Contents:
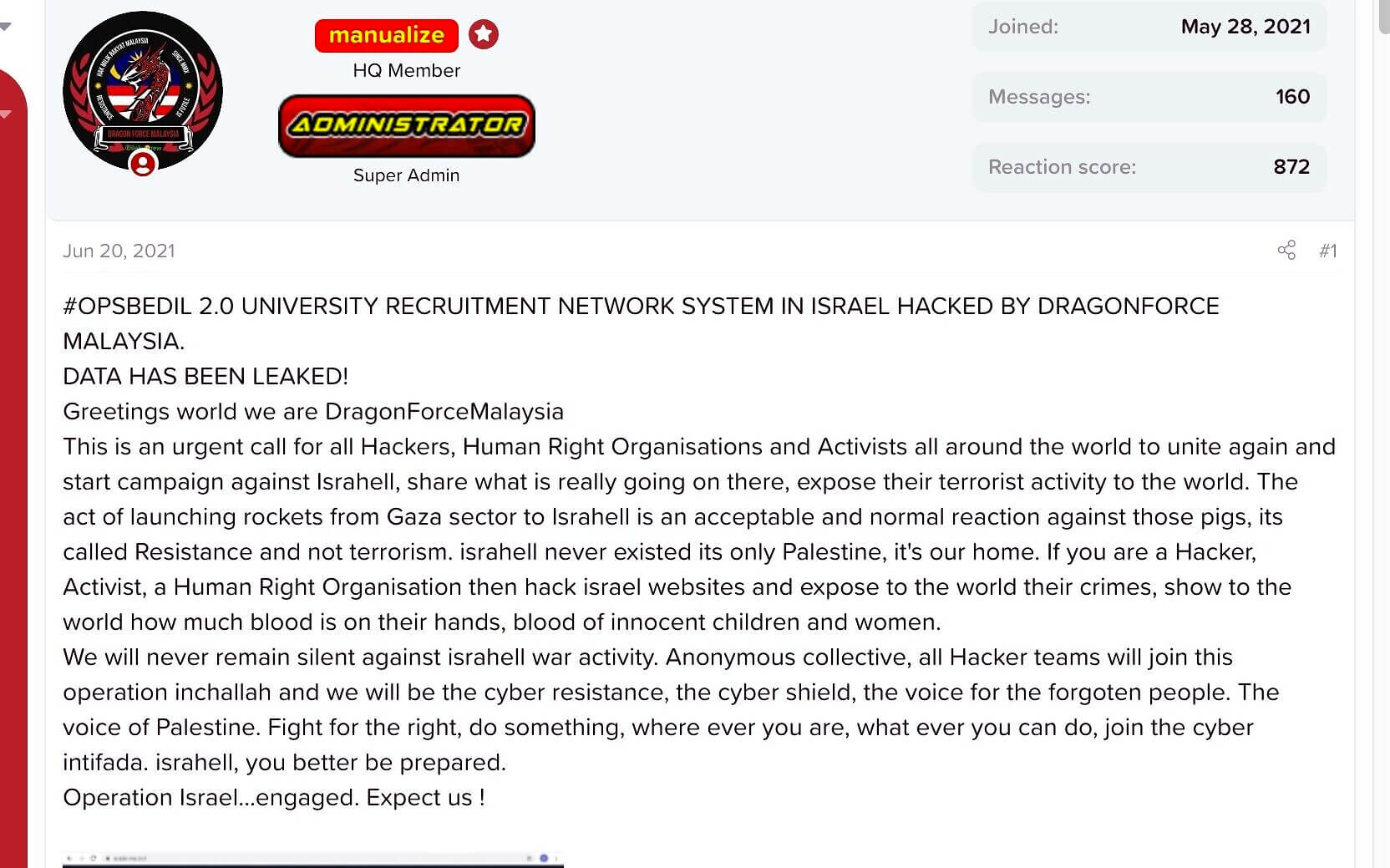
A Telegram message via Telegram App on the 20th of June revealed an AcadeME data leakage cyberattack. DragonForce, a pro-Palestinian Malaysian threat actor group, hacked the company’s systems and exposed confidential data of about 280,000 Israeli students.
What Is AcadeME?
AcadeME is an Israeli-based recruitment network company that collaborates with big universities and helps students and graduates to find a suitable job, optimizing the match between them and open positions by handling the entire hiring process. The institutions AcadeME works with are the University of Haifa, Bar-Ilan University, Tel Aviv University, Ben Gurion University of the Negev, the Open University, and many more. Its focus stays on career development and it stands for a job-seeking platform different from a Customer Relationship Management (CRM) or from an Applicant Tracking System (ATS).
What Information the AcadeME Data Leakage Exposed
Last week, DragonForce, a pro-Palestinian Malaysian group of hackers disclosed in a notification the fact that they hacked the AcadeME’s systems and got hold of students’ confidential data.
The AcadeME data leakage included students’ records even since 2014:
- Student names
- Passwords
- E-mail addresses
- Phone numbers
- Home address
- Codes
- Server addresses
The hackers announced the attack on their website and leaked the student’s information via the Telegram app on Malaysian groups.
The Reason Behind
The reason behind the cyberattack, called the operation #OpsBedil 2.0”, which comes out from the DragonForce threat actors group’s post, seems to be a response to the recent hostility between Israel and Gaza.
Cyberattacks: In a Row
It is known that cyberattacks have been endless recently. Yigal Unna, the chief of INCD (Israel National Cyber Directorate), sent previously this year a message of awareness publicly saying that Israeli academic organizations could be severely shattered if threat prevention actions are not implemented. He pointed out the danger of these ceaseless data breaches that could have the power to disable the organization’s activities and even damage the universities’ reputation, as TheJerusalemPost states. This message was sent in a letter intended to the Committee of Heads of Universities, only 11 days after Ben-Gurion University of the Negev suffered a data breach on its servers performed by an unknown threat actor.
The above-mentioned Dragonforce, however, did not break the ice with this sole information disclosure. On the same day the AcadeME data leakage was brought to the public’s attention, the hackers’ group admitted possessing a lot of Israeli passports. Then on Friday, Israeli banks were targeted by DDoS attacks. Dragonforce attacked Mizrahi Tefahoy bank, Bank Leumi, and the Bank of Israel.
Dragon Force also targeted government and residence agencies in an attack from last month, being the authors of that cyberattack that hacked the Israeli CCTV Networks.
What Measures Have Been Taken?
An in-depth investigation is now ongoing. May-Brooks Kempler, the cybersecurity expert who manages the Facebook Group “Think Cyber Safe”, is currently looking over the effects produced by the AcadeME data leakage. She advised users to take some basic security measures such as password changing and be on guard when it comes to peculiar phone calls, text messages, or e-mails, the Times of Israel Publication states.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








