Contents:
Five serious vulnerabilities in hospital robots that served for the transportation of medical supplies have been patched by vendor Aethon.
Vulnerabilities Found in Hospital Robots: More Details
As recently reported in Cynerio’s public report of Jekyllbot:5, five significant zero-day vulnerabilities in Aethon TUG robots and medical equipment can fall short of adequate security safeguards.
Hundreds of hospitals rely on Aethon’s mobile robots to do basic, repetitive jobs and supplement current workforces. TUGs do errands for healthcare workers, such as delivering medications, cleaning, and dropping off linen and other supplies.
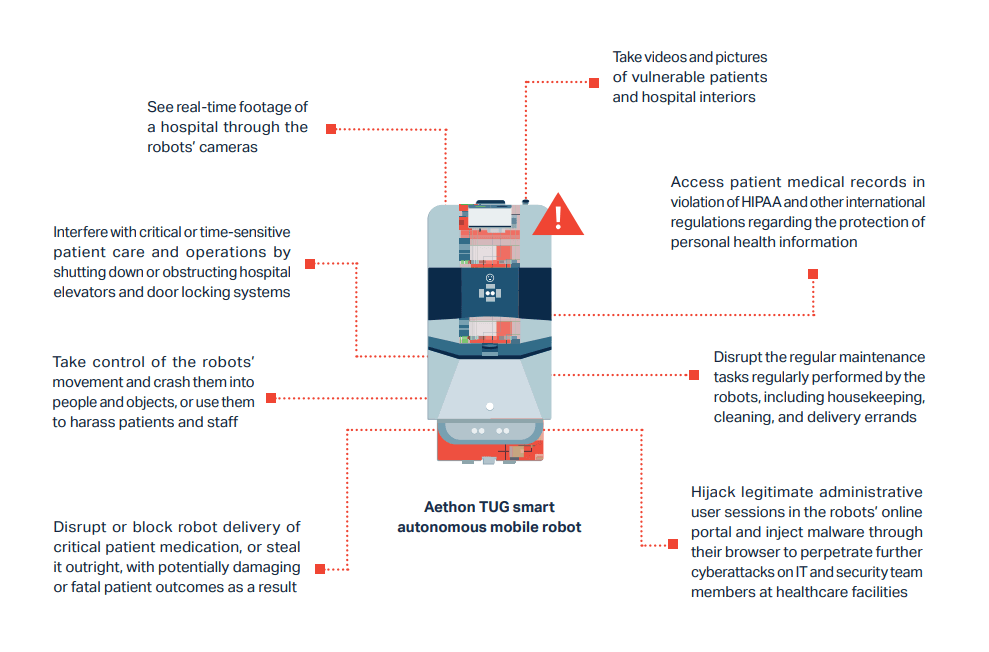
By exploiting the five discovered vulnerabilities, hackers can take control of a robot’s activities and perform a series of malicious actions that could have an impact on patient care like:
- taking photos;
- using camera feeds to snoop on the hospital in real-time;
- gaining access to records of patients;
- disrupting or blocking drug delivery.
The flaws may also be used to “take control of the robot’s movement and crash them into people or objects, or use them to annoy patients and personnel,” according to the researchers.
In their report, the security experts described thoroughly what can a hacker do if successfully exploiting these vulnerabilities:
What Are the JekyllBot:5 Vulnerabilities?
The discovered JekyllBot:5 vulnerabilities have been issued CVEs:
- CVE-2022-1066 (CVSS 8.2): because of the lack of authorization checks, a hacker could add new users using admin privileges as well as performing modifications or deletion of current users;
- CVE-2022-26423 (CVSS 8.2): this is about missing checks too, which gives free access to a threat actor to hashed user credentials;
- CVE-2022-1070 (CVSS 9.8): because of the improper check of end-users, an unauthenticated hacker has the possibility to take control over TUG robots through the TUG Home Base Server WebSocket;
- CVE-2022-27494 (CVSS 7.6): the user-controllable input is not or is incorrectly neutralized which lets the “Reports” tab within Fleet Management Console vulnerable to XSS cyberattacks;
- CVE-2022-1059 (CVSS 7.6): same problem as above, but this time the load tab of the Fleet Management Console is exposed to XSS attacks.
These vulnerabilities were identified during an audit on behalf of a client healthcare provider. While Cynerio’s customer had not connected their robots to the internet, making them immune to active hacking, the cybersecurity firm stated “many” hospitals in the Cynerio Live research lab had internet-connected robots that could be controlled remotely, according to ZDNet.
The vendor received notification about the vulnerabilities from the US Cybersecurity and Infrastructure Security Agency (CISA).
What Measures Have Been Taken?
Cynerio collaborated with Aethon to issue appropriate patches, which are now included in the newest version of TUG firmware. Aethon also produced firewall modifications for customer hospitals in order to limit public access.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










