Contents:
Another good news in the world of ransomware attacks! Czech multinational cybersecurity software organization Avast has recently developed and published a decryptor that will help those affected by AtomSilo and LockFile ransomware attacks get back some of the encrypted files for free.
BleepingComputer announced yesterday that Avast also released a free decryption tool for the victims of Babuk ransomware.
According to the antivirus software company, this decryptor may be unable to decrypt files in unknown, proprietary, or non-existent formats.
During the decryption process, the Avast AtomSilo decryptor relies on a known file format in order to verify that the file was successfully decrypted. For that reason, some files may not be decrypted.
Even though the gangs that deliver the ransomware on victims’ systems employ distinct attack strategies, the decryption tool can be used for both ransomware types as they are very similar.
According to Avast Threat Labs, this decryption tool was developed together with RE – CERT malware researcher Ji Vinopal, who has recently discovered a flaw in the AtomSilo ransomware strain.
Something big -> I just cracked #AtomSilo – one of the Latest Ransomware Family – More information soon. Stay Tuned. (cde07f39b45b883c861f4d4d0c6afb80)
For more information (Only for trusted Security accounts) DM me.?
Please help me to reach more People who could be affected!!!— Jiří Vinopal (@vinopaljiri) October 17, 2021
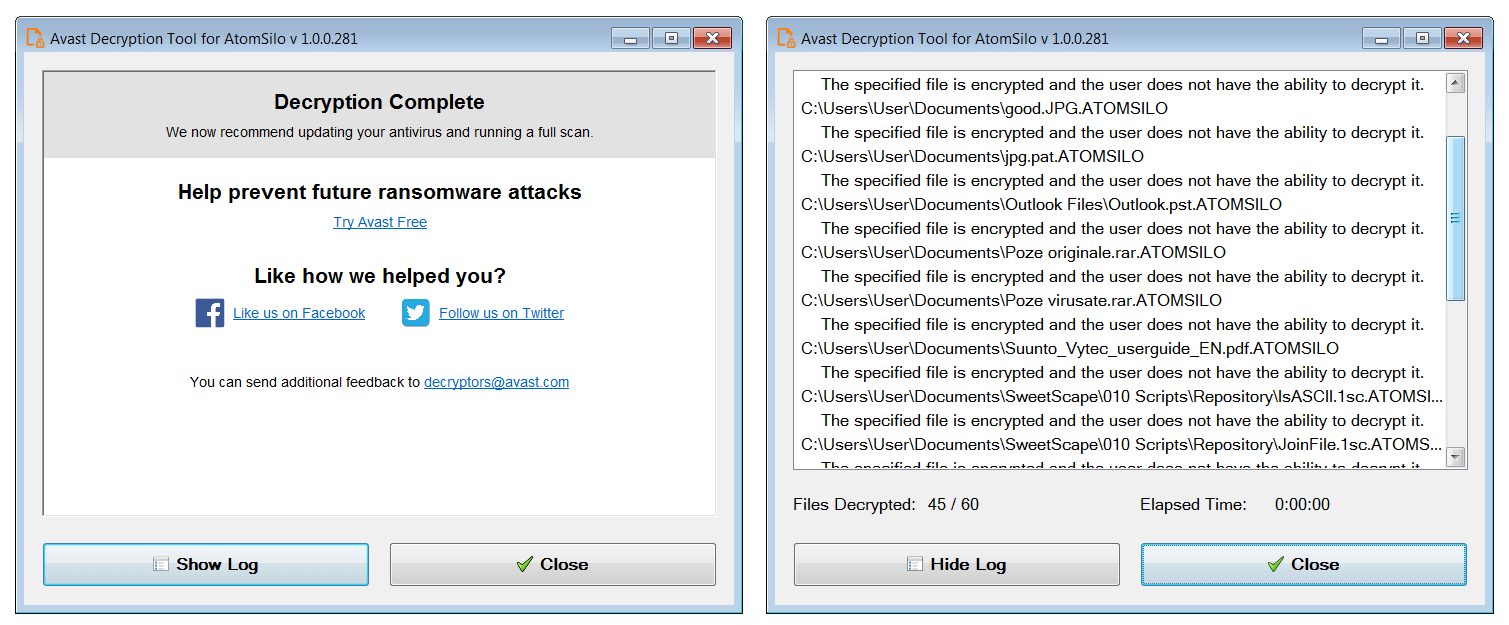
As explained by BleepingComputer, entities impacted by AtomSilo and LockFile can download the decryptor from Avast’s servers and decrypt entire disk partitions by following the steps shown in the decryptor’s user interface.
Using Avast’s free decryptor, the tech news publication tested the recently released tool and got back the files encrypted with an AtomSilo sample.
Earlier this year, we were writing about a new malware that started to target Microsoft Exchange servers, performing Windows domains encryption. The LockFile ransomware abused ProxyShell and PetitPotam vulnerabilities.
As explained by BleepingComputer, the LockFile ransomware will add the.lockfile extension to the names of encrypted files and drop ransom messages in the ‘[victim name]-LOCKFILE-README.hta’ format when encrypting them.
At the beginning of the month, we saw that AtomSilo started targeting confluence servers. SophosLabs researchers made the discovery while analyzing a recent event. They also found that the ransomware employed by this new organization is nearly comparable to LockFile, which is extremely similar to the LockBit malware.
Operators of the AtomSilo, on the other hand, employ “a number of innovative tactics that make it exceedingly difficult to examine, including the side-loading of malicious dynamic-link libraries designed to disrupt endpoint security software.”
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








