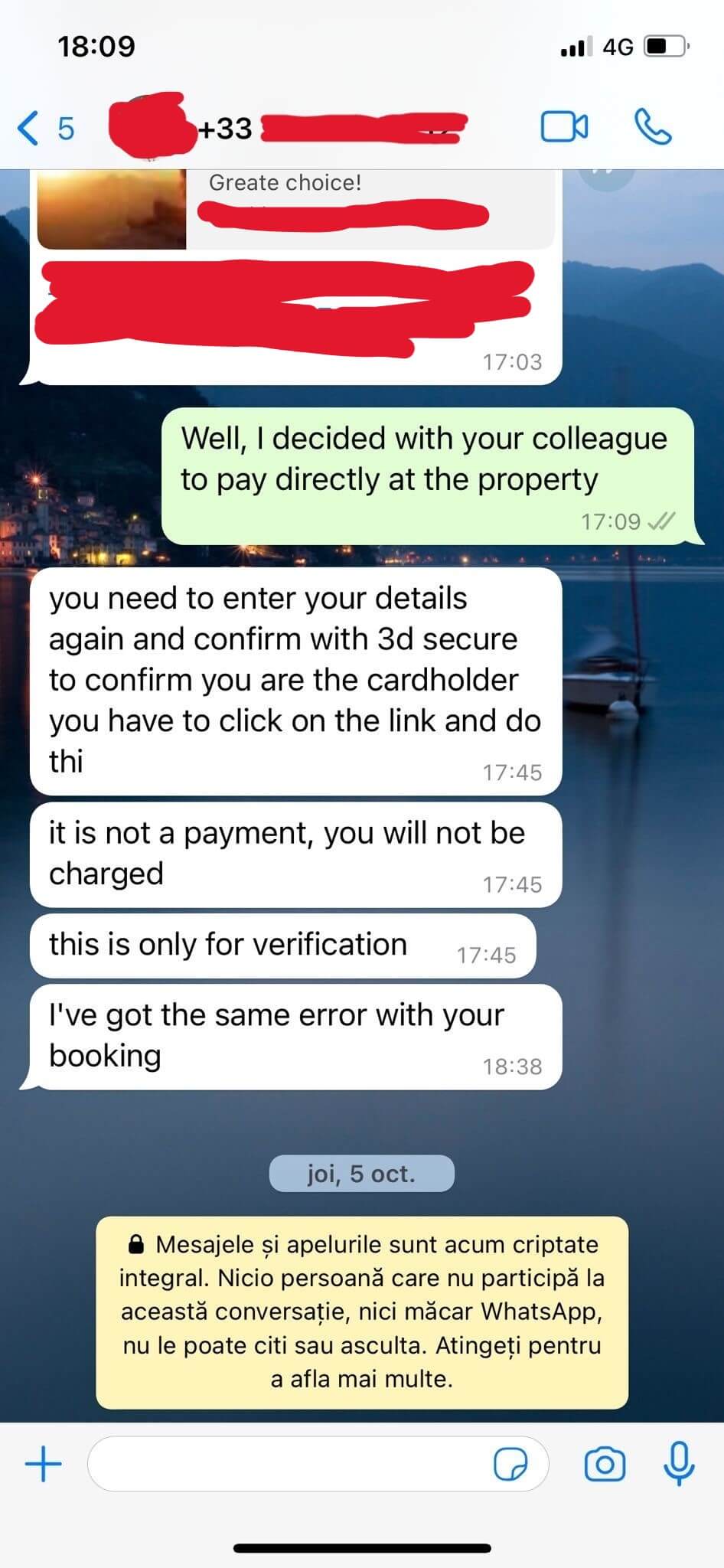
WhatsApp Conversation Between the Scammer and the Victim
More victims started voicing their concerns over on Social Media, tagging Booking.com’s official accounts, asking for help and clarifications.
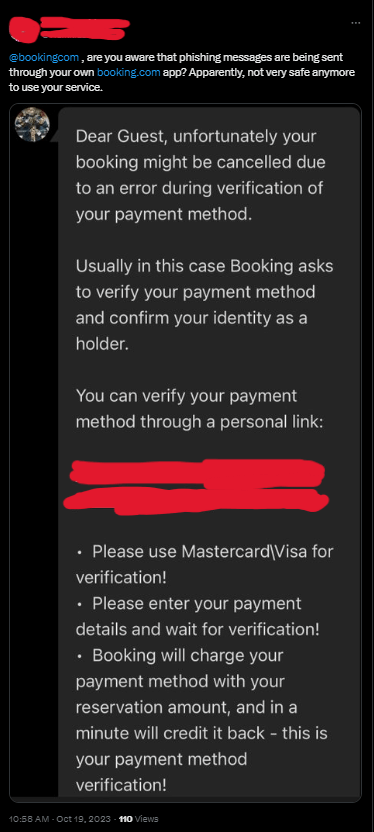
The Tweet of a Concerned Booking.com User
The admins of Booking.com’s social media accounts were seen replying to concerned users, giving their support, and offering them advice on how to spot phishing attempts.
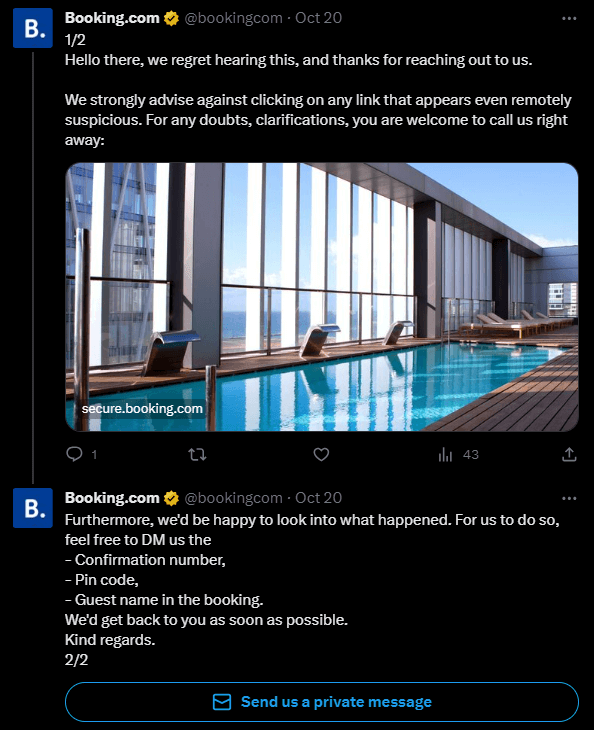
Booking.com’s Reply to a Concerned User
At the moment of writing this article, Booking.com has not addressed the situation in an official way, through a dedicated post or press release. Depending on its reach, the phishing campaign can cost Booking.com a lot of business, as customers have started to voice out their fear of using the app moving forward.
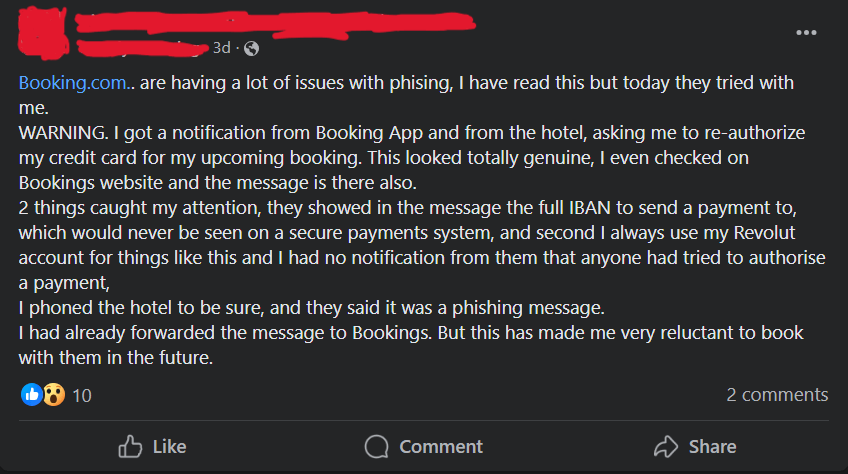
Concerned Victim on the Booking.com Phishing Attack
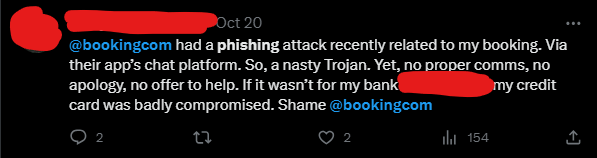
Tweet Addressed to Booking.com by a Victim of the Campaign
While waiting for a response from the company, users have started spreading the news in different travel communities around the Internet, to warn unwary travellers about the ongoing danger.
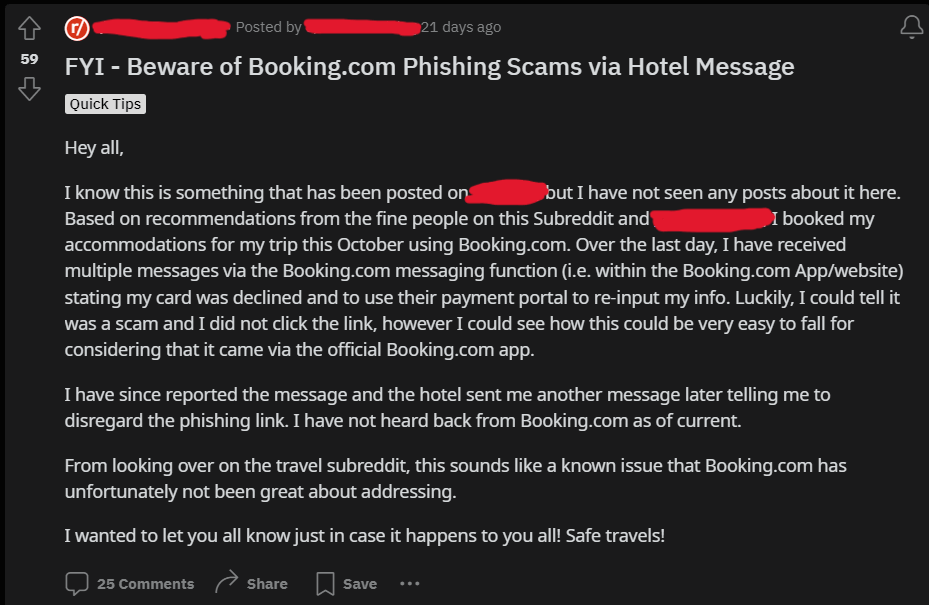
The Reddit Post of a Booking.com User
The Breakdown of the Booking.com Phishing Campaign: A Highly Sophisticated Operation
The First Step: Hostile Takeover
The scam unfolds through a calculated process initiated by cybercriminals gaining unauthorized access to various hotel systems linked to Booking.com. By hijacking these accounts, the attackers can extract sensitive guest information, including names, booking details, hotel specifics, and partial payment information. This data forms the foundation needed for the attack to be unleashed on unsuspected Booking.com users.
The Second Step: Dear Guest…
Using the data harvested from the compromised hotel systems, the attackers created customized messages to send to users. These messages are carefully created using social engineering techniques to create a sense of urgency for the user. Unsuspecting victims are instructed they must re-enter their payment details as a “verification test”, or their booking will be cancelled within 24 hours.
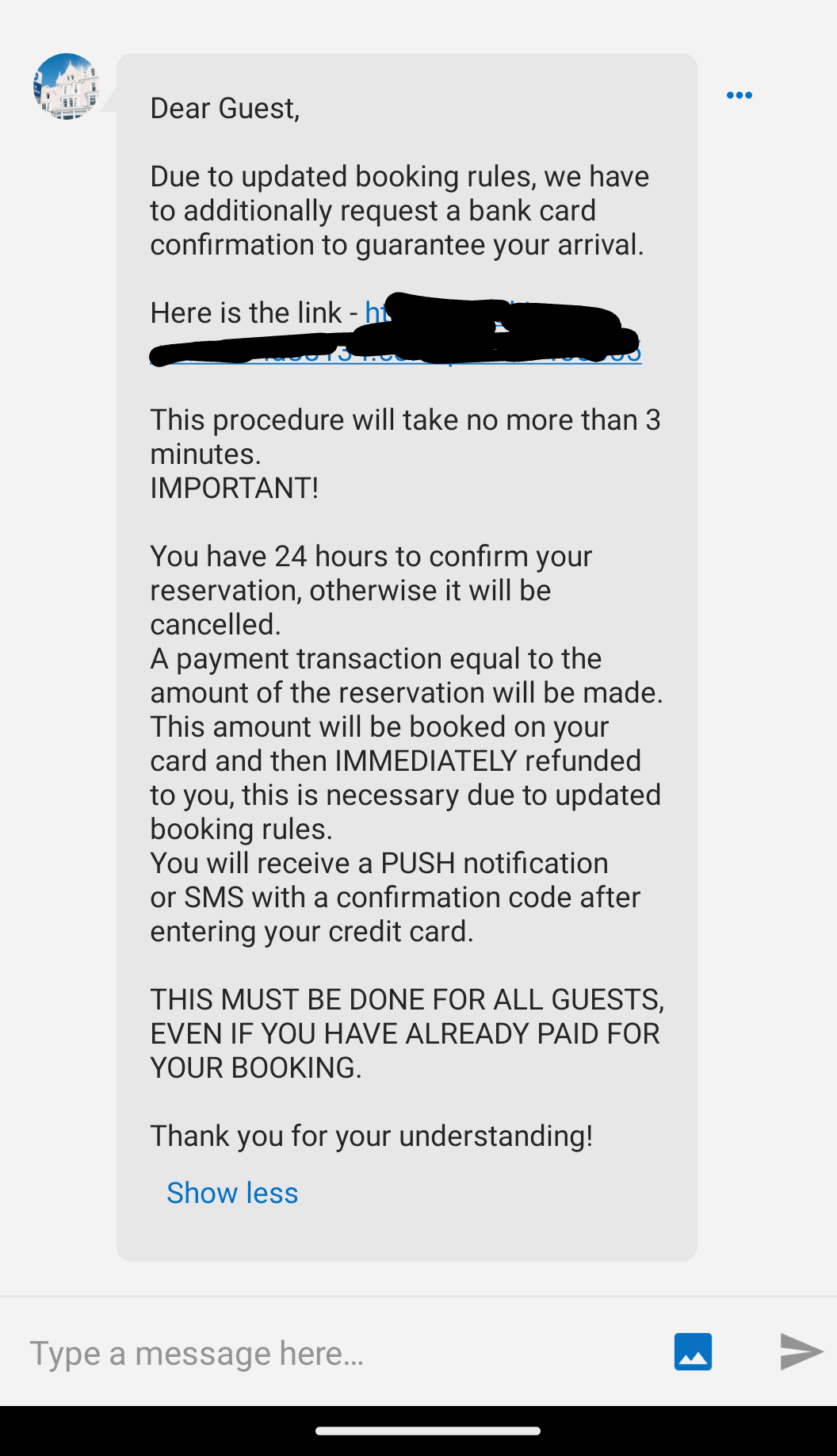
Phishing Message Received by a Victim via the Booking.com Platform
The Final Step: Luring and the Coup de Grâce
What’s next for the victims on their trip to financial theft? The attackers’ message contains a link that leads victims to a carefully crafted phishing page, that mimics the Booking.com payment portal identically.
The scam mail correctly displays all the booking and hotel details, it passes all checks and I’m 99% sure they are sent via Booking.com email servers. The only give-away is the URL, but it’s easy to miss it.
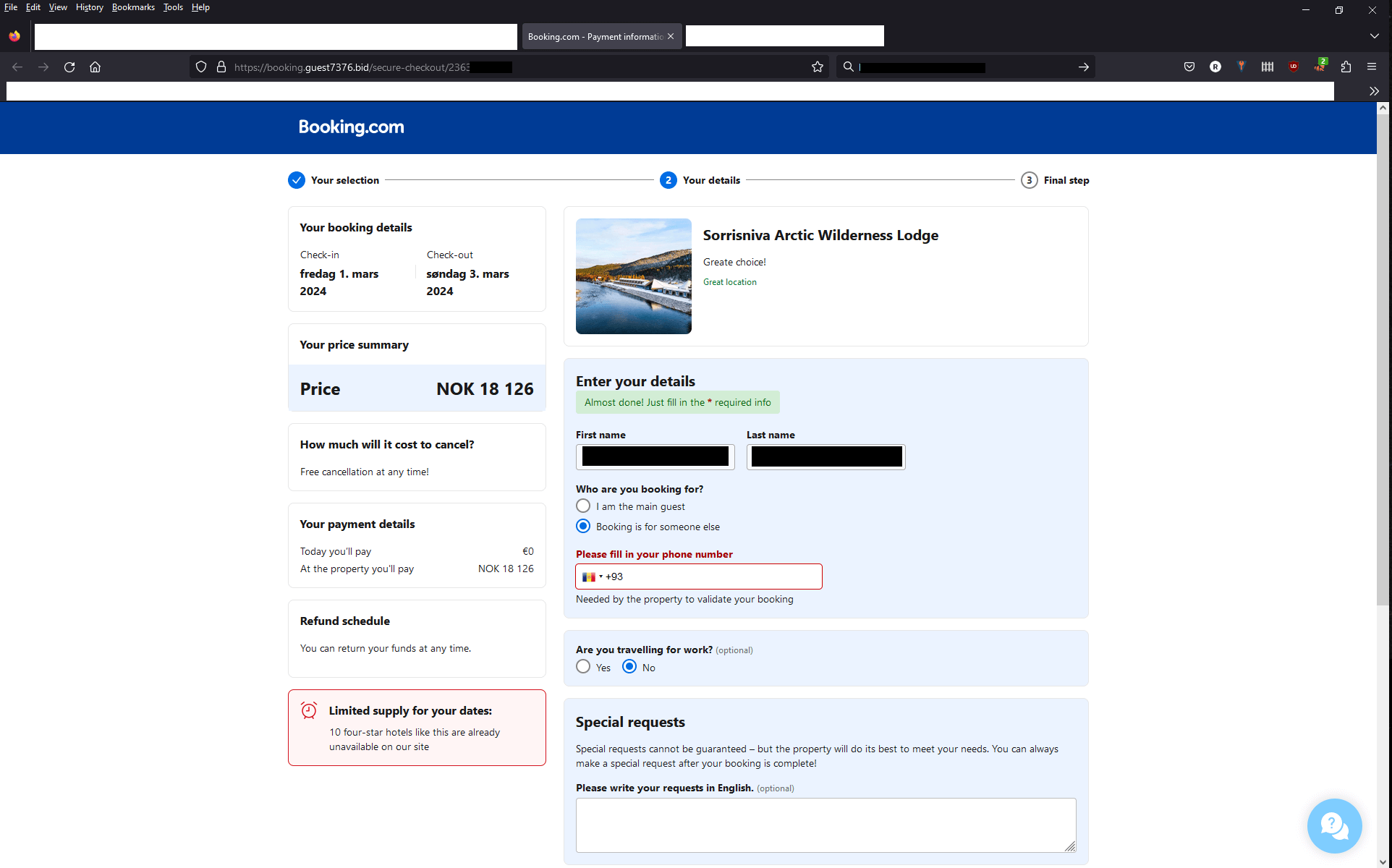
Fake Booking.com Interface Used by Threat Actors in Their Attacks
The page is already filled in with the personal information of the victims that attackers were able to harvest from the breached hotel systems, including their full name, hotel information, and stay duration. Even the URL of the page is designed to deceive victims, following the booking.guest or even booking-secure patterns.
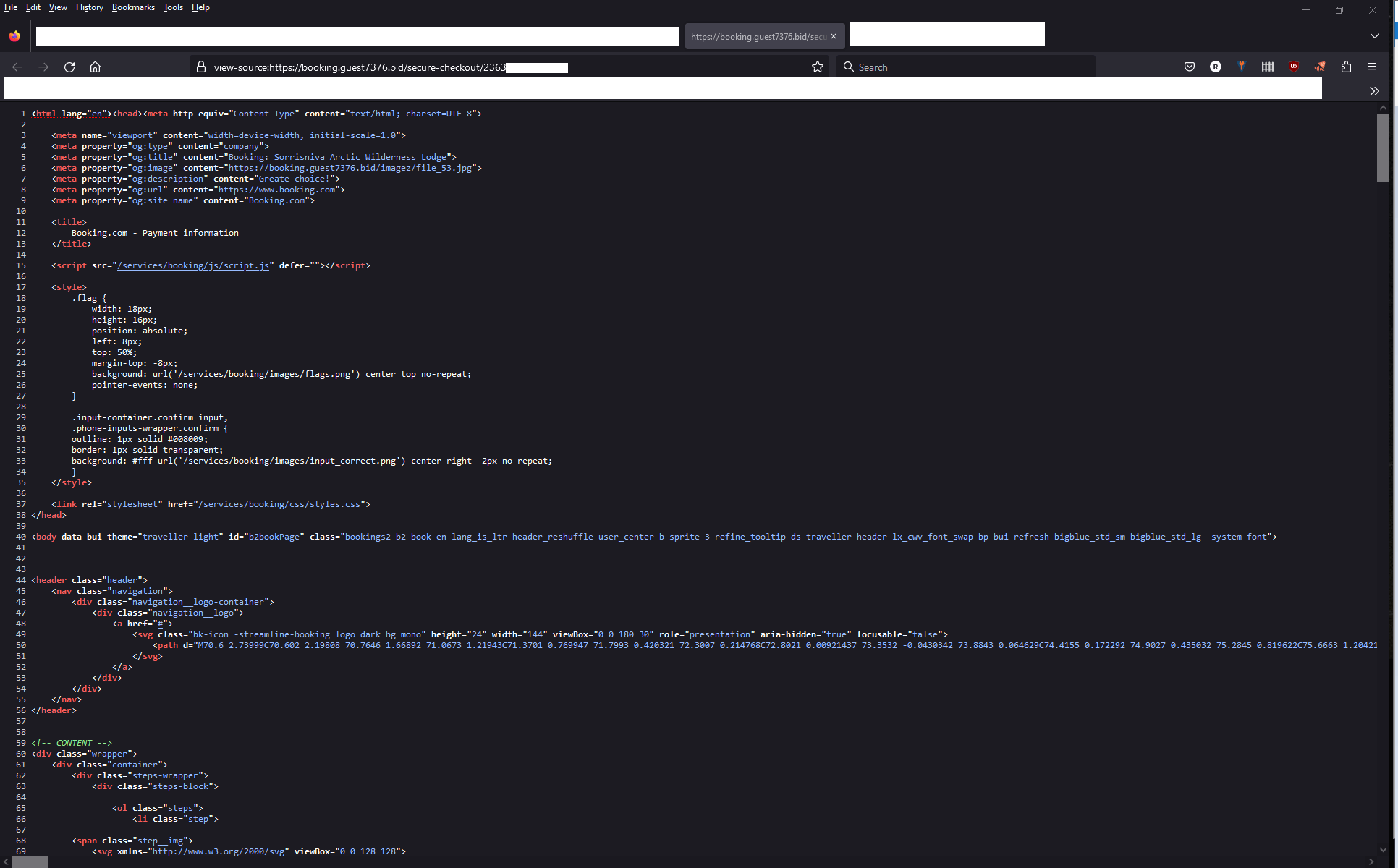
The Code Behind the Attackers Fake Booking.com Payment Portal
Here, the scam reaches its climax, as unsuspecting users re-enter their financial information, which go straight to the attackers.
Why Is This Phishing Campaign So Dangerous?
This phishing campaign is dangerous due to its method of delivery. The victims receive messages, emails, and links directly through Booking.com.
The campaign is deceptive, with a fake landing page that comes pre-loaded with the victims’ personal information. This includes the name, hotel, and trip duration. Of course, the victim assumes only Booking.com has this information.
And as a last push, this campaign manipulates the victims psychologically as well. The message puts the victims into a state of urgency, by threatening them to cancel their booking (which can actually be done since the threat actor has gained access to the hotel’s systems) unless they act as being told, leading the victims to add impulsively and provide their credit card information.
The Extent of the Campaign: How Large Is The Impact?
Taking into consideration the position Booking.com has in the hospitality industry, and its extended database, the reach of the campaign can be global, affecting thousands of people from all over the world.
For example, authorities in Singapore have already started investigating the incident. According to The Strait Times, a publication from Singapore, at least 30 people from the country have fallen victim to the hotel booking scam, with losses totaling around $41,000.
The victim realized they had been scammed only when they tried to contact Booking.com or the hotels regarding their reservations or discovered unauthorized transactions on their bank accounts or credit cards. Based on information from the investigation conducted by the police in Singapore, the campaign has been ongoing since at least September 2023.
The full impact of the phishing campaign is currently unknown. We are also unaware of Booking.com’s position or what measures they’re going to take as a result.
Based on the market position of Booking.com, the impact could rise to millions of dollars in potential losses. In the month of September 2023, Booking.com registered a number of 554.5 million visits, making it the most visited travel and tourism website in the world. The company also has established 198 offices in more than 70 countries worldwide. This extensive network allows them to serve a global audience and cater to travelers with diverse needs from various regions.
One thing is certain, this episode should determine Booking.com to take proactive measures in better protecting their users against such common threats for the industry they’re in. As our CEO, Morten Kjaersgaard says:
Given the continued exploitation of this bug, it’s evident that Booking.com does not have enough controls in place to ensure that the end consumers using their platform can interact safely with it, as those providing hospitality services are exposed to becoming part of a supply chain attack.
Morten Kjaersgaard, CEO of Heimdal®
Will the affected users be helped by the company? This is an ongoing investigation, so we’ll find out more details in the future, as more unfolds.
Staying Protected Against Phishing Attempts
The year 2023 has witnessed a troubling surge in phishing attacks, as highlighted by experts in the field, who reported staggering increases. Nowadays, it is mandatory for users to adopt proactive measures to be sure they are protecting their sensitive information. Here are some information on how to spot phishing attempts and remain safe online:
- Stay Informed: Keep abreast of the latest phishing tactics that cybercriminals are employing. Understanding the common signs of a phishing scam helps you avoid falling for one;
- Be Careful With Urgent Requests: You can see it extremely well in this campaign, threat actors create a false sense of urgency to lure victims into their traps and make them act without thinking through the situation. Take a moment to verify the legitimacy of the requests before acting;
- Contact Your Service Providers Directly: Contact the service provider directly using their official contact information, not the one supplied in any questionable emails or messages, if you get any;
- Double-Check URLs: Always check the URLs to be sure they correspond to the correct website. Search for minute spelling mistakes or unpronounceable domain extensions. On pages that don’t work properly or lead to broken pages, look for suspicious links;
- Look for Abnormalities: Do you see spelling errors in the subject of a mail, or in a message? Does the prefix of the phone number not match the one of your booked destination? These may be subtle, but clear signs that you’re heading towards a trap.
Also, it is important to note that the right cybersecurity solutions will keep your machine protected against such attempts. For example, Heimdal®’s award-winning DNS Security – Endpoint solution can prevent threats from reaching your machine by blocking traffic to and from any malicious C&C server.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








