Contents:
BazaLoader malware developers came up with a new idea in an attempt to deceive their victims into opening malicious documents.
The threat actors responsible for the BazaLoader malware are currently sending fake messages to website owners alerting them that their site has been engaged in a Distributed Denial-of-Service (DDoS) attack.
According to BleepingComputer, the notifications include a legal warning and a file saved in a Google Drive folder that reportedly offers some sort of proof of the cyberattack’s origin.
The DDoS attack idea is an alternative to another enticement, a Digital Millennium Copyright Act (DMCA) contravention complaint connected to a document that allegedly holds proof about stealing pictures.
BleepingComputer has seen submissions where the BazaLoader malware actor employed Firebase URLs to push BazaLoader.
The threat actor’s objective is to use these forms in order to spread the virus that usually drops Cobalt Strike. Cobalt Strike is a threat imitator software released in 2012 which can be used to deploy beacons on systems to simulate cyberattacks and test network defenses.
The use of this imitator can lead to data theft or ransomware attacks.
Back in April, Microsoft threat experts have noticed that hackers were misusing contact forms published on websites in order to deliver malicious links to organizations. How? By using emails with fake legal threats.
In the emails, the victims were told to access a link to take another look at alleged evidence regarding their assertions, but instead, they clicked on IcedID, an info-stealing malware.
The recent operations are similar, only the payload and the lure are different.
As stated by Brian Johnson, two of his clients received legal notices about their sites being hacked to execute DDoS attacks against Intuit and Hubspot.
According to BleepingComputer, the sender threatened the victims with legal action if they didn’t “immediately clean” their website of the malicious files that helped carry out the DDoS attack.
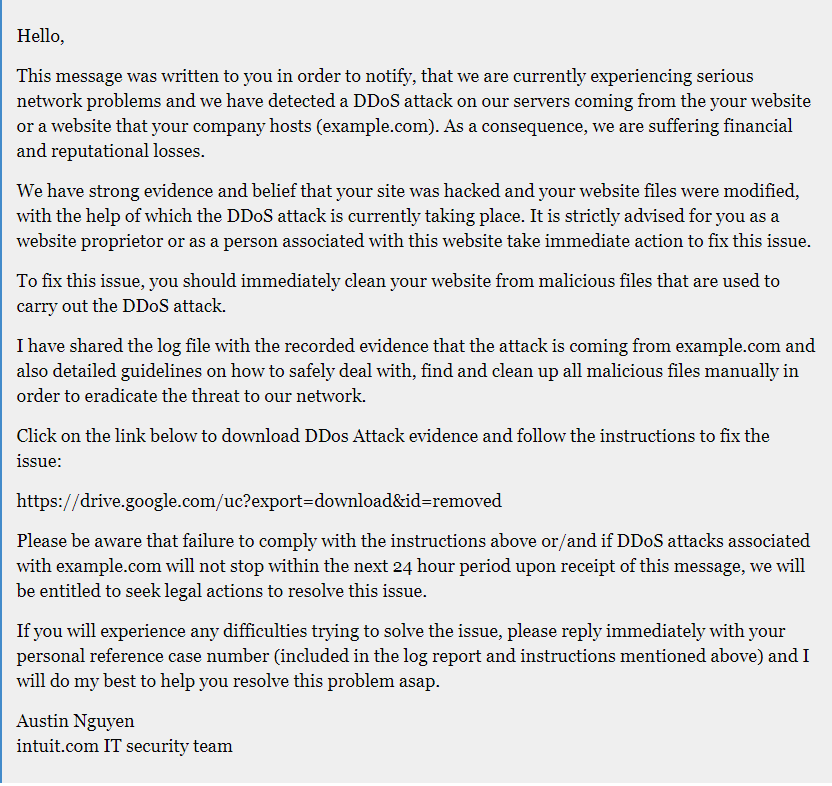
In order to make the situation look like an emergency, the threat actor also says that the website owner is “possibly be liable for statutory damage as high as $120,000.” It is all part of the delivering malware scheme, of course.

Following an investigation conducted by malware expert Brad Duncan, it has been found that it was a ZIP archive with JavaScript that fetches the BazaLoader DLL, a backdoor imputed to the TrickBot group that commonly causes ransomware incidents. The malware then reaches its command and control (C2) server and gets Cobalt Strike.
Unfortunately, there are chances that the email security solutions you have won’t consider these notifications risky as they can be very persuasive and use the validity of the contact form emails.
In order to stay away from these tricks you can try and be aware of the following signs:
- incomplete contact information
- erroneous grammar
- dubious links


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










