Contents:
Another one bites the dust, we might say. It has been recently made public that the cybercriminal responsible for the not-so-famous AstraLocker ransomware is ceasing operations and intends to switch to cryptojacking.
The threat actor behind the ransomware uploaded to the VirusTotal malware analysis platform a ZIP archive containing AstraLocker decryptors.
According to BleepingComputer, which downloaded the ZIP archive, the decryptors are valid and functional following the testing of one of them against files encrypted in the latest AstroLocker ransomware attack.
Although they only analyzed one decryptor that effectively decrypted files locked in a single operation, other decryptors contained in the archive were probably created for files that were encrypted in earlier cyberattacks.
As per BleepingComputer, AstraLocker’s developer stated:
It was fun, and fun things always end sometime. I’m closing the operation, decryptors are in zip files, clean. I will come back. I’m done with ransomware for now. I’m going in cryptojaking lol.
Why Did AstraLocker Cease Operations?
The threat actor did not explain why AstraLocker was shut down, but it was probably because of the sudden attention the operation received as a result of recent reports, which put it in the sights of law enforcement.
Emsisoft, a software organization that is well known for assisting ransomware victims with data decryption, is currently developing a universal decryptor for AstraLocker ransomware, which will be made available in the future.
Although this doesn’t happen more frequently, there are also other ransomware organizations that have provided BleepingComputer and security experts with decryption keys and decryptors as a gesture of good faith when closing down or announcing new variants.
What Do We Know About AstraLocker Ransomware?
As threat intelligence company ReversingLabs recently disclosed, compared to other ransomware strains, AstraLocker employed a somewhat unconventional technique to encrypt the devices of its targets.
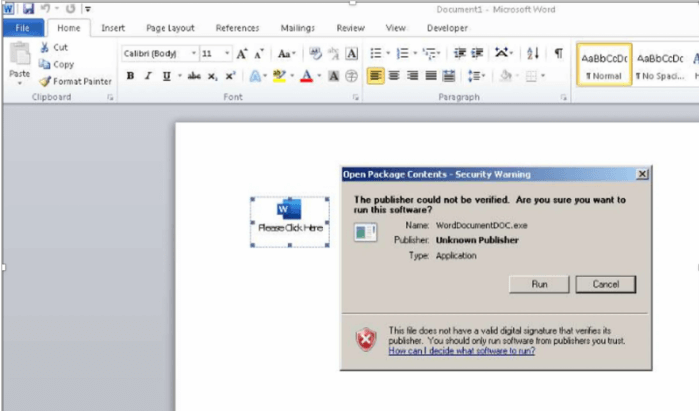
The threat actor behind pf AstraLocker would directly deploy the payloads from email attachments using malicious Microsoft Word docs rather than first hacking the machine (either through hacking it or purchasing access from other cybercriminals).
The enticements used in AstroLocker campaigns include documents that conceal an OLE object containing the ransomware payload, which is activated when the victim clicks on the “Run” button in the warning dialog that appears when the document is opened.
Before file encryption, the ransomware will inspect to see if it is functioning in a virtual machine, halt processes, and disable backup and antivirus software that would interfere with the encryption process.
According to ReversingLabs’ analysis, Babuk Locker (Babyk) ransomware source code, a flaky but still destructive version that left the market in September 2021, served as the foundation for AstraLocker.
Furthermore, one of the Monero wallet addresses in AstraLocker’s ransom message was associated with the threat actors behind Chaos ransomware.
How Can Heimdal Help?
Ransomware is the most popular threat nowadays with advanced techniques hard to fight. It’s important to have the best cybersecurity solutions especially if you want to keep your business protected and up and running. Do not let ransomware give you a bad time and check out our Ransomware Encryption Protection will help your company stay away from malicious encryption attempts, and is packed with efficient detection features.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










