Contents:
Threat groups exploited two recent Atlassian Confluence vulnerabilities to deploy Cerber ransomware.
On October 31st, Atlassian released security updates for both flaws and urged users to patch. Both flaws, CVE-2023-22518 and CVE-2023-22515, are ranked 10 which is the maximum risk level.
- CVE-2023-22515 enables hackers to create unauthorized Confluence administrator accounts. Threat actors can then access Confluence instances and compromise data confidentiality, integrity, and availability.
- CVE-2023-22518 is an improper authorization vulnerability. It enables hackers to reset Confluence and create a Confluence instance administrator account. Further on, the attackers can use the account to gain admin rights in the Confluence instance administrator. Then they can access, change, and steal data.
On November 6th, Atlassian said they noticed threat actors actively exploiting the CVE-2023-22518 flaw in ransomware attacks:
As part of Atlassian’s ongoing monitoring and investigation of this CVE, we observed several active exploits and reports of threat actors using ransomware. We have escalated CVE-2023-22518 from CVSS 9.1 to 10, the highest critical rating, due to the change in the scope of the attack.
Security researchers say hackers exploited the Atlassian authentication bypass flaw to encrypt files with Cerber ransomware.
Prevention and Mitigation Measures
Atlassian stated that all versions of Confluence Data Center and Server are affected by CVE-2023-22518. In addition, according to ShadowServer`s data, more than 24,000 Confluence instances are exposed online. However, for the moment it is not clear how many are vulnerable to CVE-2023-22518 attacks.
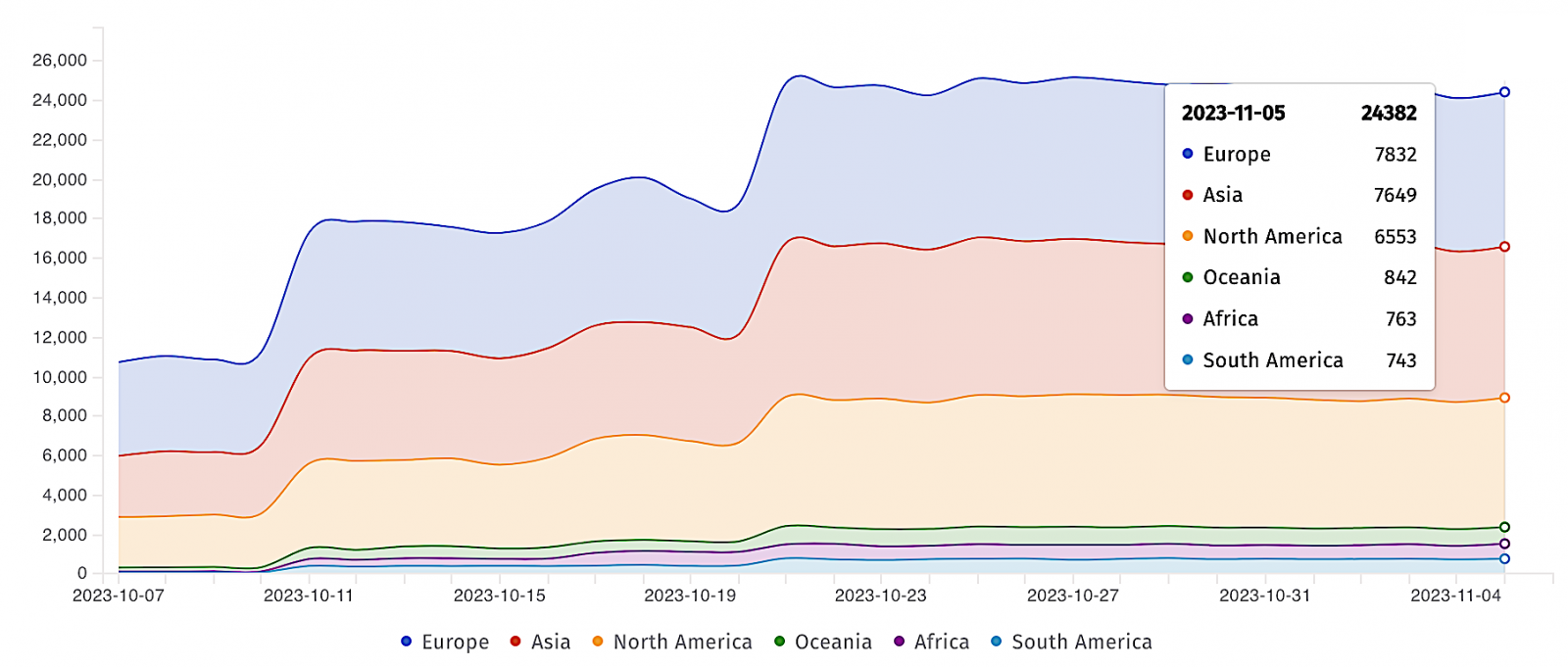
Source – BleepingComputer.com
All in all, publicly accessible Confluence Data Center and Server versions are at critical risk, and you should patch immediately, if possible.
If patching is not an option for your version, you can apply the following mitigation measures:
- Back up your instance
- Take your instance offline until you can patch, if possible.
- If restricting external network access or patching are not possible, apply the following interim measures. This will block access on the following endpoints on Confluence instances:
- /json/setup-restore.action
- /json/setup-restore-local.action
- /json/setup-restore-progress.action
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









