Contents:
Researchers discovered a new fake ChatGPT extension for Chrome in the official Chrome Store. This version steals Facebook session cookies, hijacking accounts.
The malicious extension is a copy of “ChatGPT for Google”, a Chrome add-on, but with additional malicious code. Since its release, the trojanized version had over 9,000 downloads.
Details About This Fake ChatGPT Extension
Researchers at Guardio Labs say that the extension was published on the Chrome Web Store on February 14, 2023. But threat actors started to advertise it in Google Search results only on March 14, 2023. This led to almost a thousand downloads daily from people that are searching for “ChatGPT 4.”.
This fake extension seems to be part of a larger campaign. As earlier this month another fake ChatGPT Chrome add-on was released and lurked 4,000 people before its removal.
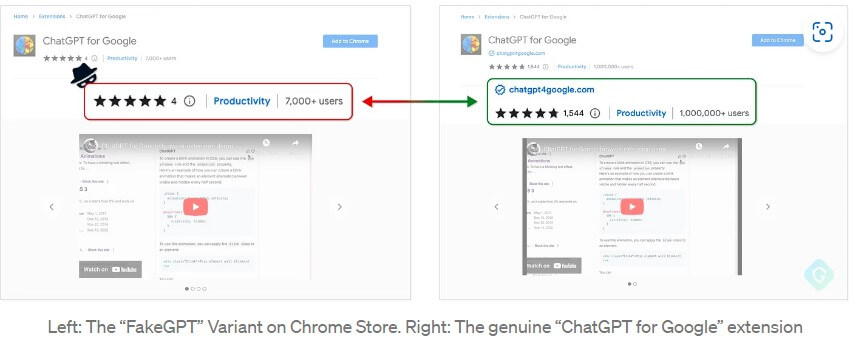
Both versions used the same infrastructure to communicate and it is not excluded that this new attempt is in fact a backup. Cybercriminals decided to activate it after the official store removed the first fake extension. This can lead us to the conclusion that hackers may also have a “Plan C” in mind, meaning another fake extension, to continue this campaign.
How the Campaign Works
Those who clicked on the advertised results landed on a fake “ChatGPT for Google” page, first, then on the extension’s page on Chrome’s official store.
Victims who installed the extension got all the advertised features, as the original code is still there. But also got a malicious code that steals session cookies for Facebook accounts using the OnInstalled handler function.
Using the cookies, threat actors were able to log into a Facebook account with full access. They used the hijacked accounts for advertising campaigns or to spread forbidden information like ISIS messaging.
The malware abuses the Chrome Extension API to acquire a list of Facebook-related cookies and encrypts them using an AES key. It then exfiltrates the stolen data via a GET request to the attacker’s server.
Cybercriminals steal the cookies without triggering any DPI (Deep Packet Inspection) by encrypting the cookie list with AES and attached to the X-Cached-Key HTTP header value
The ChatGPT extension changed the login details of the account, making it impossible for victims to salvage their profiles. Additionally, it changes the profile image and name to a false identity called “Lilly Collins.”
At this time, the malware was taken down from Google Chrome Web Store.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







