Contents:
Managing user privileges is a critical task for any organization. This article aims to guide you through the process of assigning user privileges in Heimdal, ensuring a secure and efficient management of your cybersecurity infrastructure.
Key Takeaway Summary
- Understanding User Access Control in Heimdal;
- Setting Up and Assigning User Privileges;
- Analyzing and Responding to User Access;
- Monitoring User Activities and Access;
- Enforcing and Managing Access Policies;
- Privileged access management Best Practices.
Introduction to User Access Control in Heimdal
At its core, user access control revolves around the principle of ensuring that the right people have the right access at the right times.
Heimdal’s multi-layered security model integrates various components such as identity verification, role-based access control, and real-time monitoring.
By leveraging these elements, Heimdal ensures that user privileges are not only restricted based on individual roles and responsibilities but are also continuously monitored for any unusual or unauthorized activities.
One of the key aspects of Heimdal’s user access control is its user-friendly interface, which allows you to easily assign and modify user privileges.
Whether it’s granting access to new employees, adjusting permissions for existing staff, or revoking access, when necessary, Heimdal’s intuitive dashboard makes these tasks straightforward.
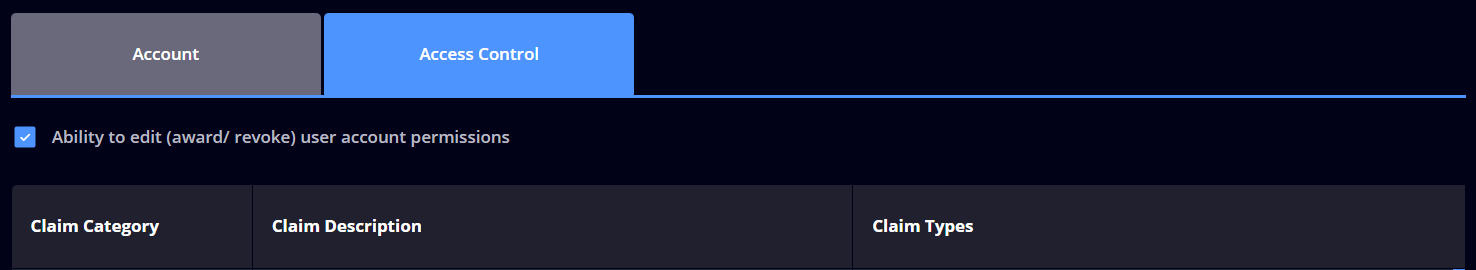
Moreover, Heimdal’s user privileges module is not just about managing permissions, and control access, it’s also about gaining insights into user behavior. Continuously monitoring privileged sessions is one of the privileged access management best practices.
The system provides detailed logs enabling administrators to track who accessed what, when, and from where. This level of detail is invaluable for auditing purposes and for investigating security incidents.
Keep reading the specifics of setting up and managing user privileges in Heimdal, as it becomes clear that it is not just about controlling access; it’s about empowering your organization to maintain a secure and efficient operational environment.
Setting Up and Assigning User Privileges
Setting up access permissions in Heimdal is a straightforward yet impactful task, ensuring that each user has access only to the resources necessary for their role.
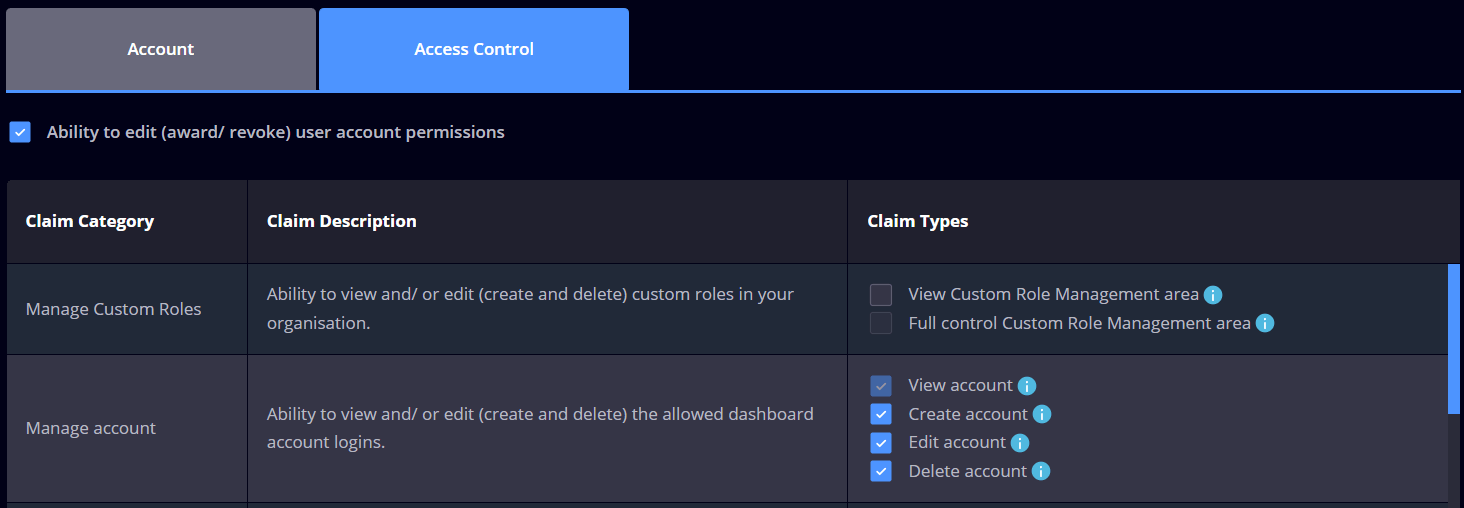
Assigning Roles and Responsibilities
Heimdal allows you to assign roles to each user, which dictates the level of access they have. These roles can range from basic users, who have limited access, to administrators, who have full access to the system.
Configuring Access Levels
For each role, configure the specific access levels. This includes determining which files, systems, and areas of the network each role can access. Heimdal’s flexible permission settings allow for granular control, enabling you to tailor access precisely.
Reviewing and Testing Configurations
Once you have set up the access permissions, review and test them to ensure they work as intended. This step is crucial to identify any potential gaps or oversights in the access control setup.
Analyzing and Responding to User Access
Let’s see what the essential steps in maintaining the security and integrity of your IT environment are:
Regular Review of Access Logs
The first step is to schedule regular reviews of access logs to understand user behavior and detect any potential security issues.
Investigating Anomalies
If an anomaly is detected, such as an unauthorized access attempt or a deviation from typical user behavior, investigate promptly. Determine the cause of the anomaly and assess whether it poses a security risk.
Taking Corrective Actions
If a security risk is identified, take immediate corrective action. This may involve revoking user session access, changing passwords, or even involving legal or law enforcement authorities in cases of suspected malicious activity.
Monitoring User Activities and Access
Effective monitoring of user activities and access is a cornerstone of maintaining a secure IT environment, and this section will guide you through the process.
Real-Time Alerts
Heimdal notifies you whenever an end-user requests admin privileges over his/her machine by sending a request to you, the HEIMDAL Dashboard Administrator who can deny or accept his/her request. The length of the session is limited, and all his/her actions are logged into the HEIMDAL Dashboard.
If the Require reason option is enabled in the Group Policy, the user will receive a pop-up to add details for the elevation request. This step is skipped if Require reason is disabled.
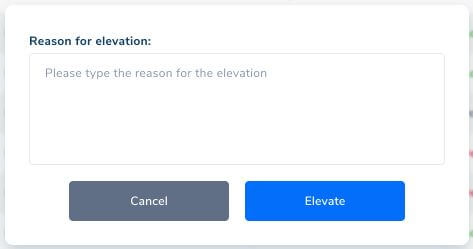
After clicking Elevate, depending on the Group Policy configuration, a request is sent to the server, to ask permission from you, the HEIMDAL Dashboard Administrator.
If Approval via Dashboard is selected in the Group Policy, then the left popup below will appear.
If Auto-mode is selected in the Group Policy, the right pop-up will appear, and the elevation will be automatically granted.
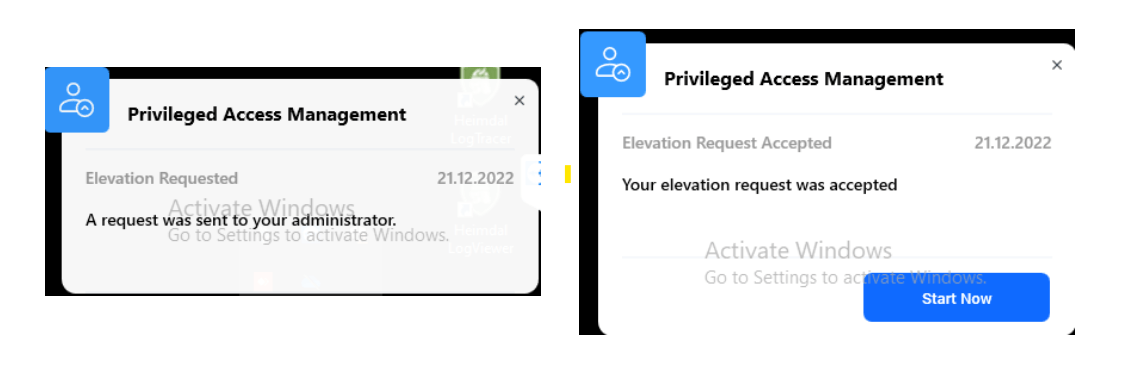
After clicking Start Now, the below popup will appear to inform the user that the file has been elevated.
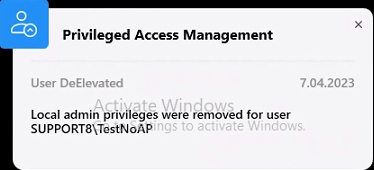
Heimdal’s dashboard offers analytics tools that provide insights into user behavior patterns. Regularly review these analytics to understand normal usage patterns and quickly identify any deviations that might indicate a security concern.
User Activity Logs
Heimdal provides comprehensive logging capabilities that record user activities within the system.
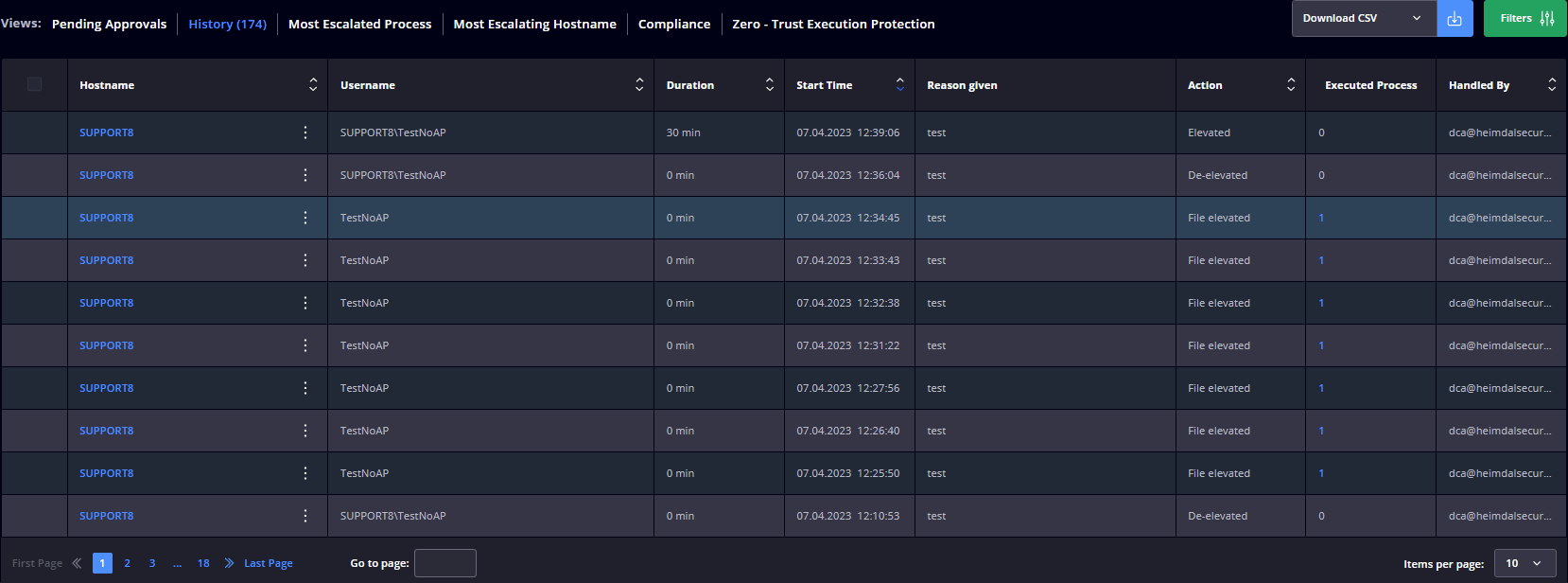
The Privileges & App Control – Privileged Access Management view displays all the information collected by the HEIMDAL Agent that is running on the endpoints in your organization.
The collected information is placed in the following views: Pending Approvals, History, Most Escalated Process, Most Escalating Hostname, Compliance, and Zero-Trust Execution Protection.
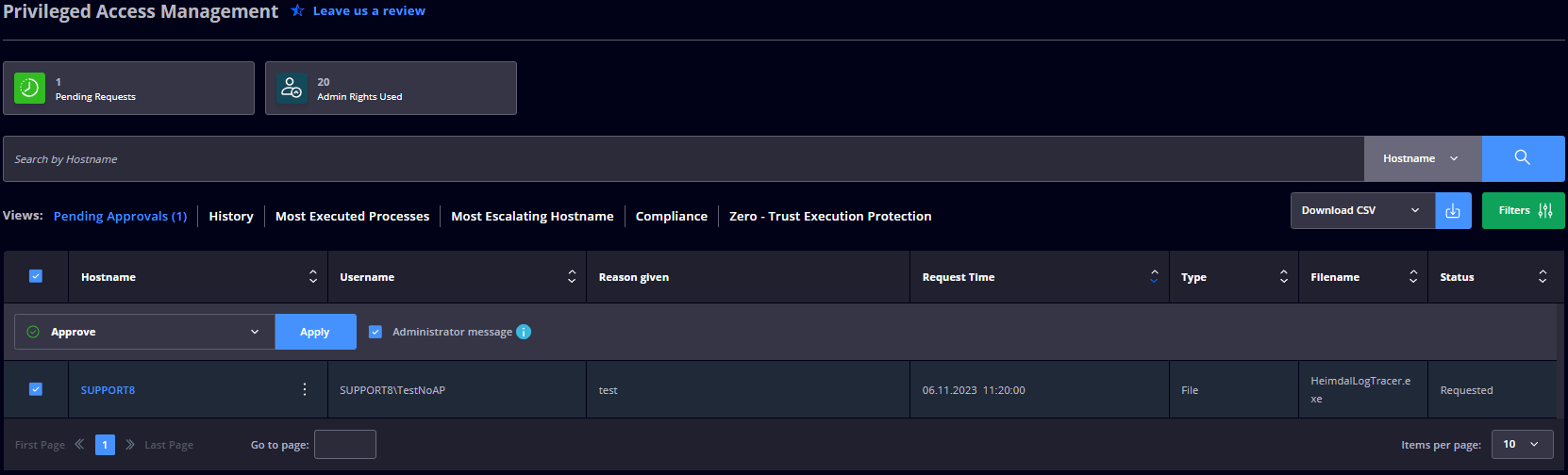
Pending Approvals
This view displays a table with the pending elevation requests and the following details: Hostname, Username, Reason given, Request Time, Type, Filename, and Status. If the Status is Requested and written in red, this means the endpoint is running a 3rd Party Application that has a vulnerability with a CVSS score of 7 or higher.
History
This view displays a table with the elevated/de-elevated requests and the following details: Hostname, Username, Duration, Start Time, Reason Given, Action, Executed Process(es) and Handled By.
Most Executed Processes
This view displays a table with the number of executed processes (during the elevated session) and the following details: Process Name, Number of Executions, Hostname, and Username.
Most Escalating Hostname
This view displays a table with the number of escalating hostnames and the following details: Hostname, Username, and Total Number of Elevations.
Compliance
This view displays a table with the compliant endpoints and the following details: Hostname, Active User, Domain Name, Local Groups, AD Groups, and Admin rights (Y/N). The Local Group field populates if the active user is found in any of the local groups or AD Groups. If it is found, it is marked as Admin (Yes).
Zero – Trust Execution Protection
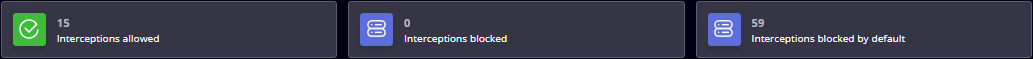
This view displays a table with the processes (non-signed executable files) intercepted by the Zero-Trust Execution Protection engine and the following details: Hostname, Username, Process Name, MD5 Hash, Timestamp, and Status. Clicking the 3-dot button will give you the option to search the file hash on VirusTotal or to Copy the file path to the Clipboard.
The status of detection can be: Unknown (intercepted by ZTEP and not found in our database), Allowed (intercepted by ZTEP, but whitelisted in our database).
Implementing Access Control Policies
In Heimdal, this means not only defining who can access what, but also ensuring that these access privileges are granted in a way that aligns with the overall security strategy of your organization.
Establishing Your Access Control Framework
Here are the steps in establishing a successful access control framework:
Defining Access Levels
Start by categorizing your data and systems based on sensitivity and importance. Define different access levels, such as administrator, and regular user, each with varying degrees of access rights.
User Role Assignment
Assign users to these roles based on their job requirements. Ensure that each user has the minimum level of access necessary to perform their duties effectively – a principle known as the ‘least privilege’.
Creating Custom Access Policies
Heimdal allows for the creation of custom access policies. Utilize this feature to tailor access controls that fit the specific needs of different departments or teams within your organization.
Understanding the requirements that are necessary for a strong Access Control policy is essential in safeguarding your systems, critical infrastructure, and sensitive data.
Lorna Willard, Information Security Auditor
Enforcing and Managing Access Policies
Ensuring the policies are not only established but also effectively enforced and managed is vital.
Policy Enforcement Mechanisms
Implement mechanisms to enforce these policies automatically. This includes setting up rules for password complexity, multi-factor authentication, and automatic logoffs for inactive sessions.
Regular Policy Reviews and Updates
The digital landscape is constantly evolving, and so are the threats. Regularly review and update your access control policies to ensure they remain effective against new types of cyber threats.
Handling Exceptions and Changes
Establish a clear process for handling exceptions to the standard policies, such as granting temporary access for specific projects. Also, have a procedure for updating user access when their role or job responsibilities change.
User Privileges Best Practices
Adhering to best practices can significantly improve your control over user access and overall cybersecurity.
Regular Access Reviews
Conduct regular reviews of user access rights to ensure they are still appropriate and necessary. Remove, grant access, or adjust access that is no longer needed or aligns with the user’s current role.
Implement Emergency Protocols
Have protocols in place for quickly revoking access in case of a security breach or if an employee leaves the organization.
Regularly Update Monitoring Criteria
As your organization evolves, so should your monitoring criteria. Regularly update these to ensure they remain relevant and effective.
Educate and Train Users
Educate your staff about the access control policies and the reasons behind them. This includes training on safe cybersecurity practices and the importance of adhering to access protocols.
Accelerate Approval – Application Control
If you want to accelerate your application approval or denial flow, we got you.
Application Control is designed to manage the execution of processes (or applications) on client machines, dictating how they run. It enables you to establish a series of rules that determine which processes are permitted or prohibited on the endpoints within your network.
These rules can be based on various criteria such as Software Name, Paths, Publisher, MD5, Signature, or Wildcard Path.
With App Control, you can manage the operation of a process (which may receive automatic elevation from the Privilege Elevation and Delegation Management (PEDM) module, if configured accordingly) or a subprocess (where you can permit or restrict all processes initiated by the process targeted by the rule).
Wrapping Up
By following the steps outlined in this article, you can set up, manage, and enforce robust access controls, ensuring that your organization is well-protected. But remember, effective user access control is not just about the technical setup; it’s also about fostering a culture of security awareness within your organization.
User Privileges FAQs
Q: What are access privileges examples?
A: Access privileges refer to the specific rights and capabilities granted to an authorized user account, such as permissions for read-only access, write access, access to certain patient information, and so on.
Q: What are privileges and user roles?
A: Privileges — These are allocated to a role, bestowing rights upon its members. Privileges dictate the actions a member is permitted or prohibited from performing within the organization.
While the privileges associated with default roles are fixed and unalterable, an organization administrator has the authority to assign and modify the privileges linked to custom roles.
Q: What are privileged user rights?
A: A privilege represents the authority granted to a user account to execute specific system operations, like shutting down the computer or modifying the system time. The Privilege Management functionality allows you to allocate (enable) or restrict (disable) these privileges.
Q: What is considered a privileged user?
A: A user who is authorized and trusted to carry out security-sensitive functions that are not permitted for regular users.
Q: What are administrator privileges?
A: The rights granted to a user enabling them to execute specific tasks within a system or network, like installing software or modifying configuration settings.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








