Contents:
ACSC, The Australian Cyber Security Centre issued a warning related to an increase in LockBit 2.0 ransomware attacks against Australian organizations.
ACSC has observed an increase in reporting of LockBit 2.0 ransomware incidents in Australia.
It is concerning to see that the LockBit victims are reporting threats related to their data being leaked online alongside the usual ransomware requests.
The majority of victims known to the ACSC have been reported after July 2021, indicating a sharp and significant increase in domestic victims in comparison to other tracked ransomware variants.
The ACSC has observed LockBit affiliates successfully deploying ransomware on corporate systems in a variety of sectors including professional services, construction, manufacturing, retail and food.
ACSC also published a ransomware profile that offers additional information about the LockBit ransomware group as it includes initial access indicators, targeted sectors, as well as mitigation measures.
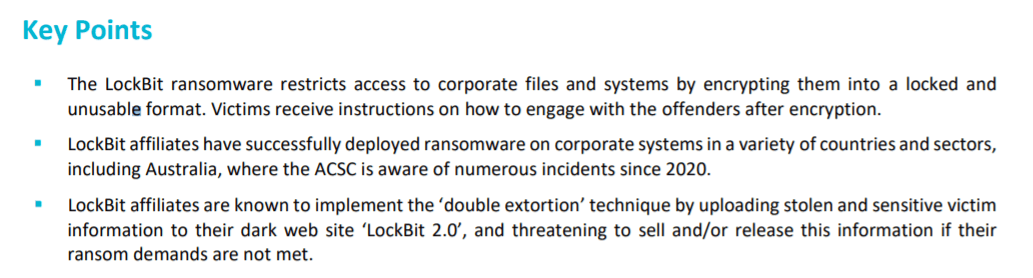
In the report it was also mentioned that the threat actors from Lockbit Ransomware are opportunistic, therefore being able to target organizations in any industry sector.
The ACSC provided in the material a series of mitigation tactics focused on LockBit TTPs (Tactics, Techniques, and Procedures):
- enabling multifactor authentication (MFA) on all accounts to block the use of stolen credentials
- encrypting sensitive data at rest to block exfiltration of sensitive information
- segmenting corporate networks and restricting admin privileges to block lateral movement and privilege escalation attempts
- maintaining daily backups to reduce a successful attack’s impact
- patching internet-facing Fortinet devices against CVE-2018-13379, a security bug heavily exploited by LockBit to breach networks
Some Background Information on the Lockbit Ransomware
LockBit ransomware started operating back in September 2019. The group works as a ransomware-as-a-service (RaaS) by recruiting threat actors to breach networks and encrypt devices.
Since it was launched, LockBit has been extremely active, as the gang representatives were promoting the RaaS and providing support on various Russian-language hacking forums.
LockBit launched the LockBit 2.0 RaaS back in June, and it seems that the ransomware gang is trying to gain some traction following the slowdown noticed in their attacks since January.
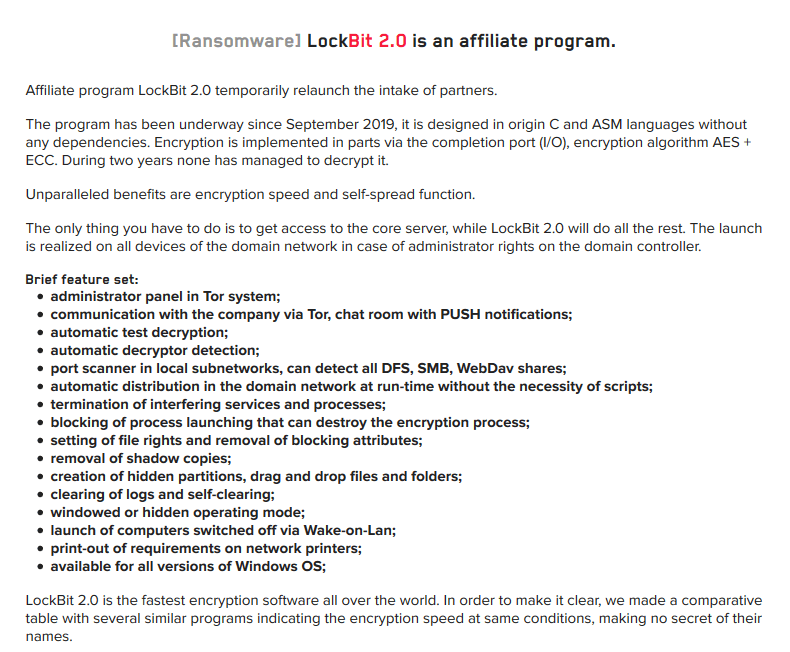
Lockbit 2.0 came with redesigned Tor sites and advanced features, that are including automatic encryption of devices across Windows domains by using the Active Directory group policies.
It’s interesting to note that LockBit 2.0 is attempting to remove the middlemen by trying to recruit insiders in the hope they would provide the ransomware group with access to corporate networks through Remote Desktop Protocol (RDP) and Virtual Private Network (VPN).


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security