Contents:
Key Takeaways:
- What is attack surface management?
- Why is attack surface management important?
- What are the best ASM vendors?
Over the last few years, attack surface management (ASM) has become an increasingly common category within cybersecurity.
The term describes a set of tools that help organizations to identify their IT assets and the vulnerabilities associated with them, so they can reduce their overall cyber risk profile.
Despite being a comparatively new term, there are now several different tools on the market that specialize in attack surface reduction.
But finding the right one for your organization can be easier said than done.
So, which are the best tools on the market? How do they help keep your attack surface secure? And how do you choose the right option for you?
Here’s everything you need to know.
What is Attack Surface Management?
Attack surface management tools have become increasingly widespread in the last few years. This effect has been particularly clear since the pandemic and the subsequent widespread adoption of remote working.
While the term might be new, the technology it describes generally has a longer heritage.
To oversimplify, you can consider ASM to be a bundle of cybersecurity tools that were traditionally split between different products, including:
- Asset discovery: Detecting known, unknown, or forgotten assets, including servers, endpoints, domains, IP addresses, cloud services, and more.
- Vulnerability scanning: Identifying unpatched vulnerabilities at the software and operating system level, across the IT environment.
- Risk prioritization: Quantifying the relative risk of different vulnerabilities and providing contextual insights from the wider cybersecurity community. This helps you to decide which vulnerabilities to prioritize for patching.
- Attack surface mapping: Visualizing the entire scope of digital assets in an IT environment. This often takes the form of a graphical or map-based view, which demonstrates the relationships between different assets.
- Compliance reporting: Like the vast majority of cybersecurity tools, ASM products also generate automated reports to demonstrate security compliance. Many tools enable you to customize these reports to your own requirements, but there is significant variation in how effective and flexible these tools are between different vendors.
So why do we need a new category?
In the last few years, ASM tools have quickly gained popularity due to the explosion of cloud-based software and subscriptions over the last decade.
Now, large organizations have a vast range of entry points across applications, websites, networks, devices, and cloud infrastructure.
Each of these channels creates a new attack vector for hackers to exploit. This causes the attack surface to continuously and exponentially expand as new services and tools are added.
ASM tools therefore focus specifically on user accounts and vulnerabilities across the whole range of networks and cloud-based systems that an IT organization may rely on.
The goal is to help IT teams visualize and protect all the internet-exposed assets that can be used to target them.
It’s also helpful to note that there are two slightly different types of products we discuss in this piece: Attack surface management (ASM) and external attack surface management (EASM). In practice, they are very similar, but EASM products generally focus on a more limited set of external-facing assets.
Top 10 Attack Surface Management Platforms: Pros, Cons, and Reviews
1. Heimdal
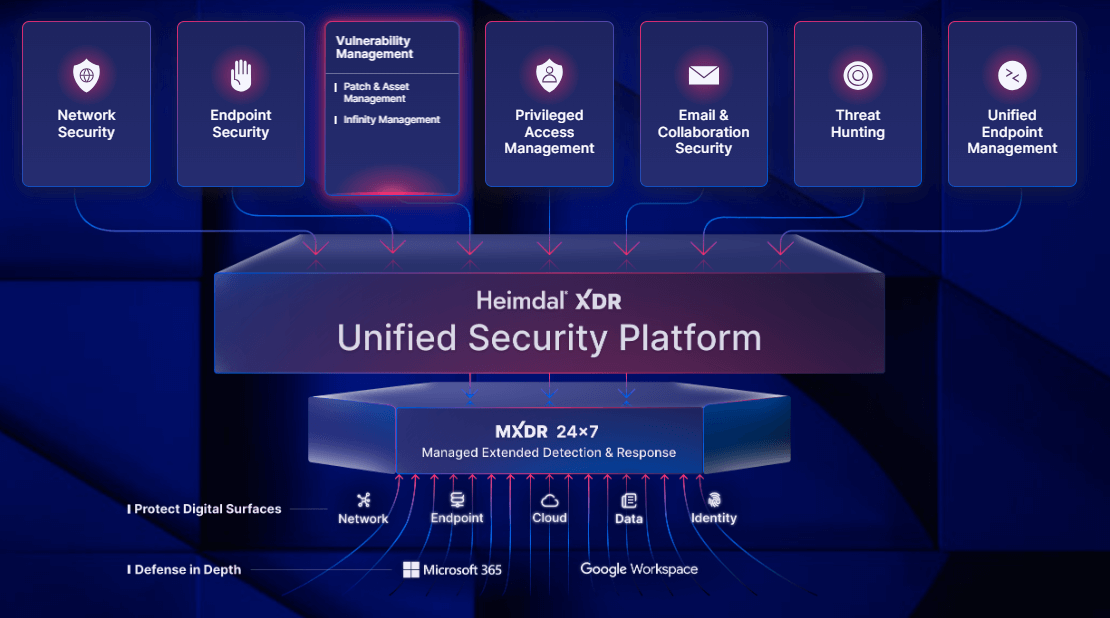
Unlike many products on this list, Heimdal isn’t just an ASM or EASM. It’s all this and much more.
Most ASM/EASM tools are point solutions, which means they’re designed for a single specialized use case. But when it comes to attack surface management, there’s a real limit to how effective this can be.
By definition, your attack surface can’t just be a collection of external-facing assets and unpatched vulnerabilities.
If the term has any meaning whatsoever, it has to include every possible vector that an attacker can use to target you.
The products on this list offer a range of effective tools, largely in the categories of vulnerability management and asset discovery.
Many also offer effective automations, risk-based prioritization, and more. But Heimdal is the only vendor that can possibly claim to defend against the full range of attack vectors that a hacker may use.
That’s because Heimdal offers the widest set of cybersecurity tools under one license of any cybersecurity vendor.
Here’s what that includes:
- Network security: Protect against network-based threats like man-in-the-middle, DNS spoofing, and more, with some of the market’s most advanced DNS filtering tools.
- Endpoint security: Prevent a whole range of endpoint-level threats, including ransomware, malware, data leaks, and unpatched vulnerabilities. Heimdal lets you automatically detect issues and remediate with a one-click response.
- Vulnerability management: Easily eliminate vulnerabilities at the network, software, and operating system levels. With customizable automations, you can decide what gets patched and when, without having to manually install updates.
- Privileged access management: Implement least privilege with dynamic tools to grant and revoke user rights on a case-by-case basis. This reduces your attack surface for user accounts to an absolute minimum.
- Email and collaboration security: Heimdal offers complete email security and fraud prevention. As well as traditional phishing prevention, it also includes AI-powered anomaly analysis that can identify and prevent unknown threats like malware, spam, and malicious URLs.
- Threat hunting: Implement a genuinely proactive approach to threat hunting. Heimdal includes integrated threat intelligence to give you the real context into emerging threats, helping you to quickly identify and resolve the most critical issues.
- Unified endpoint management: Get a single dashboard to manage desktops, mobile devices, and tablets. This integrates with our privileged access management solution to dynamically control admin access at the endpoint level.
- Managed services: All our security products come with an optional additional managed extended detection and response (MXDR) module. This means you’ll have an incident response team on hand to detect and prevent threats as they happen.
Pros:
It’s a fantastic tool. I recently moved 2,000 endpoints from SentinelOne Complete to Heimdal and couldn’t be happier. The Heimdal SOC is highly communicative and extremely helpful, which was not my experience at all with Vigilance and SentinelOne. Having all of the other Heimdal features is also a huge bonus. Their third-party patching module is the best I’ve seen so far.
– Heimdal user review, via Reddit
- A complete platform: Heimdal offers the complete ASM feature set and several other key security protections. This includes asset and vulnerability scanning, customizations, reporting, and more.
- Manage access and accounts: Most ASM/EASM products feature tools to detect assets, but not to manage access to them. Instead, Heimdal’s privileged access management functionality enables you to dynamically control access to sensitive information, data, accounts, and assets.
- Rich contextual insights: Heimdal has access to a vast amount of information about realtime and emerging cyber threats right around the world. This enables us to provide our customers with detailed context into software vulnerabilities and realtime attacks, making it much easier to understand the real risk of a threat and prioritize your response.
Cons:
First-time setup can be a little challenging. Patch management group policies took a little bit of getting used to – but once you crack it, it just ticks along.
– Heimdal user review, via G2
Reviews:
Get a complete cybersecurity platform under one license and dashboard. Save costs, reduce licenses, and improve cybersecurity with Heimdal.
2. Microsoft Defender EASM
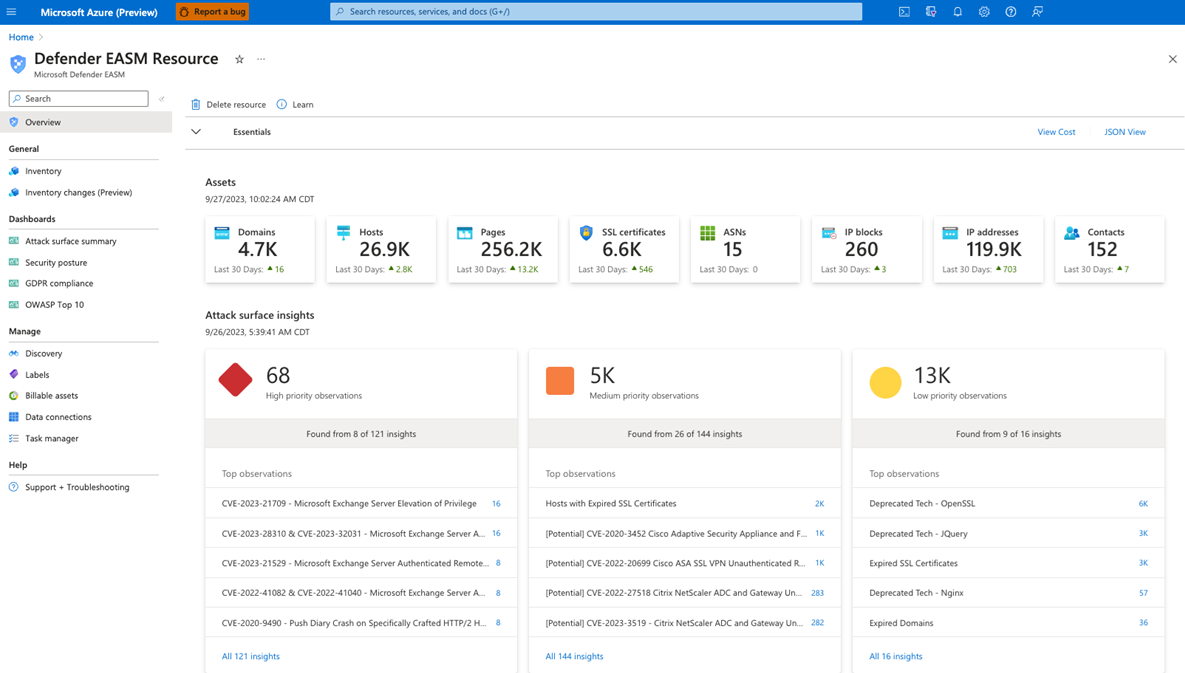
As the name would suggest, Microsoft’s EASM platform comes as part of the wider Defender security suite.
It offers several integrated features, including asset discovery, integrated threat intelligence feeds, and automated remediation.
As a Microsoft product, the platform is particularly well-suited to Windows and Azure environments – as well as anybody already using other Defender products.
Pros:
Microsoft Defender for EASM stands out because it safeguards organizations from a wide spectrum of external threats.
– Microsoft Defender EASM user review, via G2
- Effective detection: Microsoft EASM is generally praised for its ability to effectively detect both assets and vulnerabilities. In particular, the auto-discovery feature can run continuous scans without manual oversight.
- Microsoft-native: The product is a good choice for teams already bought into the Microsoft ecosystem. Nonetheless, organizations looking to avoid vendor lock-in may not consider this a benefit.
- Centralized dashboard: Microsoft offers alerts through a single dashboard, making it easy for IT teams to easily see the most recent alerts at a glance.
Cons:
It generates a lot of false positives, so you might need to have at least one person looking at those. It can require more processing power and storage, and it can for sure increase the cost. It’s part of Microsoft Defender, so you will need an existing license to have the External Attack Surface Management.
– Microsoft Defender EASM user review, via Gartner
- Complex: Like most Microsoft products, Defender EASM is complex and can be difficult to configure. Generally, it’s better suited to expert teams.
- False positives: Many users mention that Microsoft Defender creates a high number of false positives, which can lead to alert fatigue.
- Limited customization: Customizing bespoke reports and scans is more difficult in Microsoft Defender than in other products. It also lacks granular customization options, meaning even experienced users struggle to customize it exactly as they need.
Reviews:
- Gartner: 4.3/5 stars (84 reviews total)
- G2: 4.3/5 stars (16 reviews total)
3. CrowdStrike Falcon Exposure Management
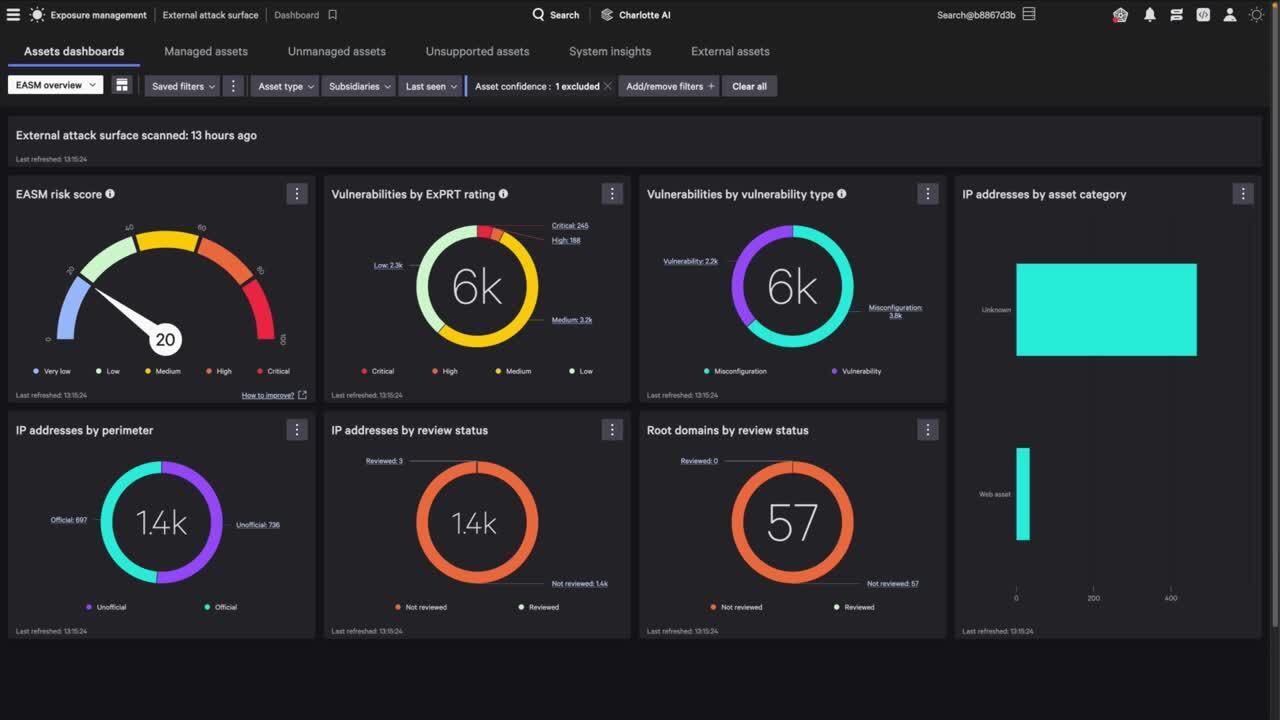
CrowdStrike is one of the cybersecurity industry’s biggest names, and its EASM product comes as part of the wider Falcon line of security products. These are all enterprise-focused solutions that generally have a wide range of functionality, but a high price point to match.
Here, the EASM product is no exception. Nonetheless, loyal customers suggest that the rich threat intelligence, effective monitoring tools, and wide customizations mean it’s well worth the cost.
Pros:
“CrowdStrike delivers the biggest bang for its buck and is customizable to the exact tools needed.”
– Falcon Exposure Management user review, via Gartner
- Rapid discovery: Many reviewers have praised the product for its ability to quickly detect internet-facing assets.
- Wide customizations: Falcon Exposure Management offers a flexible range of customizations, enabling IT teams to configure bespoke and granular scans and automations.
- User-friendly: The product is often praised for its straightforward user interface, which makes it easy to get started and find vulnerabilities.
Cons:
The product can be very expensive for small and medium businesses. The pricing model is not flexible or scalable enough.
– Falcon Exposure Management user review, via Gartner
- High cost: Like all CrowdStrike products, Falcon Exposure Management is an expensive product. Users also note that the pricing model is particularly rigid and difficult to scale.
- Integration and support: Some users note that the product lacks important integrations, and that support for legacy and minor operating systems is limited.
- Overlapping licenses: Though an effective EASM platform, this is only one of many separate CrowdStrike products. To get full coverage, customers will have to link together multiple subscriptions, which can be confusing and expensive.
Reviews:
- Gartner: 4.5/5 stars (43 reviews total)
4. CyCognito: EASM
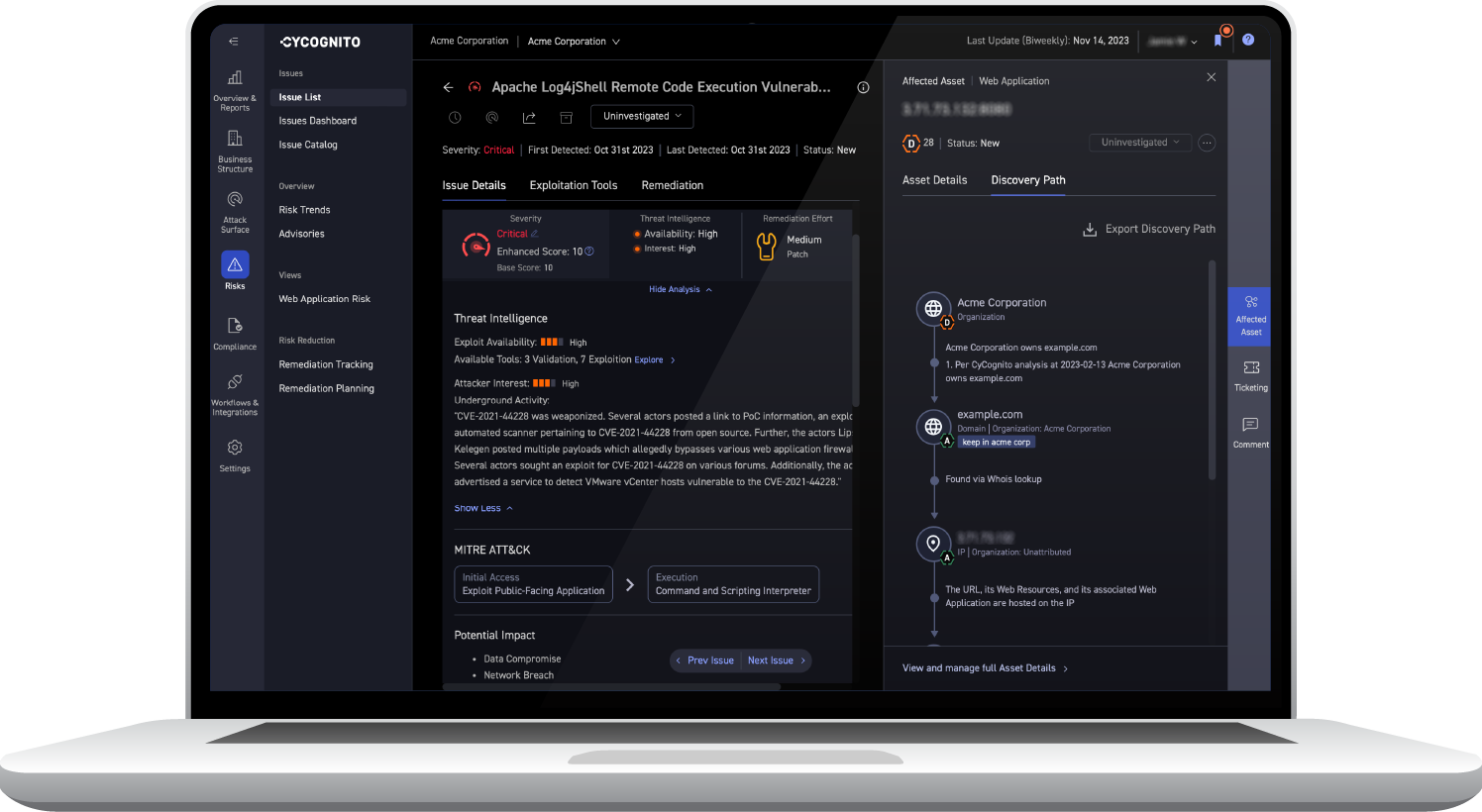
CyCognito is a more niche cybersecurity vendor that specializes in attack surface management across several products. The suite contains a wide set of functionality to manage cloud security, application security, and vulnerability management.
This more specialist approach comes with pros and cons. Users appreciate the depth of asset scanning and monitoring functionality – but the product may be more difficult to integrate into a wider security suite.
Pros:
Risk scoring and vulnerability detection features are very useful for prioritizing high-risk assets, which include misconfigurations and unpatched software versions.
– CyCognito user review, via Gartner
- Asset scanning: The product is particularly praised for its comprehensive asset discovery features. It works autonomously to detect known and unknown assets without significant input from the IT team.
- Ease of use: CyCognito also offers a straightforward user experience and a smooth learning curve.
- Continuous monitoring: Reviewers particularly appreciate how CyCognito constantly monitors threats, making it comparatively quick and easy to discover new and unknown assets.
Cons:
False positives. We get a bunch of issues that are not really issues – once that happens, there isn’t anybody to talk to. The account manager sends you to create a support ticket and from them, you don’t get a response for a very long while, if any.
– CyCognito user review, via G2
- False positives: Many reviewers mention frustrations with the high level of false positives and the alerts, which can be distracting and difficult to manage.
- Scanning limitations: CyCognito imposes limits on the number of times a customer can re-scan a particular asset – known as ‘revalidation’. This arbitrary restriction makes it difficult to scan all assets when you need to.
- Integrations: The product also features relatively few third-party integrations, when compared with larger competitors.
Reviews:
- Gartner: 4.7/5 stars (38 reviews total)
- G2: 4.3/5 stars (5 reviews total)
5. Palo Alto: Cortex Xpanse
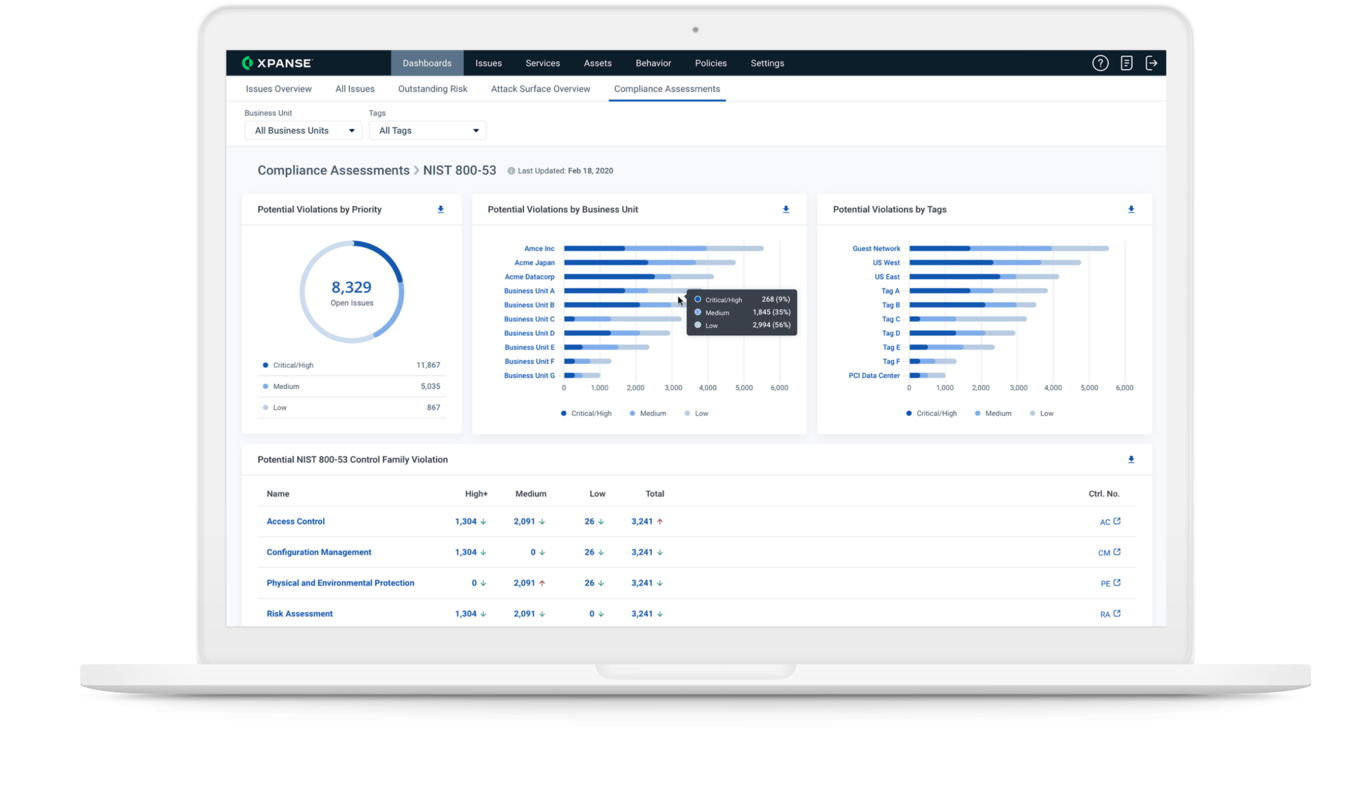
Palo Alto’s Cortex platform is a wide-ranging set of security tools and features, generally aimed at enterprise customers. The Cortex Xpanse module specializes in attack surface management, offering comprehensive asset visibility, detection, and analysis.
Cybersecurity tools by Palo Alto are generally designed to work together.
If you’ve already bought into the wider Cortex platform, Xpanse could well be the tool for you. If not, you may prefer to explore more flexible alternatives.
Pros:
Scanning the web for accessible assets, this tool provides detailed reports. It allows users to delve into vulnerabilities, offering insights on severity and exploitation likelihood.
– Cortex Xpanse user review, via Gartner
- Comprehensive visibility: Cortex Xpanse offers wide visibility over vulnerabilities, assets, and accounts. Reviewers note that it is effective in detecting unknown risks and blind spots.
- Effective prioritization: The prioritization tools are also effective, offering insights into severity, exploitation likelihood, and more.
- Rich context: Palo Alto’s vast global footprint gives the company access to detailed threat intelligence integration. This means the Cortex Xpanse product offers rich context and background into the threat landscape, helping users to understand their full risk profile.
Cons:
The cost is significant compared to other similar products in the market.
– Cortex Xpanse user review, via Gartner
- Integrations: Cortex Xpanse is primarily designed to work within the wider Palo Alto ecosystem, but integrations with third-party vendors are less extensive.
- Cost: Like all Palo Alto products, Cortex Xpanse is aimed squarely at the enterprise market, meaning it comes with a high price tag.
- Resource-intensive: Reviewers also mention that the product has particularly high CPU requirements.
Reviews:
- Gartner: 4.4/5 stars (28 reviews total)
6. Intruder: EASM
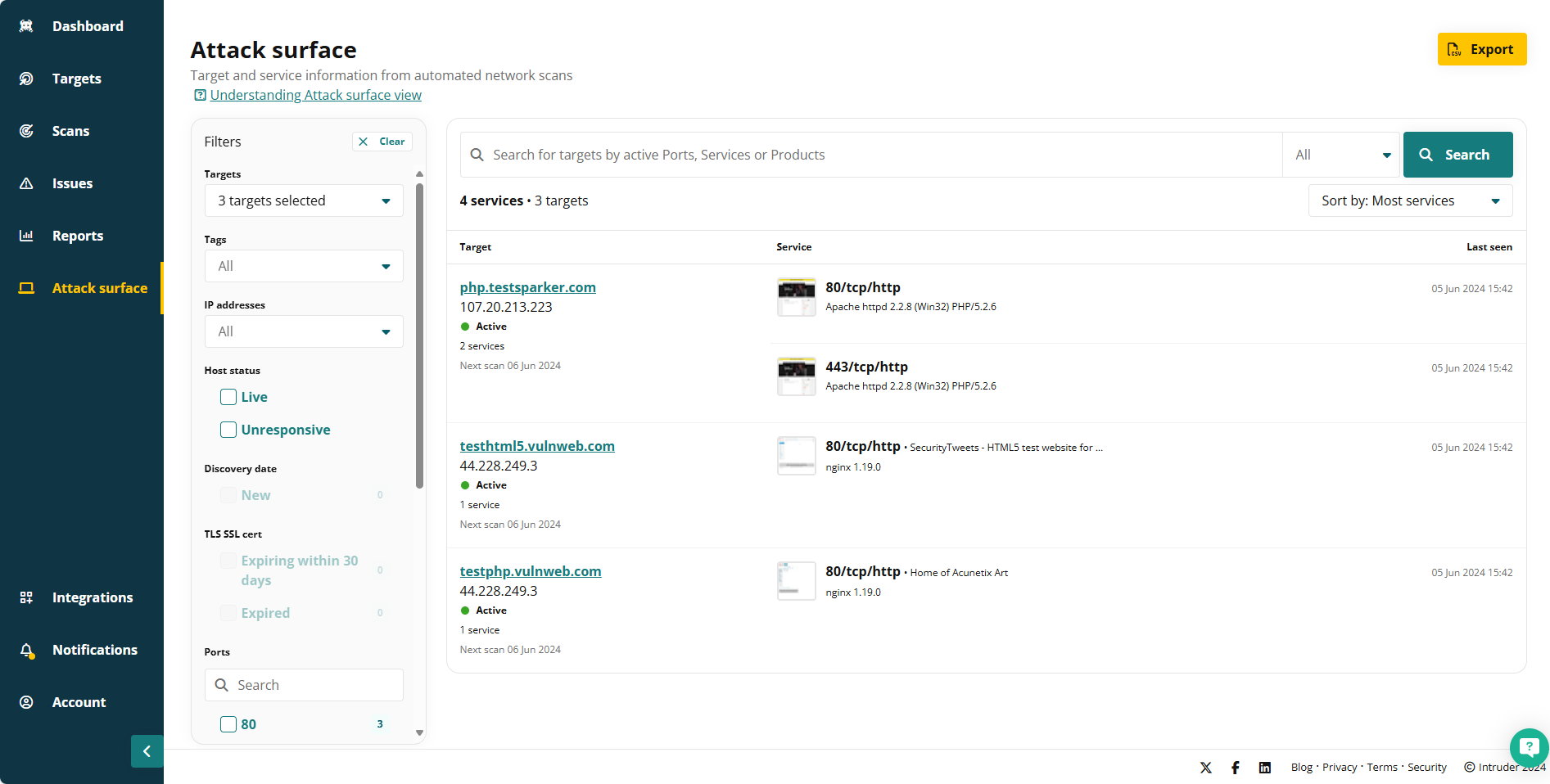
Intruder EASM is a specialist surface management solution that’s well-suited to mid-market businesses. It provides an effective set of tools to discover external-facing assets, alongside several integrations with major cloud vendors.
Pros:
It uses a set-and-forget approach, it’s easy to configure and it quickly gets out of your way once configured.
– Intruder EASM user review, via Gartner
- Ease of use: Intruder’s EASM product is easy to set up and deploy, with an intuitive interface that lets customers quickly get up and running with the product.
- Clear reports: The reports are detailed and straightforward. This makes it easy for IT teams to manage the attack surface without excessive admin.
- Strong support: Many reviewers have also praised the platform for its effective, fast, and knowledgeable support team.
Cons:
The only issue we have experienced is the way the licensing works. Once a target is set and it consumes a license, we have to wait 30 days to move the license to a new target, if there’s a change in infrastructure.
– Intruder EASM user review, via Gartner
- License restrictions: Intruder EASM has a 30-day lock-in period after licenses are assigned, making it difficult for users to reassign spare licenses. This is a very commonly cited issue.
- Configuration issues: Several users have noted important feature gaps and configuration issues. This includes a complicated API authentication process, as well as limitations around multi-factor authentication.
- Costs: The platform has higher costs than some competitors, and can also be difficult to scale.
Reviews:
- Gartner: 4.7/5 stars (14 reviews total)
- G2: 4.8/5 stars (183 reviews total)
7. Detectify
Detectify is another niche ASM vendor. The product benefits from a wide range of detailed security research from a community of ethical hackers, providing effective insights and context into various threat alerts.
The product features continuous monitoring, actionable remediation tips, integrations, and a range of tools to customize bespoke scans and reports.
Pros:
What most stood out to me was how easy it was to generate rich, insightful reports, even with no prior knowledge of how the tool worked. I was able to build reports in minutes that I had expected to take hours.
– Detectify user review, via G2
- Strong automations: The platform is widely praised for its wide and customizable automations. Users generally find it easy to build custom scans and reports.
- Effective discovery: Detectify effectively discovers unknown accounts and vulnerabilities, enabling users to map the entire attack surface, with limited false positives.
- Reporting: Users note how easy it is to create rich, detailed, and customized reports from the Detectify platform.
Cons:
There is a lack of clarity regarding the outcomes of spidering. While Detectify’s spidering capabilities are beneficial, the absence of comprehensive details about the crawling process makes it difficult to verify whether all components of an application have been thoroughly assessed.
– Detectify user review, via G2
- Expensive: Many users have noted the high costs of the platform, as well as the confusing pricing structure.
- Complex setup: The product can often seem overwhelming, particularly to new and non-technical users. Compared with other products on this list, Detectify is better suited to technical teams.
- Limited transparency: Some reviewers have noted that it’s difficult to verify exactly what has been scanned. This means IT teams can struggle to guarantee that all areas of an app or system have been covered.
Reviews:
- G2: 4.5/5 stars (51 reviews)
8. Rapid7
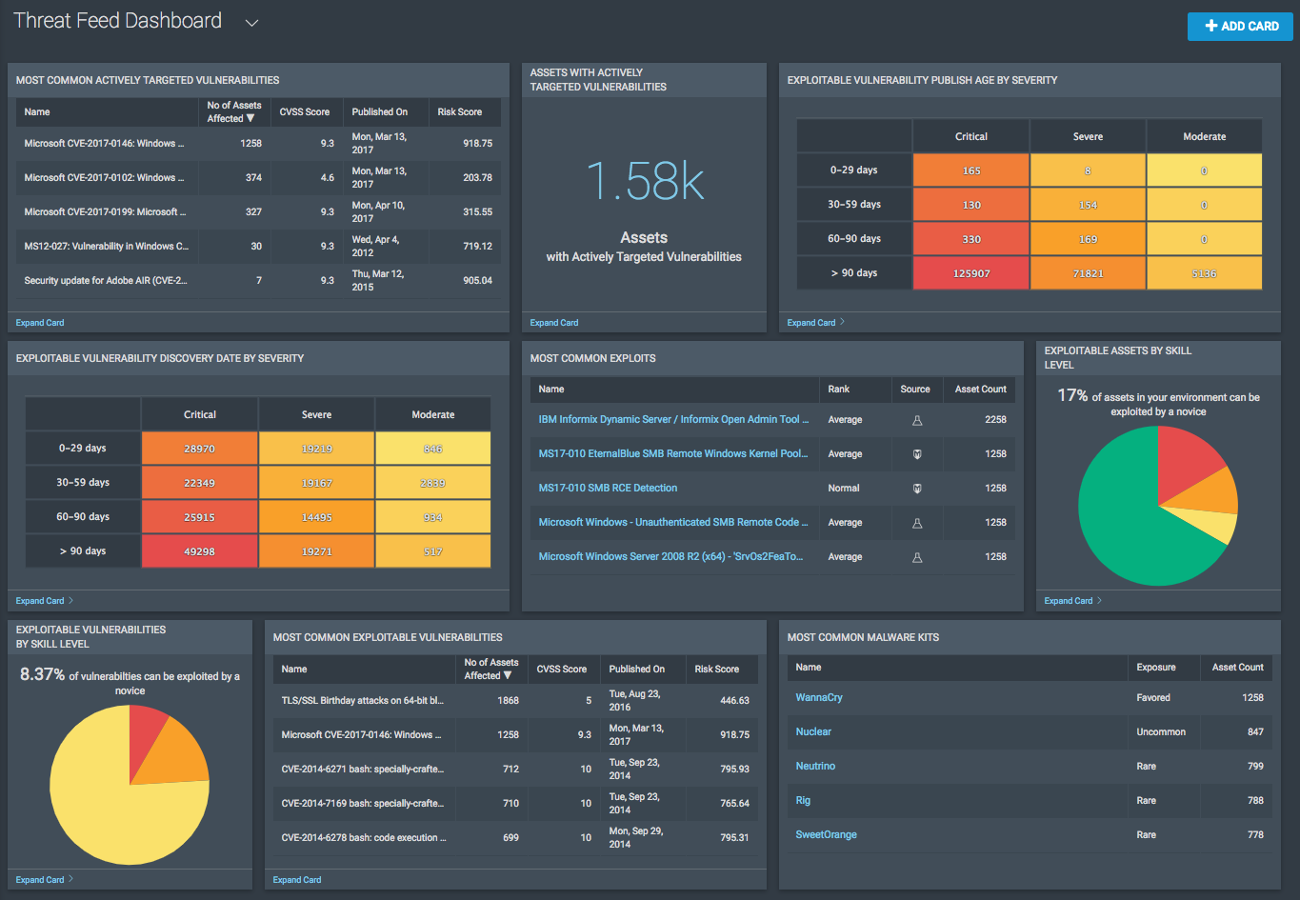
Rapid7 is an enterprise-focused attack surface management vendor.
The product offers a range of standard ASM features, including vulnerability management and assessment, risk scoring, automated asset discovery, and external threat intelligence.
It’s particularly appreciated for its lightweight and user-friendly approach, which is less common in enterprise-focused solutions.
Pros:
Their tools provide in-depth visibility into our network, vulnerabilities, and threats, allowing us to proactively manage our security posture. The user-friendly interface and robust reporting capabilities make it easy to prioritize and address security issues efficiently.
– Rapid7 user review, via G2
- Strong UX: The product is regularly praised for its effective user interface, which makes it easy for non-IT experts to keep track of risks and threats.
- Actionable reporting: Reviewers also mention the effective reporting and remediation tools, saying they’re detailed and straightforward.
- Good threat visibility: Rapid7 provides an effective set of tools to detect, manage, and prioritize the most critical risks. This makes it easy for users to get visibility over their assets and vulnerabilities.
Cons:
It lacks some no-brainer automation options. Also, I’ve been using the platform for more than a year and I think I raise more than three support tickets each month due to technical issues. Almost all the time I hear back ‘we have never seen this behaviour with our tool before’ from Rapid7 support, which gets very frustrating as a customer.
– Rapid7 user review, via G2
- Limited automations: The product has limited options to build custom reporting and scanning automations, particularly when compared with other competitors.
- Expensive: The pricing can also be relatively high, particularly for Rapid7’s more SMB-focused customer base.
- Technical issues: An unusually high number of reviewers have noted technical issues with the product, particularly around scanning. Many have also noted that the support team could have been more helpful in resolving these issues.
Reviews:
- G2: 3.8/5 stars (11 reviews total)
9. Tenable: ASM
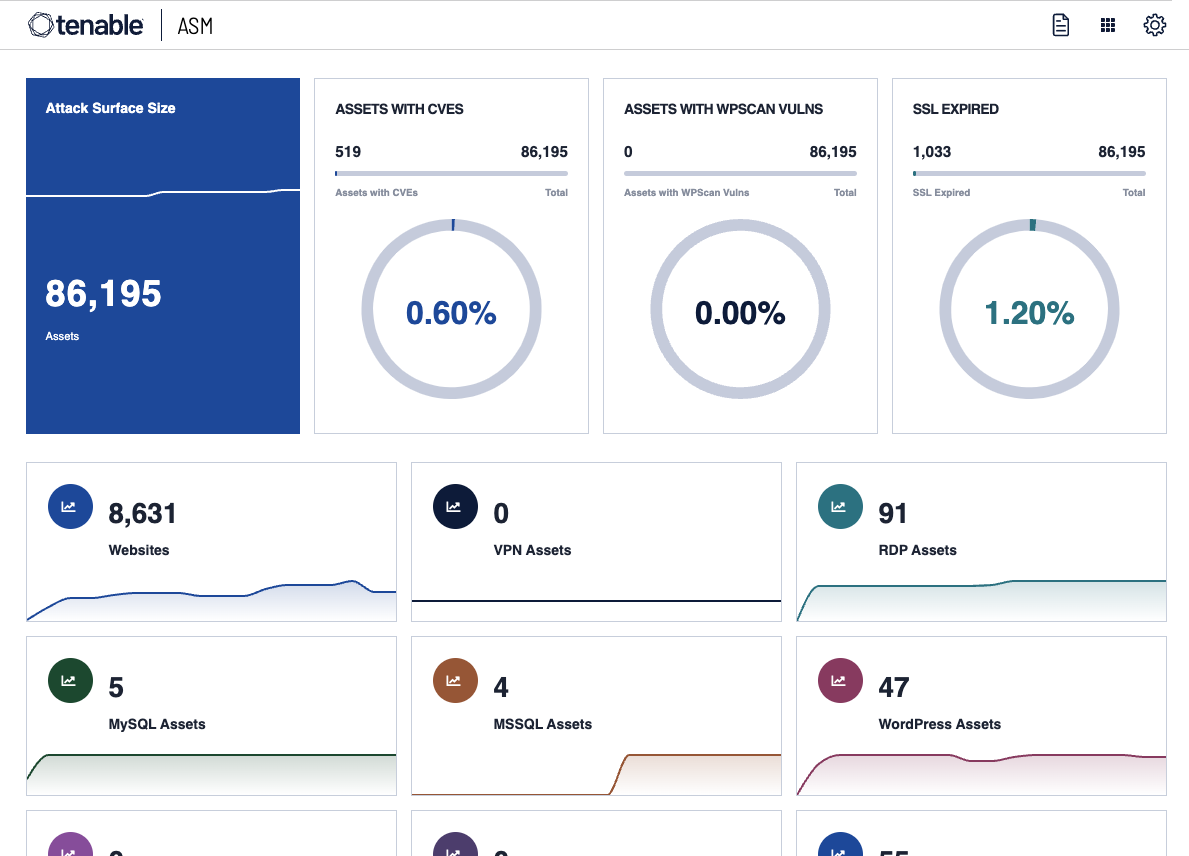
Tenable describes itself as an ‘exposure management company’. As well as the classic ASM feature set, it also offers a wider set of security exposure tools as part of the Tenable One platform. This includes web application scanning, operational technology security, and some privileged access management.
Pros:
The dashboard is very informative and gives an overview of crucial data such as system status, scanner status, plugin details, and Repo statistics.
– Tenable user review, via G2
- Comprehensive visibility: Tenable effectively detects known and unknown assets across the organization, helping to enable proactive threat detection.
- Vulnerability detection: The vulnerability detection tools are also praised for their wide compatibility and comprehensive dashboards.
- Flexible reporting: The reporting functionality is detailed and flexible, offering wide options for customization.
Cons:
The dashboard is very informative and gives an overview of crucial data such as system status, scanner status, plugin details, and Repo statistics.
– Tenable user review, via G2
- Challenging deployment: Many reviewers have criticized the platform for a complex initial setup and limited integrations.
- UI Design: The user interface of Tenable is less straightforward and simple than those of other competitors on this list.
- Resource-intensive: The scanning process also consumes significant resources, affecting the performance and usability of your systems during scans.
Reviews:
- G2: 4.5/5 stars (527 reviews total)
10. Halo Security: ASM
Our final vendor is another EASM specialist. Halo Security offers asset discovery, vulnerability assessment, and manual pen-testing tools, generally tailored towards mid-sized organizations.
The platform is praised for its straightforward layout and user experience. However, some users mention that the pricing structure is confusing and the reporting tools are rigid and difficult to use.
Pros:
Intuitively easy to use with a minimal learning curve, so all staff can be trained quickly if needed. Also, the customer service is top-notch and has answered all our questions quickly every time we reached out to them.
– Halo Security user review, via Gartner
- Ease of use: Halo Security is widely considered to have a simple and straightforward user interface.
- Customer support: Reviewers regularly praise the customer service team for its timely and knowledgeable responses.
- Risk prioritization: The platform features effective tools to help diagnose and prioritize particular vulnerabilities and issues. This includes a weekly summary email containing actionable recommendations for customers.
Cons:
Compliance reporting feature requires regular reports every 90 days, which is a manual process. Unfortunately, this is easily missed by the internal team and requires some attention to process. The pricing of this feature is also quite expensive, but legal requirements force us to buy into it.
– Halo Security user review, via Gartner
- Integrations: Halo Security has limited integrations, particularly with SIEMs and other ticketing tools.
- Reporting: Many reviewers mention that creating compliance reports is overly manual and time-consuming.
- Pricing: Halo Security is among the more expensive products on the market. It also charges based on the number of targets being monitored, which some reviewers find confusing and unpredictable.
Reviews:
- Gartner: 4.6/5 stars (89 reviews total)
- G2: 4.5/5 stars (3 reviews total)
Beyond ASM: A Complete Security Platform
There are several effective and popular ASM/EASM tools in this list. But most have one thing in common: They’re a single-purpose cybersecurity solution.
ASM is important – but it’s not the only tool in your arsenal. As well as this, you’ll also need tools to cover privileged access management, threat detection, antivirus, DNS monitoring, and a whole range of other security functionality.
Crucially, there is significant overlap between ASM and many of these. This risks creating an unwieldy and expensive cybersecurity posture, with multiple tools, licenses, and products all jostling to solve the same fundamental issues, but from a slightly different perspective.
Instead, Heimdal offers a single cybersecurity platform through one integrated license. This includes all the standard ASM functionality we’ve discussed in this blog, alongside privileged access management, email security, DNS monitoring, and much more.
Get in touch to find out more and request a bespoke pricing plan.
Top Attack Surface Management Tools: FAQs
What Is an Attack Surface Management Solution?
ASM tools continuously discover, monitor, and analyze an organization’s external-facing assets to identify potential vulnerabilities. This helps security teams to reduce attack surface risks across the organization.
What Are Some Methods Used to Reduce the Attack Surface?
To reduce your overall attack surface, it’s important to minimize the number of entry points and security gaps that hackers can exploit. Common methods include disabling unused services, enforcing least privilege access, and regularly patching software.
Which is the Best Attack Surface Management Tool?
Heimdal is one of the most effective tools to help manage your organization’s attack surface. Unlike traditional existing security tools, it doesn’t just stop at software vulnerabilities and identifying user accounts. Instead, it offers the full suite of cybersecurity protections, including privileged access management, email management, DNS security, advanced threat detection, unified endpoint management, and more. This is the best way to manage the ever-expanding attack surfaces and cloud environments that today’s organizations rely on.
Can ASM Identify Critical Vulnerabilities?
Yes, attack surface management (ASM) can identify most critical vulnerabilities by continuously monitoring exposed assets, which streamlines security operations for IT teams. These products also help to prioritize risks based on severity and exposure. However, no tool can give you a 100% accurate account of how critical a vulnerability is to your specific IT environment.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







