Contents:
Uber Technologies, Inc., or Uber, is a San Francisco-based American mobility-as-a-service provider operating services in over 900 metropolitan regions worldwide. Its services include ride-hailing, food delivery (Uber Eats and Postmates), package delivery, couriers, freight transportation, electric bicycle and motorized scooter rental through a relationship with Lime, and ferry transportation in collaboration with local operators. Uber does not own any vehicles and instead earns a 25% fee on each booking. Fares are quoted to customers in advance, but they change depending on a dynamic pricing methodology based on local supply and demand at the time of booking.
What Happened?
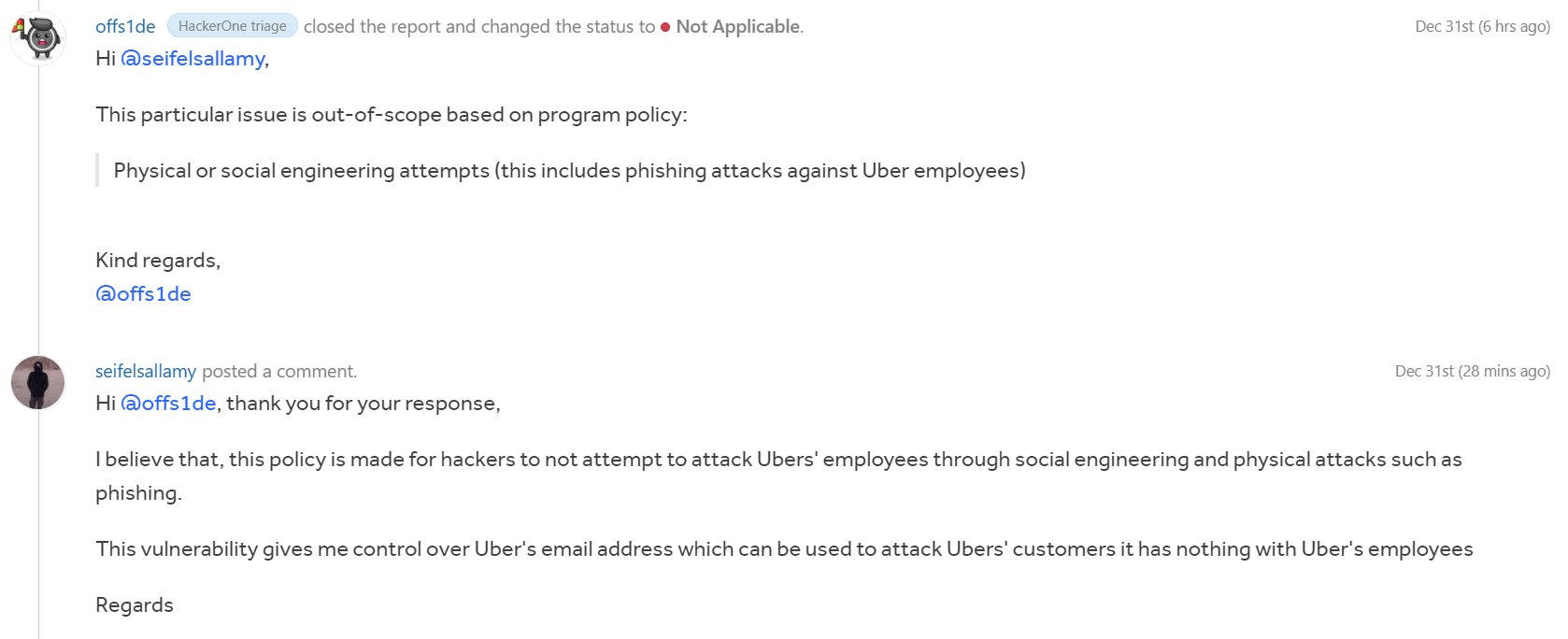
Seif Elsallamy, a security researcher and bug bounty hunter, uncovered a flaw in Uber’s systems that allows anybody to send emails on Uber’s behalf.
The researcher who discovered this flaw warns that threat actors might exploit it to send emails to the 57 million Uber customers and drivers whose information was exposed in a previous data breach.
These emails, sent from Uber’s servers, would appear authentic to an email provider, as they are in fact, and would pass through any spam filters.
Elsallamy forwarded an email that looked like it was from Uber to BleepingComputer.
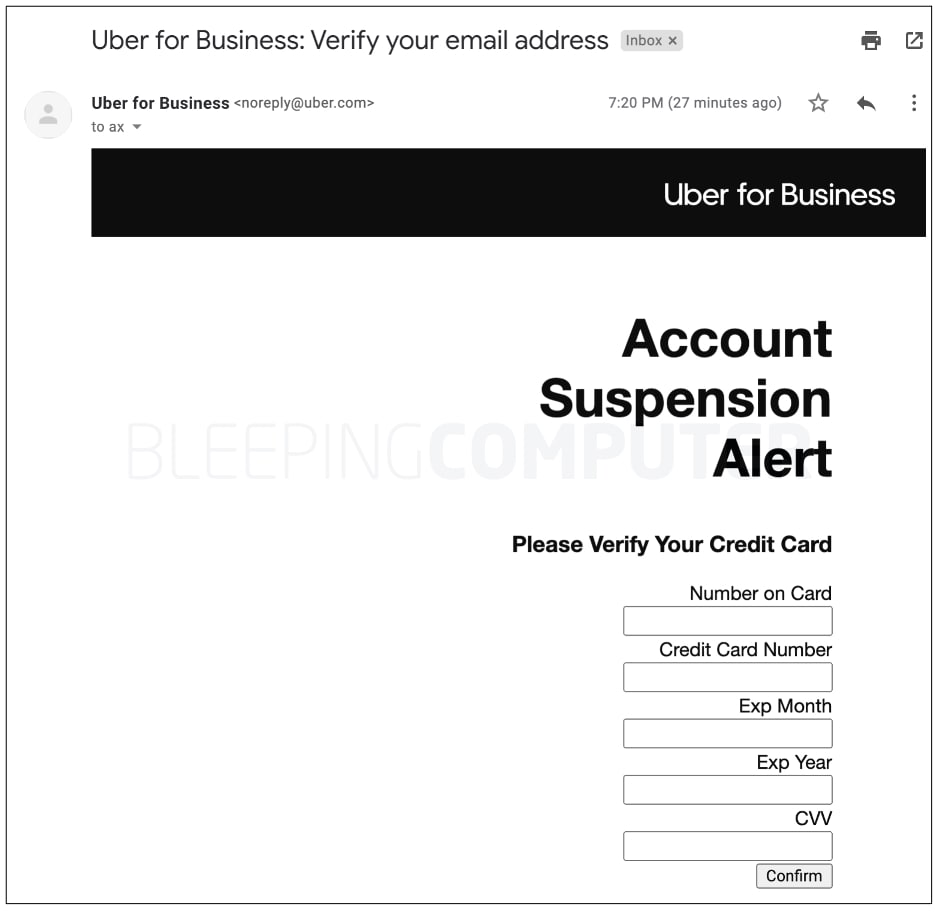
It’s worth noting that the email arrived in the inbox and prompted the Uber user to supply their credit card details. When you click ‘Confirm,’ the form sends the text fields to a test site that the researcher has set up.

The researcher responsibly submitted the vulnerability to Uber via their HackerOne bug bounty program, however, his report was rejected for being “out-of-scope,” based on the incorrect belief that exploiting the technical defect itself needed some type of social engineering.
Why Is the Vulnerability Concerning?
According to email headers the researcher’s email sent “from Uber” to BleepingComputer passed both DKIM and DMARC security tests.
The researcher’s email was sent using SendGrid, a renowned email marketing, and customer communications platform.
However, Elsallamy informed BleepingComputer that the flaw is caused by an exposed endpoint on Uber’s servers, which allows anybody to create an email on Uber’s behalf.
Hi @Uber @Uber_Support bring your calc and tell me what would be the result if this vulnerability has been used with the 57 million email address that has been leaked from the last data breach?
If you know the result then tell your employees in the bug bounty triage team. pic.twitter.com/f9yKIoCJ6O— SAFE ? (@0x21SAFE) December 31, 2021
How Can Heimdal™ Help?
Phishing it’s all around these days and you should take into consideration to protect your business with efficient tools like our E-Mail Fraud Prevention as well as Email Security. The first keeps Business Email Compromise (BEC) and CEO Fraud away through its 125 analysis vectors, effectively protecting your critical business assets and e-mail accounts. The second product combines proprietary e-mail threat prevention with Office 365 support to fight against threats delivered on the email.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security